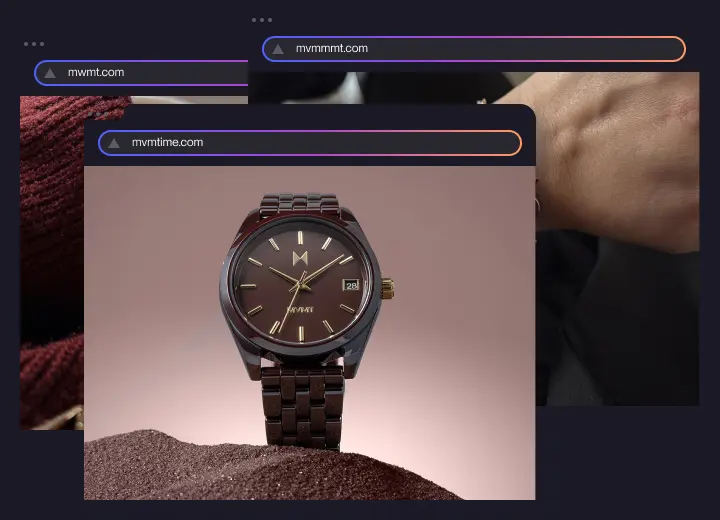
Picture this. A customer scrolling through Instagram sees an ad using your logo, brand colors, and product images. The offer looks legitimate. They click, buy, and never receive the product. Within hours, customer support tickets spike and negative reviews appear. At the same time, similar ads and marketplace listings continue to spread across platforms, all using your logo to look authentic.
This scenario is no longer anecdotal. It is systemic.
According to the OECD’s Mapping Global Trade in Fakes 2025 report, counterfeit and pirated goods now account for approximately $467 billion in global trade, representing 2.3% of worldwide imports.
In 2026, logo misuse detection is therefore not a narrow trademark enforcement task. It is a revenue, trust, and customer safety risk amplified by AI-generated imagery and platform scale. This guide explains how brand monitoring tools detect logo misuse, why legacy approaches fail, and how brands operationalize protection at scale across platforms such as Amazon, TikTok, and Instagram.
What is logo misuse detection?
Logo misuse detection is the continuous identification of unauthorized or misleading use of a brand’s logos and visual assets across digital channels, including marketplaces, social media, ads, websites, and domains.Its purpose is to prevent impersonation, fraud, and counterfeit sales that divert revenue and damage customer trust at scale.
This is where modern brand monitoring tools, such as Red Points, become essential. Red Points applies computer vision, logo recognition, image hashing, and OCR to detect brand assets visually, not just textually, enabling coverage that manual methods cannot reach.
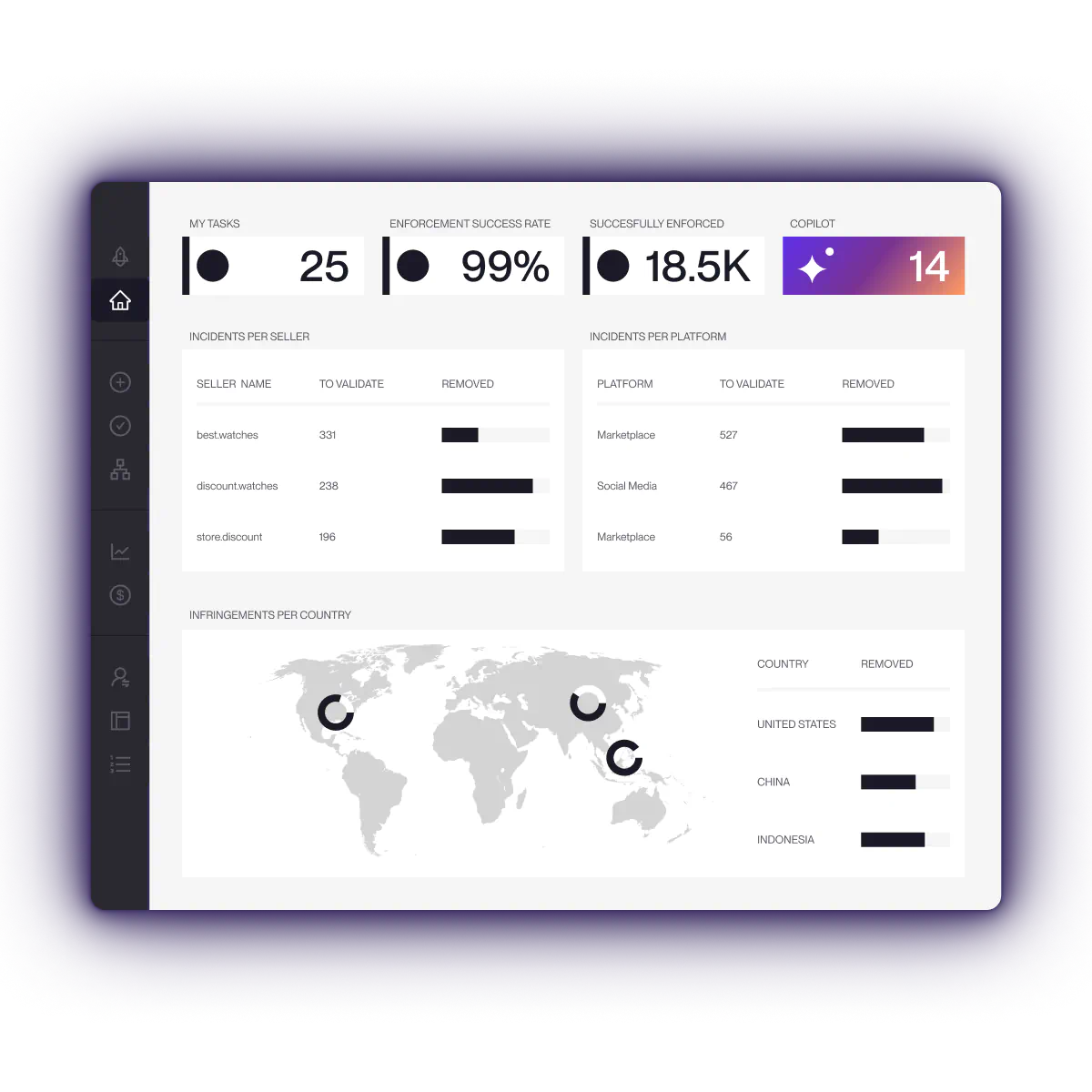
At scale, automation is essential to surface logo misuse across millions of images, videos, and listings. However, human expertise remains critical for high-risk and ambiguous cases. Red Points’ detection models are refined through over a decade of enforcement operations, informed by activity across 1,300+ brands and millions of enforcement actions per year. Dedicated enforcement and operations teams review escalated incidents, validate complex edge cases, and continuously retrain detection logic based on real platform responses. This human-in-the-loop approach ensures that automation drives scale, while expert oversight protects accuracy, reduces false positives, and aligns enforcement decisions with platform and brand risk thresholds.
From a business perspective, logo misuse detection protects three critical areas. It prevents revenue leakage caused by diverted sales and price erosion. It preserves customer trust by stopping deceptive experiences before customers are harmed. And it protects traffic and media efficiency by removing fake ads and listings that compete with official channels.
The expanding threat landscape in 2026
Logo misuse is accelerating because impersonation tactics now scale faster than ever before. Consumer advice charity Advance Direct Scotland found that an AI scam can go live in under two minutes. Short-lived campaigns, rapid asset generation, and automated relisting allow misuse to spread in hours rather than days, increasing customer exposure and commercial risk before manual action is possible.
The OECD reports that online channels are now the fastest-growing vector for counterfeit distribution, particularly where enforcement lag allows visual impersonation to remain live long enough to complete full conversion cycles.
Generative AI and the speed of fraud
Generative AI has dramatically increased the speed and volume of logo misuse by lowering the effort required to create convincing impersonation assets. Bad actors now generate synthetic product images, ads, and storefront visuals that embed brand logos naturally, bypassing keyword-based monitoring.
In practice, a single actor can launch dozens of visually unique listings or ads within 24 hours, each using logo variations designed to evade manual review. Without automated computer vision, many of these assets remain live long enough to exhaust ad spend and mislead customers.
Brand monitoring tools must therefore rely on logo recognition models, perceptual image hashing, and OCR, rather than text alone. Red Points uses these techniques to detect logos even when partially obscured, recolored, rotated, or embedded in complex imagery.
Marketplace sprawl and repeat offender velocity
Marketplace logo misuse is no longer driven by isolated listings, but by coordinated seller activity that relists at speed across multiple accounts. On platforms like Amazon, eBay, and Temu, sellers can relist products rapidly using reused visual assets and new accounts.
Manual enforcement treats each listing as a standalone event. The result is predictable. Repeat infringers often relist within 48 to 72 hours after a takedown if the underlying actor is not identified.
Red Points addresses this through seller risk scoring and actor network analysis, connecting listings, accounts, and assets to expose coordinated logo misuse. This allows brands to disrupt repeat offenders rather than chasing individual listings.
Social impersonation and ad-driven misuse
On social platforms, logo misuse is increasingly driven by paid ads that redirect users to spoofed websites and disappear quickly. These campaigns are intentionally short-lived. Ads often run for hours, not days, before accounts are abandoned.
Red Points combines ad monitoring with automated extraction of hidden destination URLs, enabling enforcement to target not only the ad, but the connected website and associated domains. On supported platforms, this reduces detection-to-takedown timelines from multiple days to 24-48 hours, materially limiting customer exposure.
Manual protection vs automated protection
Manual logo misuse protection cannot scale to the volume, speed, or platform diversity of modern impersonation threats. Automated detection and enforcement are required to monitor millions of assets continuously, prioritize high-risk incidents, and reduce detection-to-takedown timelines from weeks to hours.
Automated brand monitoring tools change this dynamic. Red Points provides always-on logo detection across millions of images and ads, prioritizes incidents using risk signals, and executes enforcement through platform-specific APIs. Detection-to-takedown timelines shift from weeks to hours or under 24 hours on high-volume platforms.
The difference is operational. Manual processes are linear. Red Points-driven automation is exponential. Manual coverage is limited. Automated monitoring scales globally. Red Points operates on a flat-fee, unlimited takedown model, removing volume-based cost penalties.
Importantly, Red Points does not eliminate human judgment. High-risk or ambiguous cases are reviewed by experts, ensuring 99%+ accuracy while maintaining scale.
Step-by-step guide to logo misuse protection
Logo misuse protection requires a structured, repeatable workflow that combines visual detection, strategic enforcement, risk prioritization, and expert validation. Using Red Points’ Brand Protection Platform, brands can move from reactive takedowns to continuous, scalable protection across marketplaces, social media, ads, websites, and domains.
Step 1: Inventory and map brand assets into detection models
Start by identifying and structuring all brand assets that require protection. This includes registered logos, legacy marks, sub-brands, and commonly misused product images. During onboarding, these assets are mapped directly into Red Points’ platform, enabling logo recognition, image fingerprinting, and OCR-based detection. A complete asset inventory reduces detection gaps and minimizes false positives from legitimate use.
Step 2: Establish IP and enforcement readiness
Confirm that trademarks and copyrighted assets are registered and connected to platform-specific enforcement programs such as marketplace brand registries. Red Points centralizes IP documentation through its Document Repository, allowing enforcement workflows to trigger automatically when infringement is detected. This step ensures incidents can move directly from detection to enforcement without manual rights verification delays.
Step 3: Activate always-on visual detection across channels
Enable continuous monitoring across marketplaces, social media, ads, websites, and domains. Red Points’ Vision AI and broad search analyze logos and product images embedded in listings, ads, and page layouts, not just keywords or domain names. This approach surfaces impersonation that would otherwise bypass text-based monitoring, including resized, recolored, or partially obscured logos.
Step 4: Prioritize risk using predictive signals and expert validation
Not all incidents carry equal commercial risk. Red Points applies Seller Risk Score, Actor Networks, and AI Incident Prediction to prioritize repeat offenders, coordinated networks, and high-exposure misuse. High-risk or ambiguous incidents are escalated to Managed Services and enforcement experts for validation, ensuring accuracy while maintaining scale and avoiding unnecessary disruption to legitimate sellers.
Step 5: Enforce through automated workflows and optimize continuously
Submit takedowns using platform-specific APIs, automated enforcement rules, and priority reporting paths. Track outcomes such as removals, relisting behavior, and enforcement success rates directly in the platform. Red Points’ closed feedback loop uses real enforcement responses to retrain detection models, refine rules, and reduce recurrence over time.
Implementation plan – first 90 days
The first 90 days of logo misuse protection should focus on establishing visibility, automating enforcement, and disrupting repeat abuse. A phased approach enables brands to baseline exposure, remove high-volume misuse quickly, and refine prioritization based on real enforcement outcomes.
Days 1–30: Audit & Baseline In the first 30 days, brands complete asset inventory (including legacy logos), configure detection rules, and establish baseline misuse metrics within the Red Points platform. This phase focuses on mapping exposure before launching enforcement.
Days 31–60: Enforce & Automate Between days 31 and 60, automated logo misuse enforcement launches on high-volume platforms. This typically delivers immediate impact, as clusters of infringing listings and ads are removed in bulk via API connections.
Days 61–90: Optimize & Disrupt From days 61 to 90, brands analyze repeat misuse patterns, refine prioritization, and escalate complex cases with expert validation, shifting from reactive cleanup to sustained control.
Real-world use case
Global brands facing logo misuse increasingly see fake websites appear faster than customers can report them, leading directly to payment fraud and trust erosion. Burton, a global sporting goods brand, encountered thousands of scam websites impersonating its brand, using copied logos, layouts, and product images to appear legitimate and expose customers to stolen payment details.
Problem
Burton saw a surge in fake websites posing as official brand stores. Customers were unknowingly entering payment details on scam domains or purchasing products that never arrived. These sites frequently reused Burton’s branding and product images, making them difficult for customers to distinguish from legitimate stores. Manual searches surfaced threats only after harm occurred, while new domains appeared as quickly as old ones were removed.
Solution
Burton deployed Red Points’ automated fake website detection using instant URL triggers, AI-driven pattern recognition, and predictive risk scoring. Obvious impersonation domains were flagged and enforced automatically, while machine-learning models identified disguised copycat sites by analyzing copied layouts, pricing signals, and reused product images, even when the brand name was not present in the URL. Human experts validated high-risk cases and continuously refined detection rules to improve accuracy.
Result
Within the program’s first phase, Burton removed 4,600+ fraudulent websites, prevented over 5,000 fraudulent transactions, and shifted from reactive enforcement to proactive protection. Scam-related customer complaints declined, enforcement accuracy improved by more than 40%, and internal teams reduced time spent on manual review while maintaining customer trust.
Actionable insights
- Inventory all logo variants, including legacy designs.
- Prioritize platforms where logos appear in ads, not just product listings.
- Use automation for scale, but retain human oversight for high-risk cases.
- Treat logo misuse detection as a permanent operational function.
Frequently asked questions
Why is logo misuse detection important in 2026?
Because AI-driven impersonation allows misuse to scale faster than manual monitoring, directly impacting revenue and trust.
Can brand monitoring tools detect logo misuse automatically?
Yes. Platforms like Red Points use image recognition and computer vision to detect logos across images, ads, and listings, identifying even modified or cropped variants. Modern tools use computer vision, image hashing, and OCR to detect logos across images, ads, and listings.
Can this be done manually?
Manual detection works only at low volumes. At scale, with millions of new listings created daily, it becomes slow, costly, and ineffective.
Which platforms should brands monitor first?
High-traffic marketplaces and social ad platforms such as Amazon, TikTok, Instagram, and Facebook.
How long do logo misuse takedowns typically take?
With Red Points’ automated workflows, takedowns often occur within 24 to 48 hours rather than days or weeks.