Everyone loves a deal. But when a premium software subscription is selling for the price of a coffee, what are you actually buying?
To find out, the Red Points Anti-Piracy team went undercover. We didn’t use complex coding or dark web tactics. We simply acted like average internet users searching for well-known brands, using terms like [Brand + Subscription / Brand + Pro, Brand + Prime]. We cover services like AI tools, anti-virus, productivity apps, design, and streaming services across 14 different marketplaces in 8 countries: China, Malaysia, Philippines, Thailand, Indonesia, Ecuador, Mexico, and Poland.
We wanted to know: How easy is it to find pirated services? Do they actually work?
The results of our 60 test purchases revealed a sophisticated, global business ecosystem and a minefield for consumers. Here is what happened when we hit “Buy.”
One in five pirated transactions ends in a complete scam
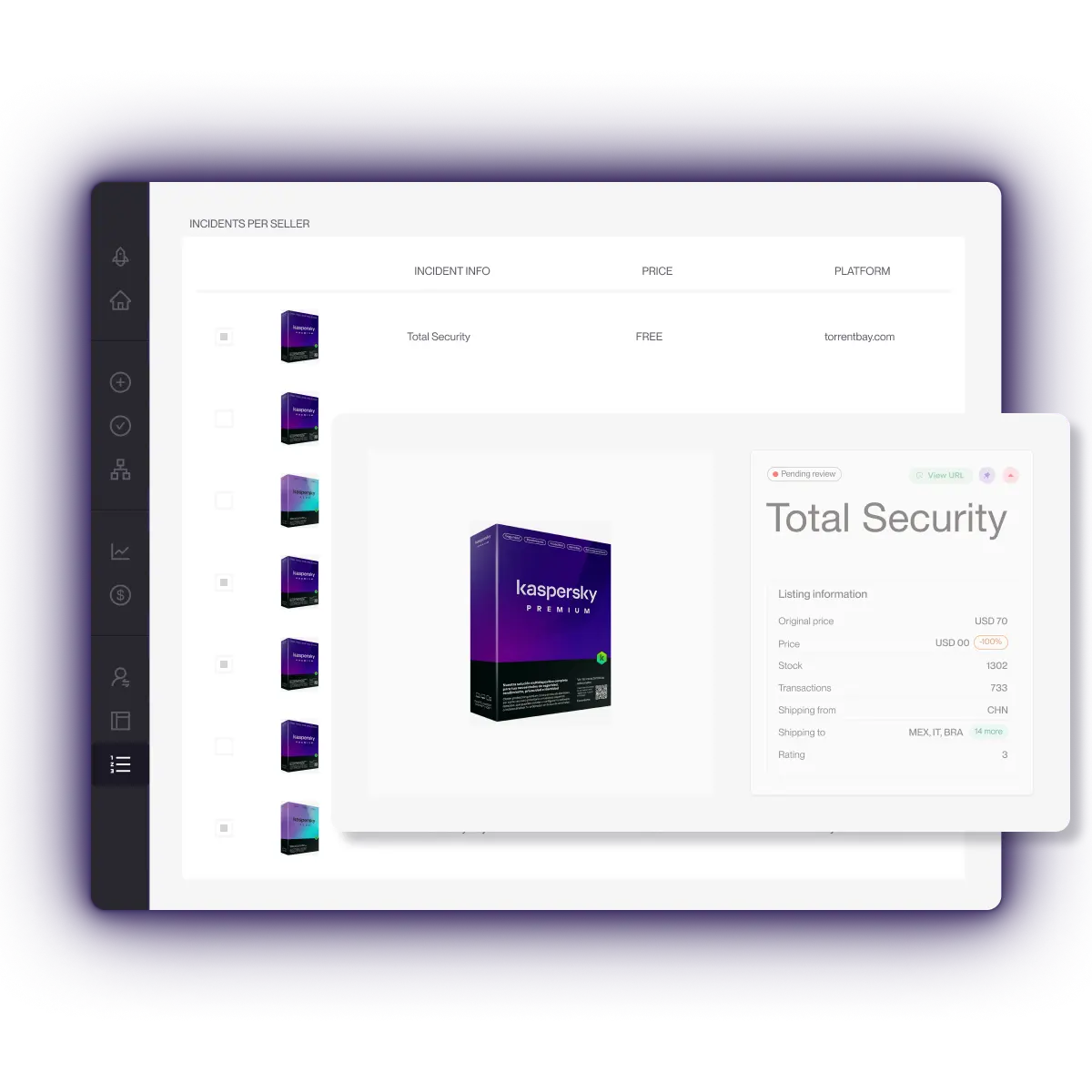
The first thing we noticed was the price. The average cost of the pirated products we analyzed was just $4.66, representing a massive 44% discount off the retail price. In some cases, specifically in Southeast Asian marketplaces, we saw subscriptions selling for 98% off.
But that low price tag comes with a high “hidden” cost.
Our data showed that 21.7% of these transactions failed completely. In more than 1 out of every 5 purchases, the buyer received nothing. Sellers ghosted us, canceled orders after taking payment, or sent “verification codes” that never arrived.
The dangerous journey from marketplace to encrypted chat
When the transaction didn’t fail outright, it often took a turn toward the dangerous.
To evade marketplace detection, many sellers forced the conversation off-platform. We were frequently directed to encrypted messaging apps like WhatsApp, Telegram, or WeChat to complete the process. Once outside the safety of the marketplace, buyers are stripped of refund rights and often pressured to share personal data, opening the door to phishing and identity theft.
Even the “working” products carried heavy risks. Instead of official downloads, we were often sent shady activation codes or “installer files” of uncertain origin. These unverified files are prime vehicles for malware and ransomware, putting the user’s entire device at risk.
How the pirated subscription business model actually works
Perhaps the most striking finding was that these weren’t isolated hackers. We found that sellers across different continents used identical, repeatable strategies to monetize stolen access. Piracy has become a standardized, scalable business.
Here are the four main tactics we uncovered:
1. The “Family Plan” exploit: Sellers abuse family or group subscriptions (designed for households) by selling individual slots to strangers. If the platform detects the anomaly, the innocent buyer loses access instantly.
2. Shared credentials: A low-tech but common method where a seller shares one login (email and password) with multiple buyers via a spreadsheet, often imposing strict time limits to avoid triggering usage caps.
3. Regional arbitrage: Pirates take advantage of lower software prices in specific regions (like Southeast Asia) to resell credentials globally at a markup, undercutting official prices in the West.
4. The “Middleman” platform: In the most sophisticated setups, we didn’t log into the official app at all. Instead, sellers directed us to third-party, merchant-operated platforms that acted as a bridge to the service. This allows the pirate to manage thousands of sessions while insulating themselves from the official provider.
The 18 billion dollar problem brands cannot ignore
You might think consumers know the risks when they buy cheap software. But our research suggests otherwise. When these illegitimate products inevitably fail, or the accounts get banned, the frustration is rarely directed at the anonymous pirate.
Instead, consumers blame the legitimate brand.
The reputational damage is compounded by real economic loss. In 2024 alone, piracy websites received over 216 billion visits, contributing to an estimated $18.7 billion in lost revenue for the software industry.
The takeaway
Piracy is not fragmented; it is organized, consistent, and dangerous.
For brands, understanding these distribution channels is the first step toward shutting them down. Our investigation proves that by approaching piracy from the buyer’s perspective, companies can uncover the networks exploiting their IP and protect their customers from fraud.
Is your software being sold for $4.66 on the open market? Don’t wait for the bad reviews to roll in. Request a demo to see how Red Points can detect and remove unauthorized listings before they damage your brand.