How to stop software piracy? It’s an important question, and the answer is complicated. Copyright protection systems aren’t foolproof. Even when using copyrights and patents, content owners still deal with a lot of problems from software piracy.
In 2018, the Business Software Alliance estimated that 37% of all software installed on personal computers was unlicensed, which translated to $46.3 billion in lost revenue. BitTorrent, the most popular file sharing website, accounted for 22% of global upload bandwidth in 2018, according to Sandvine. That shows how much people are interested in pirating content.
Global stay-at-home orders due to COVID-19 made the issue of software piracy worse, as well.
Copyright infringement can come in the form of counterfeit programs, client server overuse, internet piracy on torrent indexing sites, and software license or product key circumvention. Once a product is copied, people can use the technique of hard disk loading to add pirated software programs to computers they sell and entice buyers. All of it affects copyright holders. We’ll go over a few ways companies can prevent software piracy here.
Summary:
- Copyrights, patents, and user agreements form the legal basis for fighting online piracy
- A wide range of tools exist to combat piracy, like tamperproofing, obfuscation, watermarking, and product keys
5 ways to prevent piracy
A few main ways to prevent piracy include:
- Copyrights, patents, and end user agreements
- Software product keys
- Obfuscation
- Tamper-proof software
- Software watermarking
Copyrights, patents, and end user agreements
Software can be protected by copyrights and patents. These create a legal basis for businesses to protect their intellectual property and electronic inventions. End user agreements further define what a customer is allowed to do with a piece of software.
As the name indicates, purchasers are considered users and not owners. Agreements spell out what people can and can’t do with the software. Namely, they can’t copy it illegally or share it with more users than their license allows. Of course, people still do these things, which is where the rest of the anti-piracy techniques come in.
Software product keys
Software product keys are unique for each purchaser. The software won’t run or install unless the user types in the key. The goal with product keys is to decrease end-user piracy, since people who intend to distribute locked software can generate keys with their own codes. A hardware-locked software key is one of the strongest types, since the key is based on the user’s individual computer.
Obfuscation
Obfuscation is the technique of making a product’s source code unintelligible to humans. Complex algorithms can change software code to disguise it as something else or appear random. However, obfuscation isn’t a completely foolproof solution, as an attacker can uncover the source code with enough time. For that reason, obfuscation is often used in conjunction with the next technique on our list, tamper-proofing.
Tamper-proof software
Tamper-proof software is designed to be protected against modification and reverse engineering. If an attacker changes part of the source code, the program will shut down or malfunction. Attackers tamper with a piece of software to get around authentication, disable security monitoring, or bypass the license code to make illegal copies.
Software watermarking
Software owners can also include a watermark within the source code. This watermark is hidden within the software and can prove ownership or origin of the program when it’s extracted. This traceability can discourage thieves from making illegal copies. On a similar note, forensic watermarking is a new technology to prevent movie piracy, thanks to recent advances in blockchain development. It’s done by slightly changing certain pixel colors in a video file, which are imperceptible to the human eye. This also traces ownership of the product.
Also read:
How to take down a fake website
How to fight back against software piracy
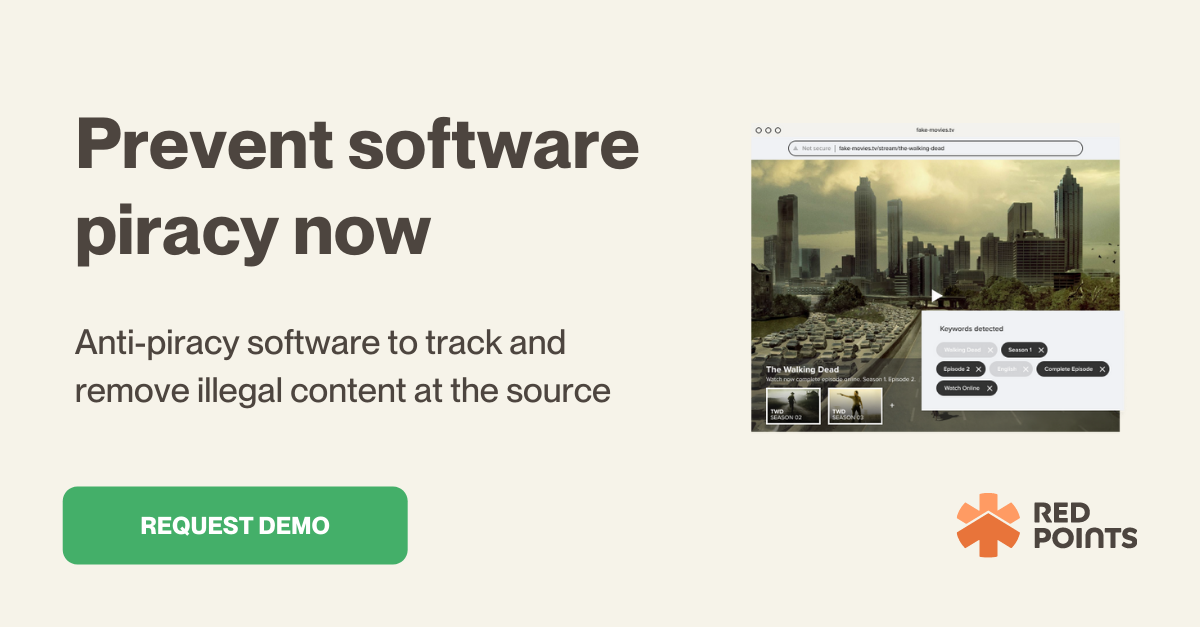
So far, we’ve talked about anti-piracy techniques used at the time of software creation. But whatever techniques you use at that point, there’s always the chance that people can crack your defenses with enough time. That’s where Red Points comes in. Our anti-piracy software scan hot spots of piracy on the net and take down copyright violations.
Software pirates love to use outlets like linking sites, cyberlockers, P2P platforms, and apps to disseminate pirated content. Red Points’ bot-powered search crawls these locations and more to locate the source of the problem. Then, you can send automated deindex and removal requests based on your rules. Our experts are available to pursue actions further, as well.
You can view your progress in an easy-to-use dashboard that shows the total detections, success rate, and more so you can measure your ROI. Ultimately, stopping piracy is going to have a positive impact on your company’s bottom line and encourage more users to purchase legitimate programs or licenses. Check out our piracy solution for more information.