Table of Contents:
Last updated on: April 17, 2023
Digital Risk Protection (DRP) is, in a nutshell, a systematic effort to protect the systems or networks of an organization from cyber threats and other types of digital risks.
DRP is designed to be preventive. For many cyber threats and digital risks, the damage was already done once they were identified, and in many cases, the damage is irreversible.
In today’s highly agile digital business environment, Digital Risk Protection is now crucial for any business looking to protect its digital assets and confidential information while minimizing potential downtime. Business owners can continue their effort to win customers’ attention and grow the business rather than needing to spend their time and resources tending to these digital risks.
In this guide, we will discuss all you need to know about Digital Risk Protection and why implementing it is important for your business.
By the end of this article, you’d have learned about the following:
First things first, what are ‘digital risks?”
We can define the term ‘digital risk’ as any threat (internal and external) that can potentially occur after the adoption of technology.
For example, when a business just launched a website, it may face the following digital risks:
With that being said, Digital Risk Protection (DRP) is the practice of identifying these digital risks, reducing the possibility of these risks, and mitigating any damage caused by the failure to manage these digital risks.
Each organization may deal with various forms of digital risks—both internal and external threats—and the introduction of any new technology solution may add new digital risks to the organization.
We can classify digital risks into eight major categories:
Let us discuss them one by one.
Whenever an organization adopts new technology, it may be at risk of not meeting the legal requirements that apply to the business.
For example, the California Consumer Privacy Act (CCPA) regulates US-based companies when collecting and storing consumers’ information. This should be a major consideration for the company when adopting and utilizing any technology solution. Similarly, an organization based in Spain or the UK will need to stay in compliance with GDPR.
Many industries also have specific regulations controlling how long data must be retained. The SEC, for example, has specific retention requirements that financial firms must stay compliant with.
A brand that violates data privacy laws or advertising regulations may suffer negative publicity and lose customer trust. This can lead to legal liabilities and damage to the brand’s reputation.
The risks related to external attacks by cybercriminals.
When adopting a new technology solution, there’s always the risk of any potential security vulnerabilities that can be exploited by hackers or cybercriminals, for example, the risk of potential malware infection.
There are various forms of cybersecurity threats lurking, with new threats being introduced on a daily basis. The most common types of cybersecurity threats include social engineering attacks (i.e., phishing your customers via a fake website impersonating your brand,) malware/ransomware infection, DDoS attacks, and SQL injection attacks, among others.
Organizations are legally required to protect their customers’ sensitive data information and will also need to protect the company’s confidential information to ensure competitive advantage and optimal day-to-day operations.
Any potential data breach or data leak is a serious data privacy risk for the organization.
This type of digital risk deals with the organization’s ability to protect sensitive, confidential, and/or regulated data, like customers’ personally identifiable information (PII) or credit card details. Fraudsters are especially likely to steal a person’s identity or commit fraud using their personal information.
Especially for organizations that collect customers’ sensitive data, it’s crucial to implement strict cybersecurity measures supported by adequate security infrastructure.
Online reputation risks refer to the potential damage to a brand’s reputation and credibility that may result from negative reviews and feedback, defamatory content, fake social media profiles, negative media coverage, or online harassment.
To mitigate online reputation risks, brands should monitor their online presence regularly, respond promptly to negative comments or feedback, and engage with customers proactively on social media and other online platforms.
Additionally, brands can implement reputation management strategies, such as search engine optimization (SEO) and online content marketing, to promote a positive image and build a strong online reputation.
Intellectual property risks are threats to a brand’s intellectual property rights, which include trademarks, copyrights, patents, and trade secrets. Risks can arise from competitors, employees, distributors, and customers. Common risks include trademark infringement, copyright infringement, patent infringement, and trade secret theft.
To mitigate these risks, brands can protect their intellectual property rights, implement internal policies and procedures to safeguard trade secrets, monitor their intellectual property regularly, and take legal action when necessary.
Referring to the use of techniques such as phishing, pretexting, baiting, and tailgating to trick customers into revealing confidential information or compromising security. These risks can result in data breaches, financial losses, and damage to reputation.
To reduce social engineering risks, brands should implement security protocols, train employees to recognize and respond to social engineering tactics, educate your customers to identify potential phishing attacks, and protect sensitive data and systems with multi-factor authentication, encryption, and other security measures.
As a result of the actions or vulnerabilities of suppliers or vendors, supply chain risks pose a threat to a brand’s operations, reputation, and finances. Risks can include unethical or illegal practices, poor quality control, patent or trade secret theft, and cyber attacks.
To reduce supply chain risks, brands should conduct careful investigation on their suppliers, create contracts and non-disclosure agreements that address supply chain risks, and regularly monitor and audit suppliers.
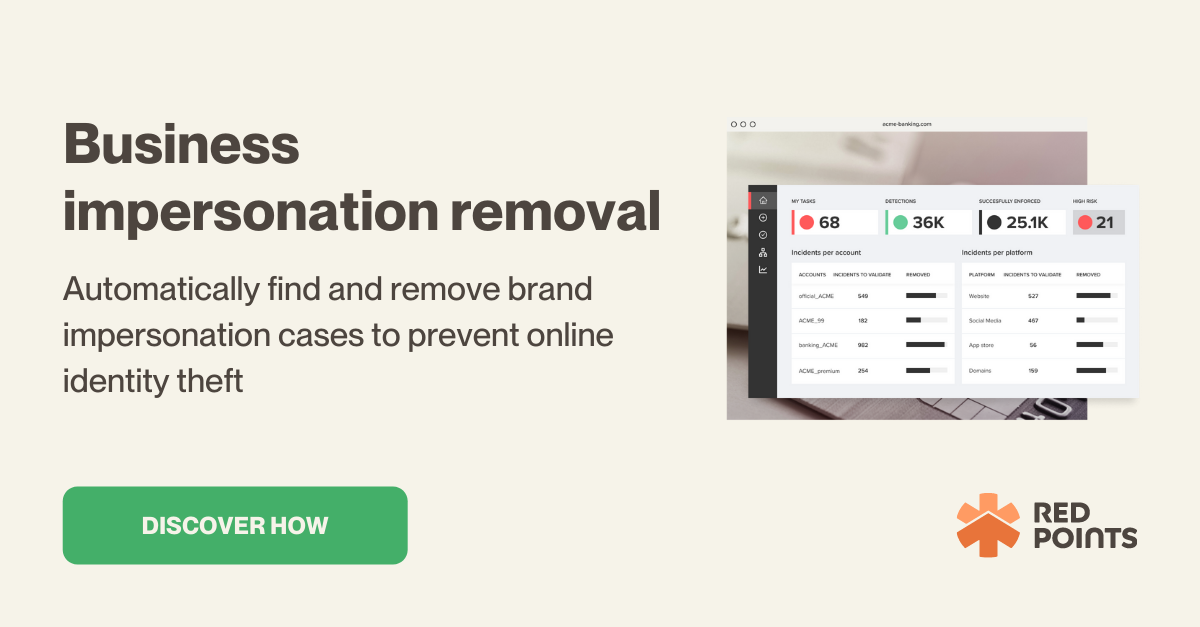
Maintaining a positive brand reputation should be a part of any DRP strategy, including proactively looking for brand abuses such as impersonations, trademark or copyright infringement, etc. Investing in an automated Brand Protection Software as your primary protection can be key to tackle these issues before they affect directly to your consumers and sales. .
Also regularly assess:
A key aspect of Digital Risk Protection is protecting the security and integrity of your company and your customers’ data.
The thing is, your and your customers’ systems, technology, and data are evolving rapidly, and your data security measures should also evolve accordingly.
Consider:
Conducting regular intellectual property (IP) audits is important for identifying potential infringement or unauthorized use of a brand’s IP assets, as well as identifying any gaps in IP registrations that may exist in certain regions or jurisdictions.
It is critical to register trademarks, copyrights, and patents in order to protect a brand’s intellectual property rights, and failure to do so can result in limited legal recourse against infringers.
All modern organizations now deal with at least three important external environments: customers, competitors, and regulations; all three are continuously and rapidly evolving at the moment.
An important element of DRP implementation is that it should not disrupt the evolving customer demands and compliance with regulations, while at the same time, shouldn’t hinder the organization in its quest to stay ahead of the competition.
When implementing and executing DRP, regularly assess the following:
Businesses can quickly identify any negative feedback or issues that need to be addressed by monitoring what is said about their brand online. They can also monitor brand sentiment, identify trends, and make informed marketing and product development decisions. Brands can automate this process by using tools like Google Alerts or Social Media Monitoring Software to stay on top of any mentions or impersonation across multiple platforms.
If a significant number of negative reviews mention issues with the product’s quality or authenticity, it could be a sign that counterfeit versions of the product are being sold online. Early detection of these problems allows brands to take action to remove the counterfeit listings or cooperate with law enforcement to halt the manufacture and distribution of counterfeit goods.
In today’s digital age, it is critical for brands to protect their online presence from digital risks. Failure to do so can have serious consequences, including reputational damage, loss of customer trust, and decreased business performance. As a result, it is essential to put best practices in place to mitigate them.
The most effective way for brands to protect themselves is to continuously monitor online mentions and reviews, perform intellectual property audits, and place security measures to prevent social engineering attacks. It’s also critical to keep up with compliance regulations and collaborate closely with partners and suppliers to ensure a secure supply chain.
If you are looking for an automated and streamlined process to protect your brand against the main digital risks, an Impersonation Removal Software like Red Points’ allows businesses to detect and remove fake profiles from online marketplaces, social media, and other digital channels. Book a 15 minute consultation and see how we can help.