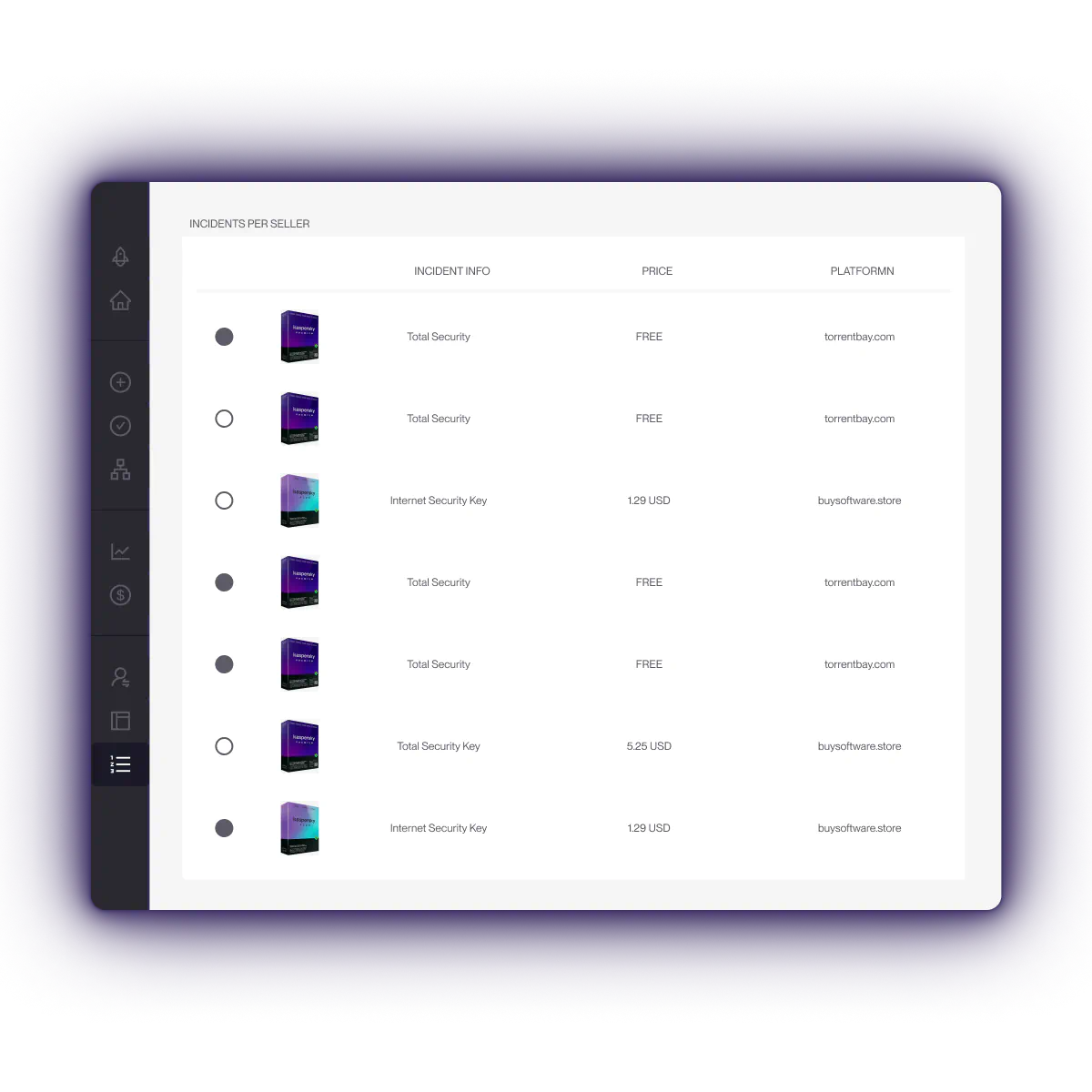
Counterfeiting
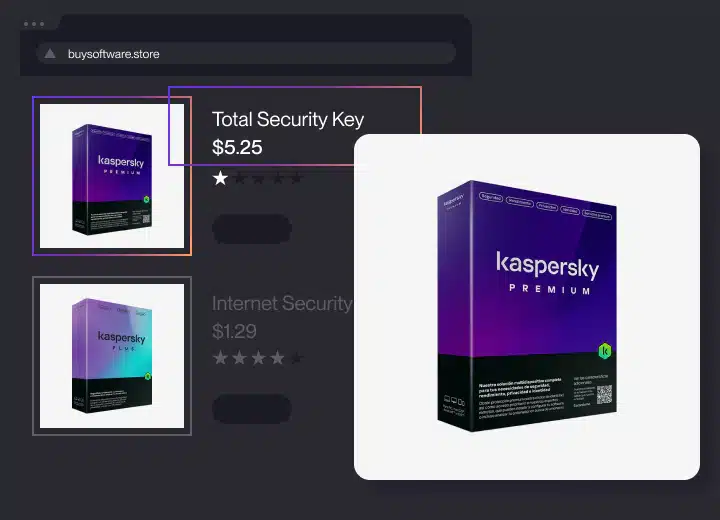
This involves the illegal copying, sale, and/or distribution of a copyrighted software with the intention of imitating the original product. For software programs, counterfeits come in different forms, including copies of compact disks with the software incorporated in them.
Other elements that are usually counterfeited include license agreements, packaging, security features, labels, and registration cards.
End-user piracy
This type of piracy involves the duplication of a software by an individual without authorization from the software company. There are many different types of end-user piracy, including:
Using a licensed copy for multiple installations on multiple computers
Benefitting from upgrades without having a licensed copy of the old version that’s being upgraded
Copying programs on discs with the intent of distributing or installing them
Getting a non-commercial, academic, or any other restricted software without the proper license
Changing discs outside or inside your workplace.
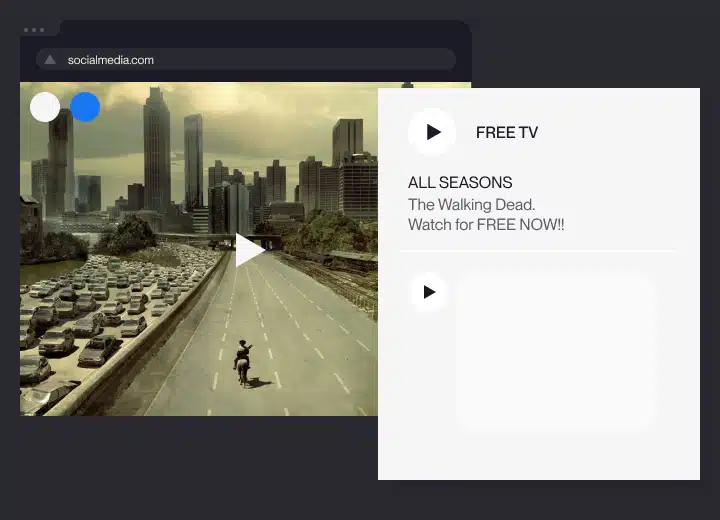
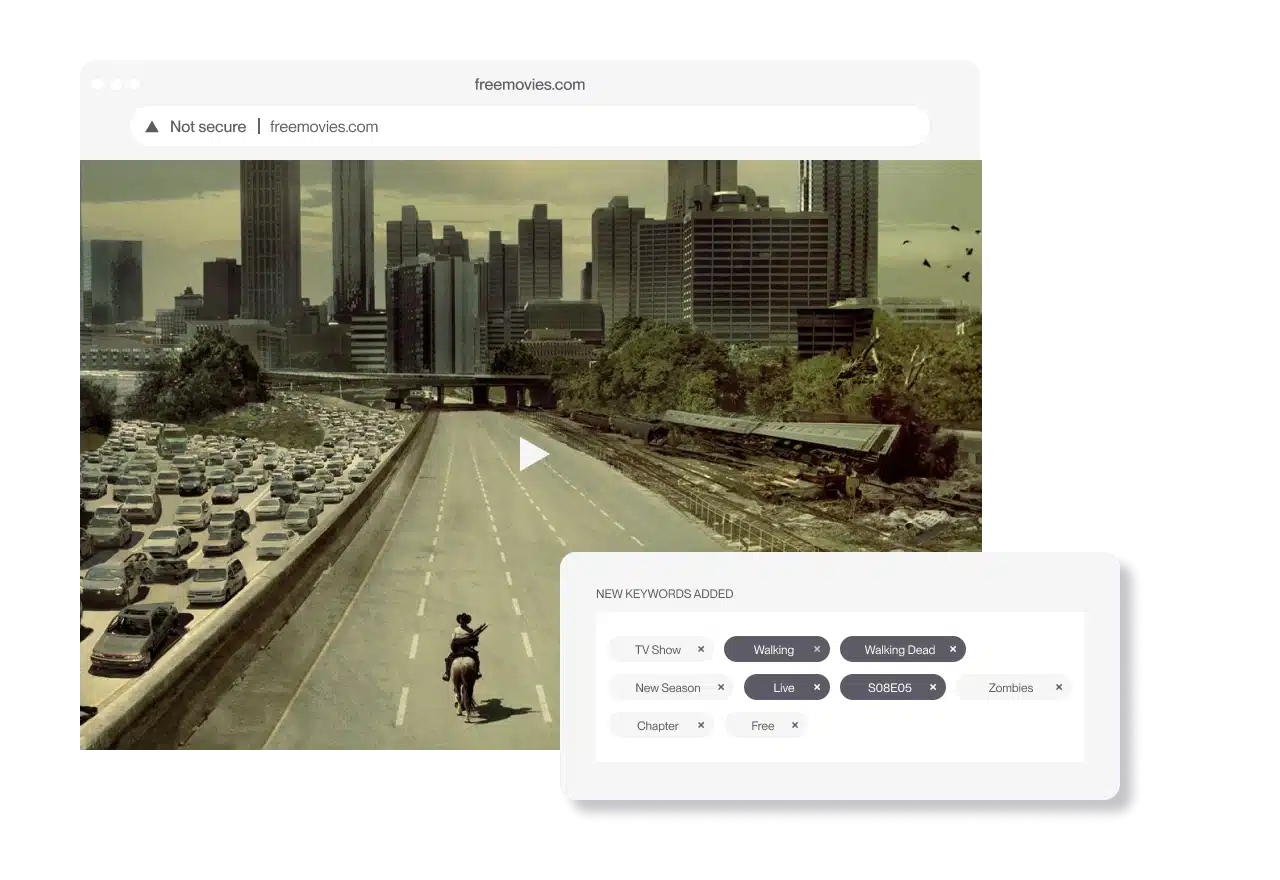
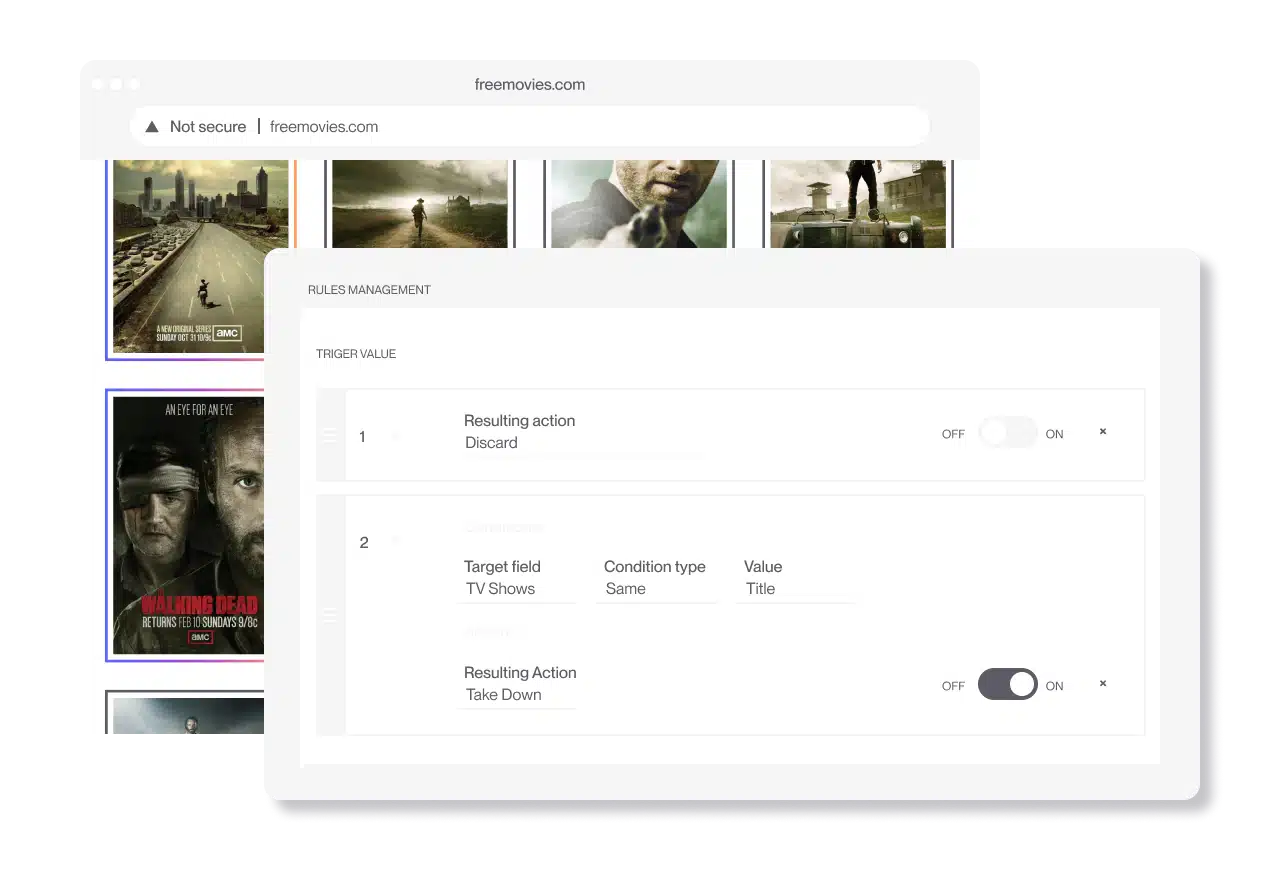
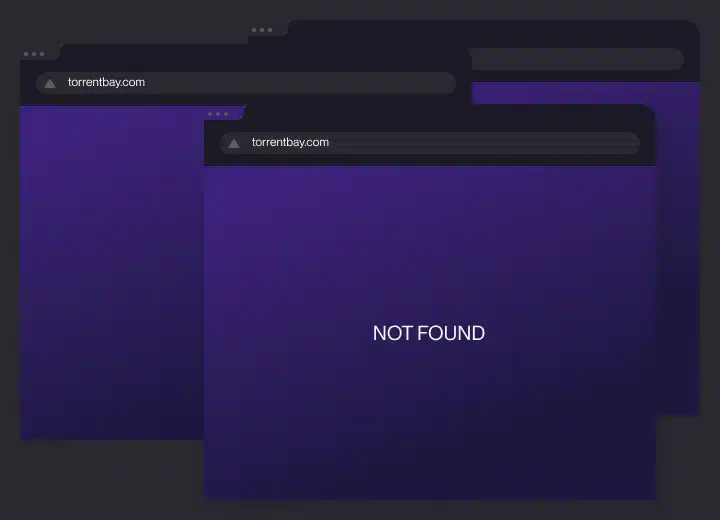
Internet piracy
A very widespread issue, internet piracy involves the copying of a software and uploading it on the internet.
Users who download pirated software from the internet are practicing internet piracy. Online software purchases follow the same rules as those bought in CD formats.
Some of the common internet piracy techniques include:
Internet auction websites that provide users with out-of-channel or counterfeit websites
Websites that exchange some software programs for others.
Websites that allow users to download software for free
Peer-to-peer networks that allow users to transfer copyrighted programs and pirated software without authorization.
Hard-disk loading
This is an act perpetuated by many computer sellers. Hard disk loading involves a business installing illegal copies of pirated software on the computers they are selling. They usually do this in order to make their offers more attractive to potential customers.
Client-server overuse
This piracy style involves the overuse of a central copy of a program on a particular network.
If you are someone who has a LAN, and you install software programs on this network for many people, you need to ensure that your license allows you to do so. With client-servier overuse, you are overusing and pirating the software if the number of users using the software are more than the number your software allows.