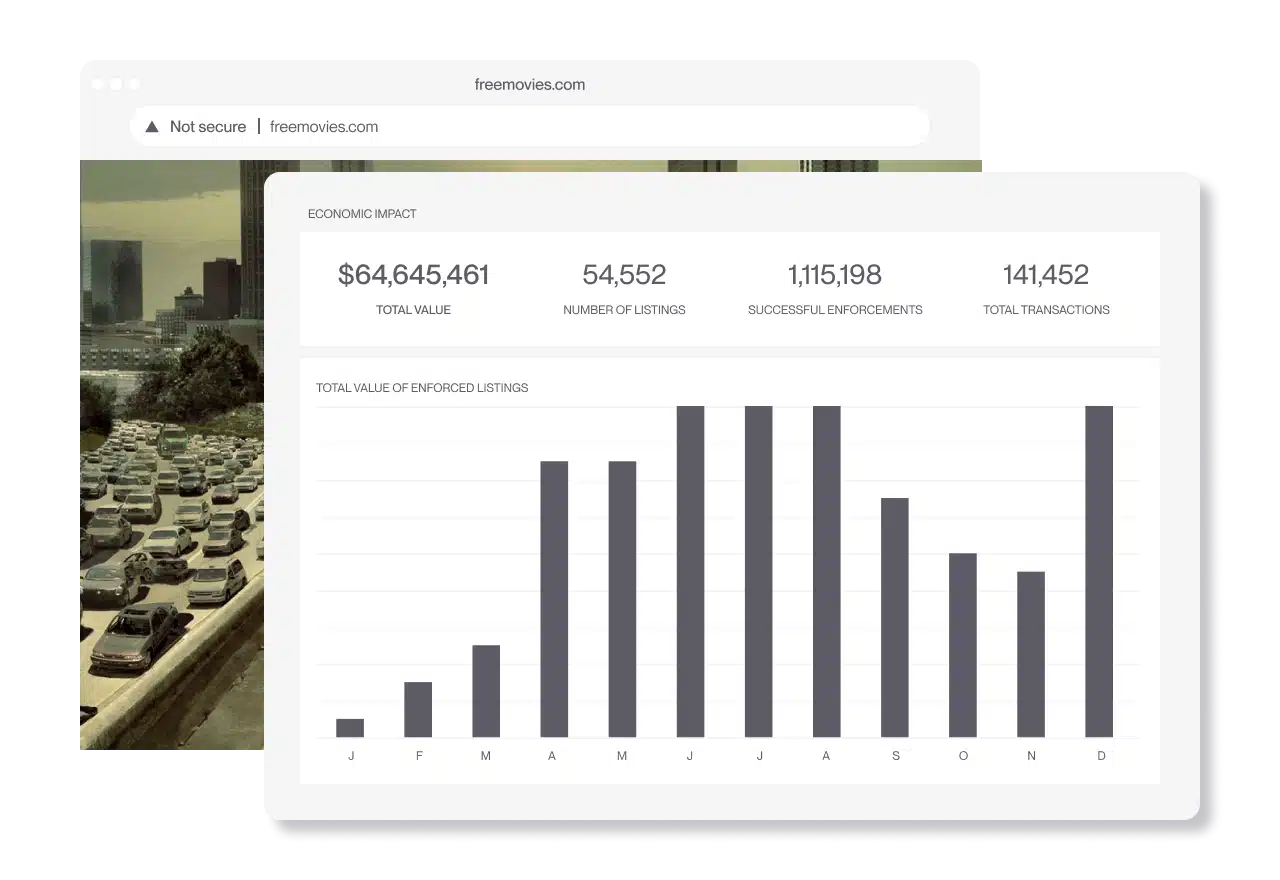
Software piracy has always been a pressing issue, but today, it’s escalating at a pace that no business should ignore.
Software piracy and unlicensed software use have continued to surge in recent years, with global losses estimated at up to $46 billion annually, according to the BSA. But the damage goes far beyond profits.
Pirated software undermines brand reputation, creates unfair competition, and erodes trust among partners and investors. As piracy tactics grow more sophisticated and spread across new platforms, stopping them requires a smarter, more proactive approach.
In this guide, we’ll break down what modern software piracy really looks like, and how to get ahead of it to protect your business.
The cost of software piracy for modern businesses
Software piracy doesn’t just steal a product. It affects every area of your business, hindering how much you earn, how you’re perceived by customers and investors, and how you grow.
Revenue loss
Software theft drains your business revenue well beyond a single lost sale. From leaked login credentials that bypass monthly payments to widespread sharing of unauthorized downloads, piracy erodes your long-term profitability and customer value.
Unfair competition
Pirated software listings crowd the market across search engines, social media platforms like Instagram and Facebook, and e-commerce marketplaces.
Wherever your customers search, counterfeit listings drive down your prices, bury your official products, and sabotage your advertising. If a pirate runs ads alongside yours, their cheaper, fake version often wins the click, costing you both revenue and return on your ad spend.
Piracy can also create unfair competition for users, especially in gaming, where users can illegally purchase high-level accounts, mods and hacks that interfere with game play. This diminishes the overall player experience and can put the game’s reputation at risk as it becomes overrun by modders.
Security risk
Pirated software poses serious security threats, both to the legitimate businesses who have had their software stolen, as well as users who download the software.
Users who download pirated software—whether knowingly, or thinking they are downloading the legitimate product—are also at risk for infecting their device with malware.
This malware can steal users passwords, banking details, and other sensitive information. Worse, it can compromise the security of the user’s entire system and network, which can wreak havoc on businesses if downloaded onto a company computer.
Reputational damage
Customers may be turned off by pirated versions of your software that leave them with a buggy product or malware, but the damage doesn’t end there.
For investors and potential partners, widespread piracy signals weak IP protection and long-term risk, which can limit and stall your business growth. Even after one instance of software piracy, your customers, partners, and distributors may choose to take their business to competitors who appear less risky.
Higher operational costs
Piracy drains internal resources far beyond enforcement. When users unknowingly purchase pirated software, your team will be left fielding and investigating complaints, verifying licenses, and repairing trust.
Your customer support team will need to answer questions and provide assistance to disappointed customers who unknowingly downloaded the pirated version of your product. Prioritizing these duped customers will put a strain on your team’s usual day-to-day responsibilities and can quickly drain resources.
Legal teams will need to pursue takedowns while customer support handles confusion and frustration, and sales teams face pricing pressure from unauthorized sellers.
Without a proactive approach, each area of your business will face time consuming, costly hurdles, diverting your time, budget, and energy away from growth.
Most common types of modern software piracy
There are different forms of piracy for just about every kind of software on the market. From unauthorized resellers to credential-sharing schemes, these methods allow users to bypass licenses and access paid products for free, or at a steep discount.
Understanding the most common tactics is the first step toward effective protection.
Unauthorized distribution
Involves reselling or distributing software license keys, or installation files without your permission.
These unauthorized copies can appear on third-party websites, legitimate marketplaces, social media, and messaging platforms, and video platforms, posing as official or discount versions.
Illegal downloads
Pirated software is frequently uploaded to torrent sites, file-sharing platforms, and peer-to-peer (P2P) networks after hacker modification to bypass activation, licensing, and security features.
These cracked versions give users full access without paying, and unlike unauthorized resales, the software itself is illegally duplicated or altered.
Credential sharing
A growing form of piracy involving the unauthorized sharing of logins or session cookies via resale platforms and private groups. This form of piracy often involves streaming services, e-learning platforms, and video games.
An emerging form of credential sharing in the gaming world involves selling high-level accounts loaded with rare items or achievements, undermining both revenue models and gameplay fairness. These tactics violate terms of service and are difficult to track, yet they significantly impact monetization and user experience.
How pirated software is distributed in 2026
Software piracy is more accessible today than ever, both for pirates and those actively seeking free or unauthorized versions of paid software.
From cyberlockers and torrent networks to listings on marketplaces and invite-only groups on social platforms, pirated software is everywhere. Add in generative AI and search engines, and finding pirated software has never been easier.
Free vs. monetized piracy
Piracy today splits into two broad categories: free and monetized piracy. Each type uses different platforms, keywords, and languages, meaning enforcement strategies must adapt accordingly.
- Free piracy – Involves pirates sharing unauthorized downloads, login credentials and other pirated content, both on public sites and hidden in private groups and forums. Scammers may share free pirated content in order to gain more followers on social media, or to funnel traffic toward future scams or paid listings.
- Monetized piracy – Involves directly profiting from pirated content. Cracked software, resold licenses, and stolen accounts are sold across traditional marketplaces, specialized platforms, social media, advertisements, and underground sites.
Key distribution methods
Pirated software, account credentials, and unauthorized downloads are distributed and found via a wide range of channels, making identification and enforcement challenging. These methods include:
- Cyberlockers – Hosting cracked software behind download links that are often shared across forums or private chats.
- Specialized piracy sites – Entire websites dedicated to offering cracked, modded, or unauthorized software.
- Torrents and peer-to-peer networks – Common for distributing large software packages and unlocked apps.
- Traditional marketplaces – Cracked plug-ins, modded games, login credentials, and cookie/session files are commonly sold on reseller sites and third-party marketplaces, from eBay to Alibaba.
- Specialized marketplaces – Niche platforms like Steam for pirated games and G2A for software keys often host pirated or resold licenses and accounts.
- Social media – Pirates can promote cracked software and logins via posts, comments, and even paid ads across Facebook, Instagram, and other social platforms. Private groups can also serve as hard-to-track locations for distributing pirated content.
- Forums – Public forums like Reddit, as well as invite-only communities on platforms like Discord, are frequently used to share pirated software, login credentials, and tips for finding pirated content and bypassing licensing systems.
- Messaging apps – Encrypted apps like Telegram and WhatsApp can be used to share pirated content in closed groups and one-on-one chats, often behind paywalls to evade detection.
- Search engines – Users may discover pirated versions of your product through online searches, often using misspellings or code words that lead them to unauthorized copies.
- Video platforms – Videos, such as YouTube and TikTok tutorials, demonstrate how to install or unlock pirated software and often link to download sources in the description.
- Spreadsheets – A method spreading in popularity recently, influencers and micro-influencers share curated lists of sellers and products via spreadsheets, linking to pirated versions of the software.
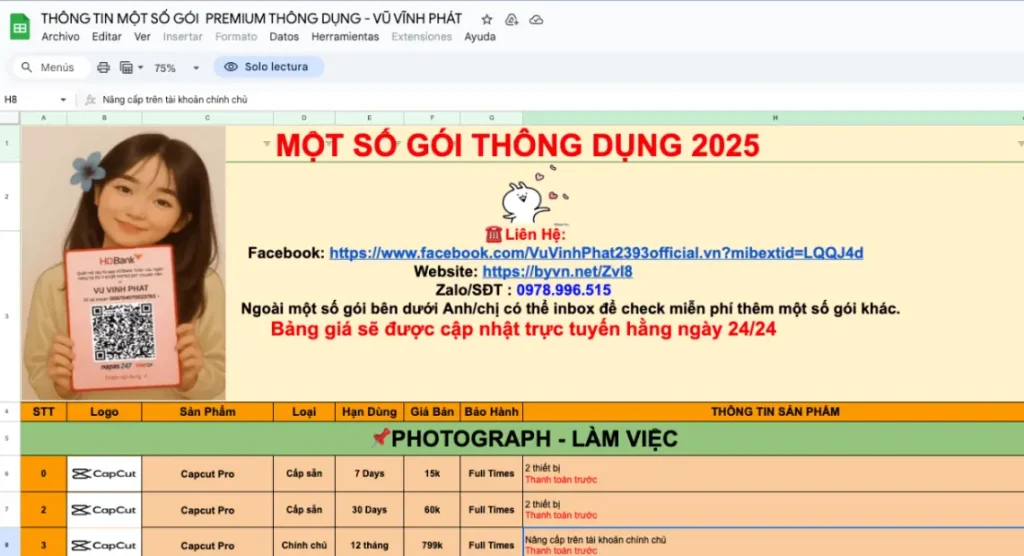
What makes modern piracy so hard to stop
Modern software piracy is widespread, and increasingly built to avoid detection. Here are three of the leading reasons it’s become harder than ever to track and remove:
Piracy hidden behind closed doors
In addition to easily identifiable public listings on marketplaces, a growing amount of piracy often happens out of view. Software pirates hide behind closed forums, invite-only Discord and Telegram groups, and platforms protected by logins.
These private channels make it extremely difficult to detect, access, and enforce against infringing content without specialized tools or tactics.
Generative AI
With the help of ChatGPT and other AI tools pirates can obscure and distribute pirated content faster and easier than ever. Generative AI can be used to easily code and create new websites and generate new but similar domain names when one is taken down.
Evasive keywords and language
Software pirates rarely use obvious keywords in their fraudulent listings. They rely on code words, misspellings, and obscure language to bypass the basic filters and enforcement tools used in traditional monitoring systems.
Scale and speed
Piracy moves fast, spreading across thousands of platforms and listings, often faster than teams can respond. The moment one listing is removed, several more often appear in its place, creating a never-ending monitoring and enforcement cycle.
How Red Points helps companies fight back
Modern software piracy isn’t just hard to take down—it’s hard to find in the first place. It hides in private Telegram groups, invite-only Discord servers, and obscure forums. Pirates often use vague keywords, deliberate misspellings, or even coded language to keep their listings under the radar.
Manual methods just aren’t enough to keep your product protected across the thousands of channels where piracy could be putting you at risk. That’s where Red Points comes in.
Combining human expertise with industry-leading AI, Red Points detects and removes software piracy at scale, even in the hardest-to-find places where traditional tools fall short. Here’s how:
Advanced keyword strategies for better detection
Red Points uses smart detection to uncover even the most evasive forms of software piracy. Each strategy starts with expert analysts who design tailored keyword sets based on your product, industry, and risk areas. These include core detection terms, multilingual variations, and common evasion tactics.
Then, Red Points’ technology expands these keywords, adapting by channel type and boosting searches for faster, more accurate identification of piracy wherever it occurs.
With continuous optimization and advanced pattern recognition, Red Points keeps your protection up to date and highly effective, no matter how piracy evolves.
Comprehensive coverage
With advanced AI detection that identifies threats worldwide, across various platforms, and in multiple languages, Red Points can detect piracy no matter where it occurs.
You’ll get 24/7 monitoring and unlimited takedowns across indexed and non-indexed sites, social media, video platforms, cyberlockers, and marketplaces. Red Points’ experts are always in the loop with new trends and evasion techniques, so your product will be protected even as pirating evolves.
Automated, prioritized enforcement that scales
Red Points doesn’t just find piracy, it helps you act on it fast. Using automated takedown tools, real-time analytics, and enforcement rules tailored to your business priorities, you can focus on stopping the threats that do the most damage.
Combined with visual dashboards, reporting, and feedback with real analysts, you get broad coverage and deep insight into what’s happening with your brand.
What’s next
The threat of software piracy isn’t slowing down. It’s adapting, spreading faster, and becoming harder to detect. A proactive, tailored strategy is essential to stay ahead of these evolving threats and protect your business.
Red Points combines expert strategy, human oversight, and advanced automated technology to combat piracy at scale, protecting your revenue and brand reputation 24/7.
Schedule a demo to learn how Red Points can detect hidden piracy and stop threats before they spread.