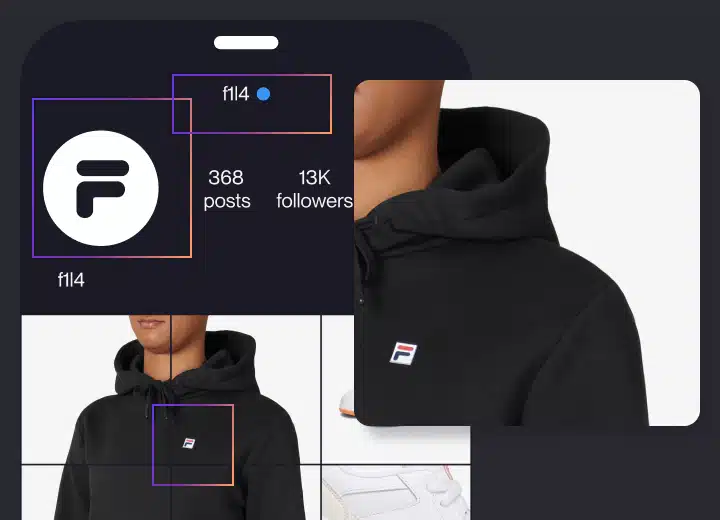
Using social media protection software is important for several key reasons:
1. Intellectual Property Protection: Social media platforms are bustling hubs for sharing content, which can make it easy for others to misuse or infringe upon your intellectual property rights. Social media protection software helps detect and mitigate such infringements, preserving the value of your creations and ideas.
2. Brand Reputation Management: Your brand’s reputation is a valuable asset. Social media protection software can monitor mentions, discussions, and user-generated content related to your brand, allowing you to promptly address negative comments, respond to customer concerns, and maintain a positive online image.
3. Content Control: By tracking and managing how your content is used and shared on social media, you can ensure that it aligns with your branding and messaging strategies. This control helps maintain consistency and authenticity in your online presence.
4. Legal Compliance: Many social media protection software tools assist in complying with legal requirements related to intellectual property rights. They can automate the process of sending takedown requests, which is essential for enforcing copyrights and trademarks.
5. Counteracting Impersonation: For businesses and public figures, social media security software can detect and prevent unauthorized accounts or profiles attempting to impersonate them. This helps in preventing scams, misinformation, and damage to your reputation.
6. Early Detection of Issues: Social media protection software continuously monitors online activities, allowing you to detect and address issues as they arise. This proactive approach minimizes potential damage and legal complications.
7. Efficient Resource Management: Instead of manually monitoring social media platforms, which can be time-consuming and labor-intensive, using software for social media protection streamlines the process and allows you to allocate resources more efficiently.
8. Data and Insights: These social media protection tools provide valuable data and insights about how your content is shared, who engages with it, and the impact of your online presence. This information can inform your marketing and content strategies.
9. Scalability: As your online presence grows, it becomes increasingly challenging to manage intellectual property and brand protection manually. Social media protection software offers scalable solutions that adapt to the size and complexity of your online footprint.
In conclusion, social media protection software is a crucial component of digital asset management and brand protection in today’s online landscape. It helps you maintain control over your intellectual property, respond to potential threats, and manage your brand’s reputation effectively, ultimately ensuring a positive and secure online presence.