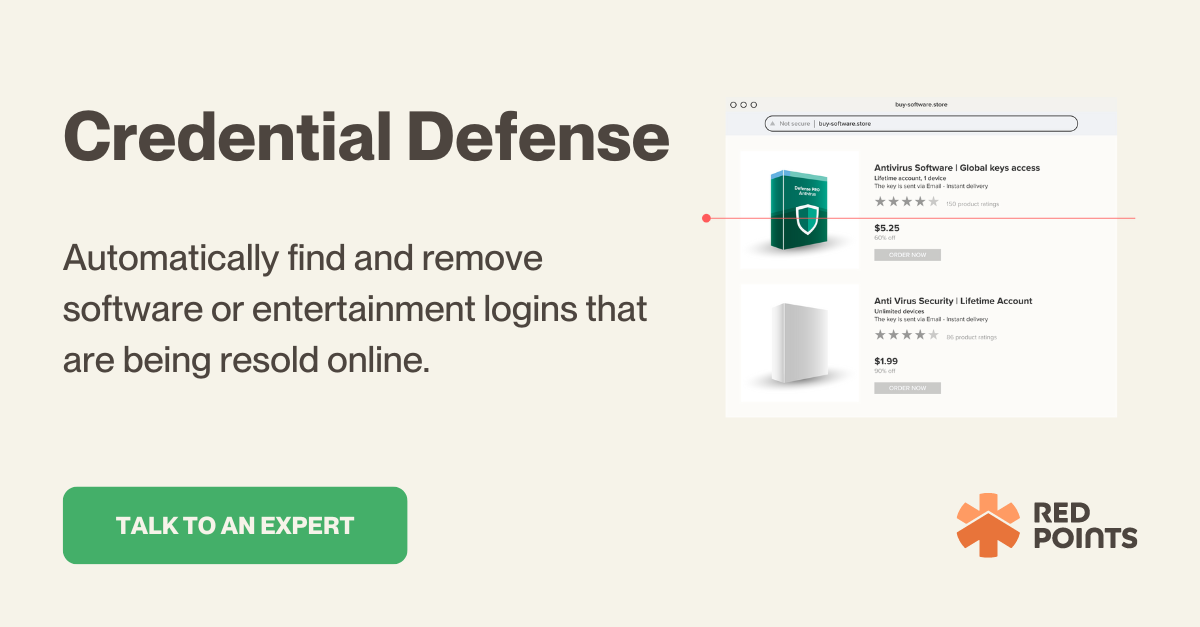
There is a wide variety of website credential sharing services available. Some services claim to allow user credentials to be shared free of charge while other services require the user to pay for downloading the credentials in order to access over-the-top (OTT) platforms.
Credential sharing is clearly an indication that either full or partial access credentials have been leaked. It is probable that in both cases, the credentials have already been used multiple times by different users. In this article, we’ll explain why credential sharing is a worrying trend in the OTT market that threatens the viability of many providers and how they can detect and prevent it.
Summary:
- Several OTT platforms have seen huge growth since the start of the pandemic.
- This has also led to the emergence of parallel activities where access to platforms is traded in an unauthorized way.
- Credential sharing (a.k.a. credential sharing, credential selling) can occur on social networks, closed groups, and marketplaces.
- Credential sharing can be an opportunity for businesses to create new subscribers.
- Detecting illegal credential sharing is possible using specialized software.
- Preventative measures include introducing multi-factor authentication.
OTT subscriptions on the rise
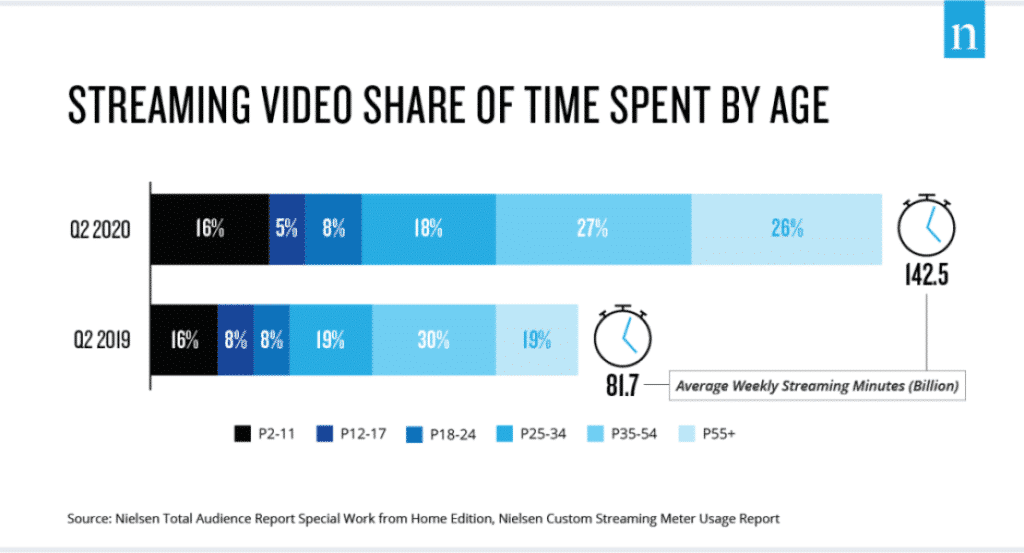
Over the past months, home confinement has led to a spike in television consumption hours and video consumption rates as well as an increase in access to video platforms such as YouTube.
The pandemic has also digitalized a large segment of the population who, prior to confinement, were unfamiliar with new technologies, social networks, online content consumption, and video communication. A recent study conducted by Nielsen in the United States shows not only the increase in streaming minutes consumed but also how new-age groups have been impacted by this new trend.
What is credential sharing?
Credential sharing is the practice of using someone else’s digital identity to gain access to a platform. One example of credential sharing is providing another person with one’s credentials in exchange for payment, and then signing in using their credentials. In some instances, customers will share their credentials with 3rd party resellers, and these resellers can combine multiple platforms into a bundle of services.
Can users share credentials?
In its user agreement, each platform explicitly defines what can and cannot be done. Though most people don’t tend to read it, this document outlines whether a user can share credentials with a family member, for example.
It also specifies the prohibition to sell access to the platform to third parties. Though most people may share their credentials with friends and family members, it can also be done maliciously. This is when credentials are stolen and sold on marketplaces or given away on social networks, for example.
Generally speaking, there are two types of credential sharing:
Occasional sharing:
This is when someone shares credentials with friends and family, and generally does so without any economic exchange and without the purpose of earning money. Usually, it is done within the immediate family group. This type of “credential sharing” is well regarded or socially accepted.
Illegal sharing:
In many cases, the credentials of thousands of users are exchanged with the explicit aim of generating income from their sales and/or distribution. Passwords are then sold on marketplaces at a much lower price than the monthly subscription cost. The descriptions often offer guarantees and lifetime credentials.
To avoid negative comments in the offer listing, contact telephone numbers or email addresses are listed. This type of “credential sharing” directly violates the terms and conditions of the service that every user agrees to when signing up and starting the subscription.
Conclusion
The entire digital ecosystem, ranging from social networks and video platforms to marketplaces, implements its own policies in order to report this type of infringement. This ensures they can be taken down and the economic damage to the rights owners can be avoided.
However, the burden remains on the right holders to identify these infringing cases across the internet. Red Points’ expertise in the anti-piracy space coupled with our state-of-the-art detection and enforcement technology makes it possible to provide a comprehensive credential protection service.
Check our Credential Defense platform for more information on how we can automatically find and remove software or entertainment logins that are being resold online.