Fake Social Accounts
Make your profiles bullet proof
Stand-alone Websites
Take down
scammers
Lookalike
Apps
Remove apps impersonating you
Fake Social Accounts
Make your profiles bullet proof
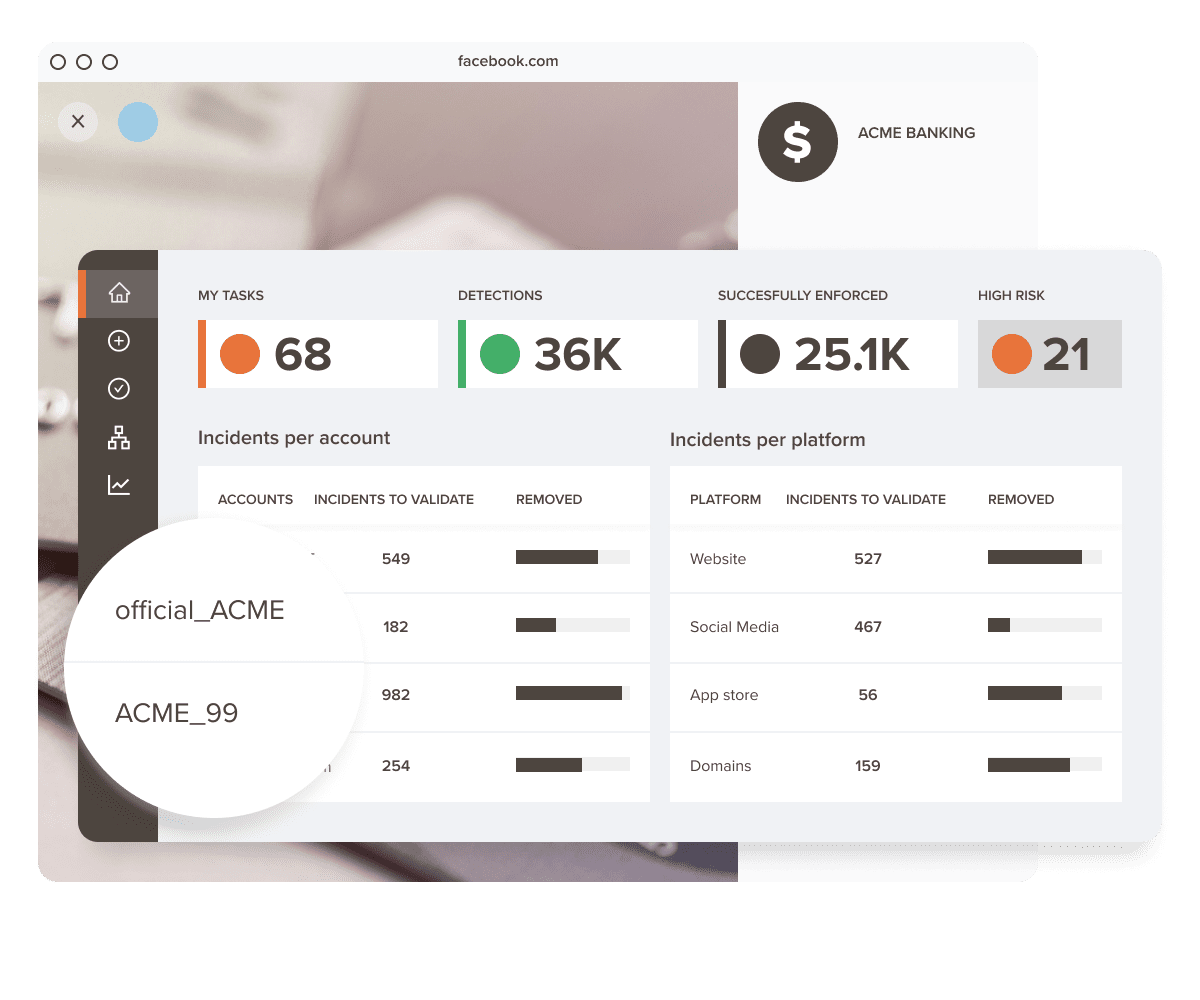
Discover accounts that are impersonating your brand 24/7
Review suspicious accounts and request takedowns or let our impersonation protection software do that for you automatically
Boost your search with machine learning that incorporates patterns and improves detection
Stand-alone Websites
Take down
scammers
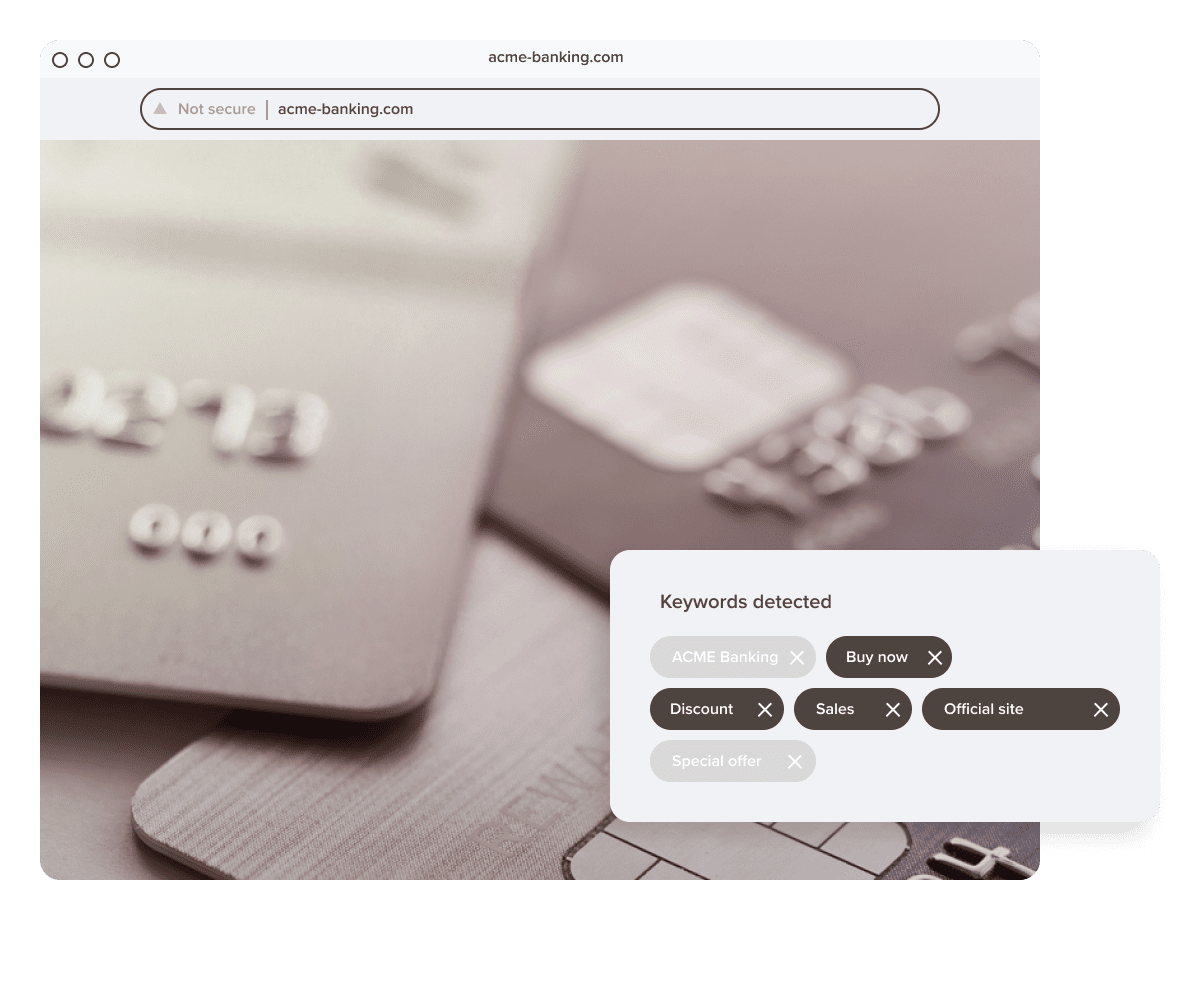
Uncover sites stealing your traffic and committing fraud under your brand name
Take down fake sites automatically and dissuade scammers from doing it again
Add new search opportunities seamlessly thanks to machine learning
Lookalike
Apps
Remove apps impersonating you
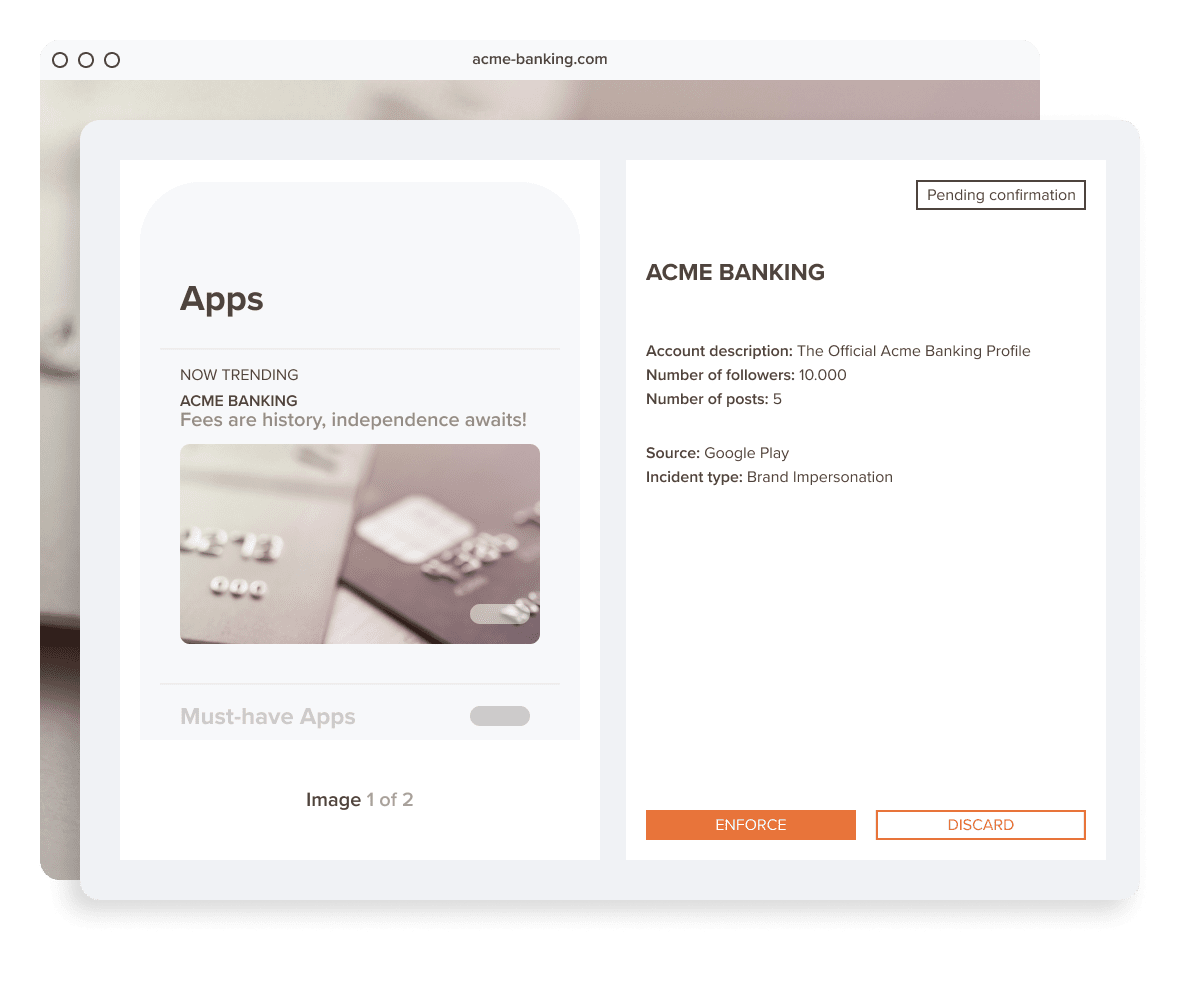
Identify apps that impersonate your brand fast through keyword search and photo analysis
Trigger takedown processes immediately on top app stores and APKs
Monitor links after enforcement to avoid playing whack-a-mole

Detect
Find impersonations in seconds with bot-powered search
Validate
Filter thousands of brand impersonation infringements by leveraging image recognition
Remove
Take down what puts your customers at risk automatically

Wei Zhang , Puma
Lawyers & General Counsel
Red Points’ impersonation protection software equips you with legal expertise and proactive strategies to effectively tackle impersonation attacks.

Ed Rainey, Knockaround
Revenue leaders
Our services safeguard your revenue streams by proactively preventing issues related to impersonation, which can otherwise divert potential customers.

Barbara Mora, FILA
Marketing teams
Our impersonation removal software helps marketing teams counter impersonation by monitoring and eliminating deceptive websites, fake social profiles, and more, safeguarding brand reputation.

Juan Salomon,
Security teams
Red Points’ impersonation software is a crucial tool, enabling early detection and swift removal of malicious scams. This proactive approach enhances overall cybersecurity defenses.
As a leading industry reporter, with over 4.6M enforcements per year in top platforms, we are official partners and have certifications with:
Google's Trusted Copyright Removal program
Youtube-Certified Multi-Channel Network
Josh L. General
Manager
Fantastic option for fighting copies of products!
Overall
Not only does it give us the confidence that copies of our products are being found and dealt with worldwide, but it has also enhanced our relationships with our distributors.
Pros
Red Points online dashboard is very simple to use and has strong back-end reporting. It is a very quick process to check daily and approve or remove potential copies of our products that they find. The customer service team is excellent even though they are in Europe and we are in New Zealand – has never been a problem for us. It has definitely helped us in our fight against copies worldwide and is great value for money….FAR cheaper than a lawyer!
Reasons for Switching to Red Points:
Cost initially. However over time we have seen Red Points has a fair quicker and greater reach than lawyers do.
Joe H.
Marketing & Engagement officer
Well-designed software that works with excellent customer support!
What do you like best?
The UI is clear, simple and well laid out so it’s easy to navigate. I was able to learn the software very quickly as well as roll out teaching to others with no issues. The algorithm really captured a great deal of matches after a short learning period and I was able to work through a large number of items easily thanks to the thorough setup. The customer support is also excellent, communicative and very helpful so we are able to get the most out of Redpoints.
Tobias B.
IPR Coordinator
Efficient removal of infringing listings!
What do you like best?
Red Points quickly and independently scans several platforms for infringing listings. What used to be a days work to search trough the platforms and report them is now done in minutes. The customer support is also great.
What is brand impersonation?
Brand impersonation is an act of pretending to be another person/ brand for the purpose of fraud and taking advantage of a position in the market.
Brand impersonation can be especially dangerous when customers are misled into sharing their personal information via social media messaging, email or web forms. Counterfeit goods are also sold very often from impersonated accounts and cloned websites, and consumers can be exposed to many other cybercrimes, so it is essential to implement impersonation protection techniques and tools.
What is an example of brand impersonation?
Brand impersonation comes in many forms, from phishing scams asking you to provide personal information to an outside account to full-blown online fraud where you buy products from shady sellers. All types of impersonation should be detected immediately to protect the reputation of your brand. Your business should use the best software to avoid impersonation for this purpose.
Here are some examples of common impersonation attacks:
How do you know if someone is impersonating your brand?
The easiest way to know if someone is impersonating your brand online is to search for your brand’s name online. The website, social media platform, or app will show you all the accounts using your name.
The first thing you can do to know if someone is impersonating your brand online is to search for your brand’s name on social media account lists, app stores, and search engines. However, very often impersonation is perpetrated in stand-alone rogue websites that are not indexed by search engines (i.e. the deep web) and that attract consumers via ads, banners, and social media posts. For those cases, impersonation protection software detection technology is required in order to effectively find out who is impersonating your brand.
How does brand impersonation protection software work?
When it comes to impersonation protection, early detection and removal are the most important steps.
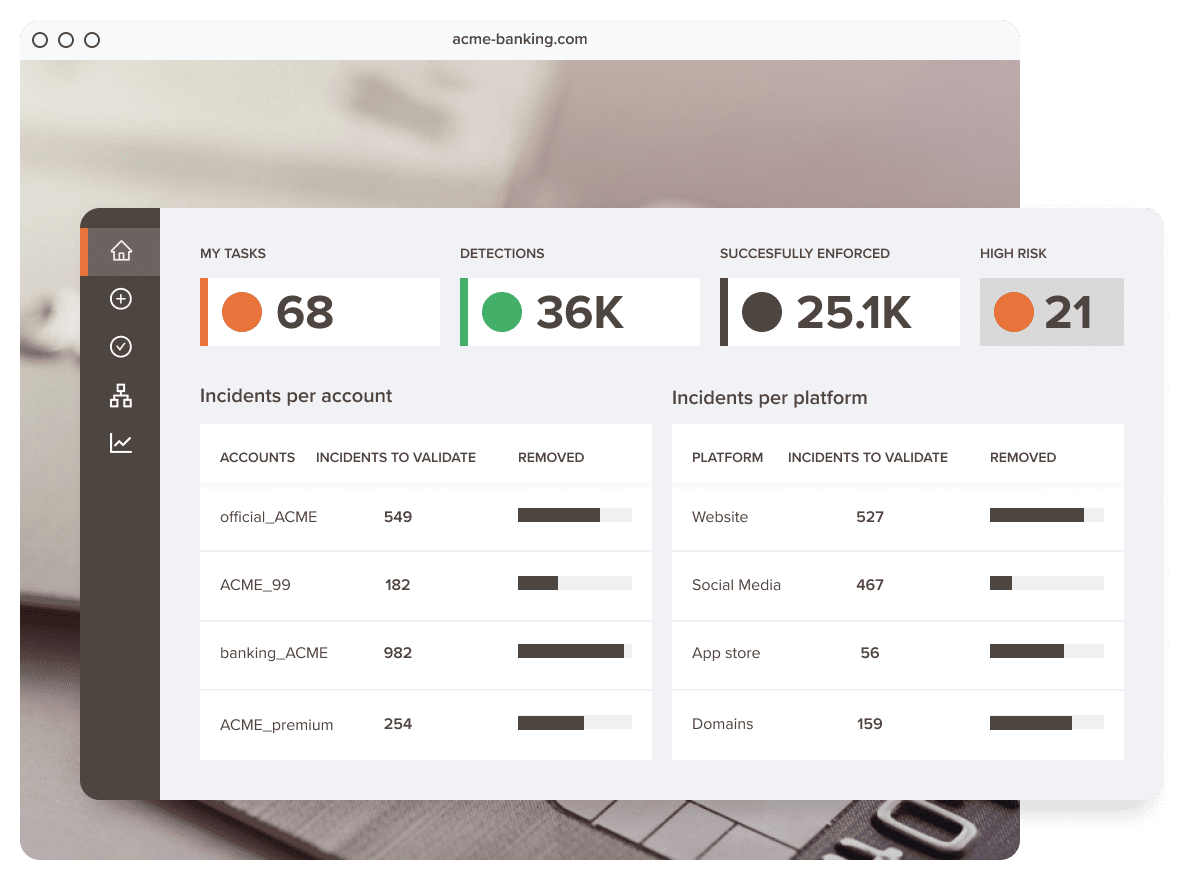
Red Points’ impersonation protection software offers the possibility of detecting, monitoring, and enforcing unauthorized profiles on social media, apps, websites, and domains that impersonate your brand’s official accounts.
All the potential infringements can be registered on Red Points’ impersonation protection platform so that brands can access it to check and analyze results, confirm the infringements and protect from brand impersonation in the future.
What are the causes for impersonation?
Impersonators can steal your content and upload it under a fake domain in a matter of minutes for several purposes:
Divert Traffic: Creating ads under the genuine brand name and stealing traffic
Sell Counterfeits: Using look-alike sites that mimic your official website
Commit Fraud: Creating phishing sites to steal users’ personal and financial information