Bank fraud is the false impersonation of a bank or other financial institution in order to obtain money, assets, or other property owned or held by a financial institution, or to obtain money from depositors.
According to several jurisdictions, bank fraud refers to actions that use a scheme or artifice, rather than bank robbery or theft. However, the specific features of specific banking fraud statutes differ. Bank fraud is therefore sometimes called a white-collar crime for this reason.
In this article, we talk about what is impersonation in banking, what constitutes bank impersonation scams, and how best to combat this problem.
What are bank impersonation scams?
A bank impersonation scam occurs when a fraudster poses as a representative from a financial institution in order to deceive a victim into making payments to a fictitious account.
Bank impersonation scams examples
1. In most cases, a fraudster will contact their victim by phone, but they may also use email or another form of communication. It’s possible that they already know the victim’s name and where they bank.
Faking a bank employee, the fraudster may claim that a customer’s account is in jeopardy and that they must transfer funds to a “safe account” or set up automatic withdrawals in order to “stop the funds.”
There is a possibility that a fraudster will ask for Digipass information so that they can gain access to the account and make payments themselves.
2. They may ask the victim to install screen-sharing software so they can monitor or control the machine. An account can be more easily managed if this is done.
3. E-mail that looks to come from a well-known institution, such as banks or well-known websites, can be used to phish. For your protection, please be aware that banks will never ask you to divulge sensitive information such as your login and transaction password or One Time Password (OTP).
Phishing using an email that appears to originate from someone in your organization, your supervisor, or a close relative is called spear-phishing. It is a targeted attempt to steal sensitive information. In many cases, the subject line address is tailored to a specific project or development within the organization, or it could refer to a personal occasion.
When a person opens an email and clicks on a link connected to it, a violation has occurred. In a matter of seconds, a Trojan horse or other malicious software is downloaded or a form appears on the recipient’s computer screen, requiring them to enter their personal information.
4. Website spoofing is the practice of building a fake website in order to commit a bank impersonation scam. Phishers exploit the names, logos, pictures, and even the code of the original website to make spoof sites appear real. This includes the URL in your browser’s address bar, as well as the padlock icon on your browser toolbar’s bottom right corner.
5. Fraudsters use Vishing to steal personal information such as your user name, password, OTP (one-time passphrase), URN (Unique Registration Number), and any other personal information, such as your date of birth or mother’s maiden name. Customers are tricked into handing over personal and financial information to fraudsters who pretend to be bank representatives.
6. Skimming is the practice of obtaining sensitive information from credit or debit cards by reading the magnetic strip on the back of the card. Fraudsters read the magnetic strip on the back of a credit/debit/ATM card to get the cardholder’s personal information.
A tiny gadget is hidden in the card slot of ATMs and other payment terminals in order to perform this. It uses a “skimmer” to read the card’s information and save it in a database. The PIN can also be captured by placing a small camera in a strategic location. In addition to banks and other financial institutions, ATMs, restaurants, and other retail establishments may be targeted for skimming.
What are the consequences for financial institutions?
In any economy, one of the most devastating effects is the rise of bank impersonation scams as it can throw the economy off-kilter, which can lead to a decline in the stock market.
Scammers frequently target online users to mislead them into sharing their personal information or worse send money via impersonation websites passing as financial institutions.
It can take a month or more for a bank to trace down missing money when users wire money to bad actors.
It goes without saying that this can lead to significant security and financial concerns for both financial institutions and customers if left unchecked.
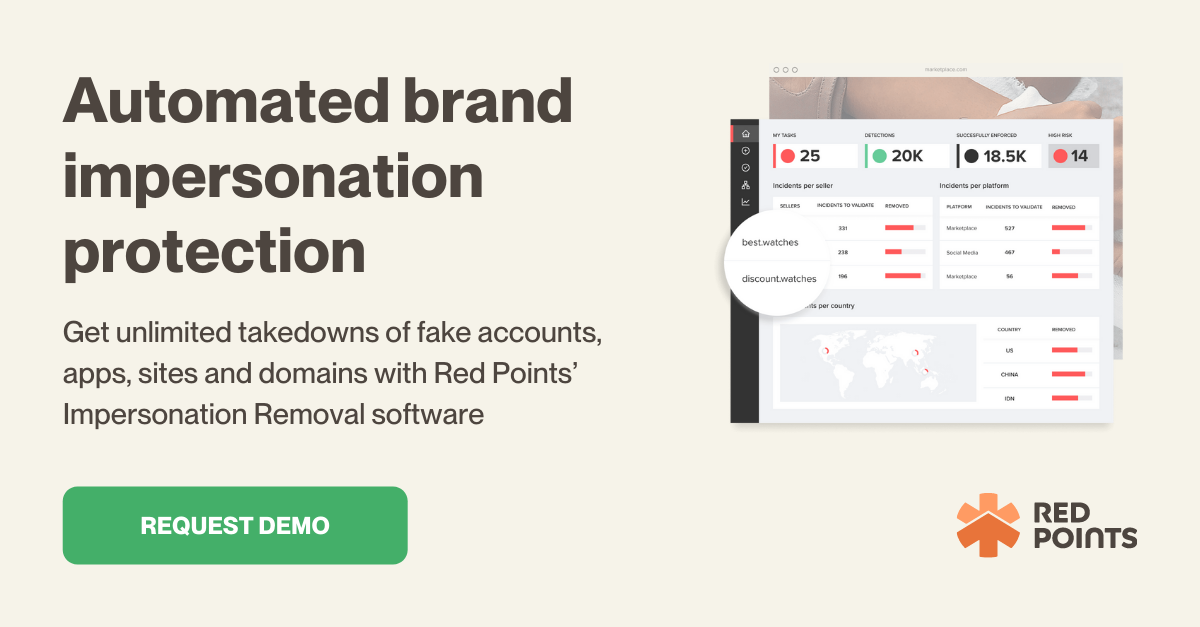
How to stop bank impersonation scams with Red Points?
Securing your brand from bank impersonation scam requires cutting-edge impersonation protection technologies and world-class professionals.
Impersonation protection software like Red Points can help you:
- Keep your social media accounts safe from bank impersonation by requesting that questionable accounts be taken down, or you can let our impersonation protection software handle it for you.
- Stop fraudsters from using your brand name to steal your traffic and perpetrate fraud.
- Remove any applications that are acting in your place. Using keywords and photos, you can rapidly find apps that use your brand. On the most popular app stores and APKs, the takedown process is triggered right away.
What’s next
The financial system faces reputational risk, operational risk, and commercial risk as a result of bank impersonation scams. Frauds involving large sums of money have the potential to bring down banks or to make them more vulnerable, necessitating the merger of failing institutions with stronger ones. Make certain that no bank impersonation infringement goes unnoticed or unchallenged. With Red Points’ Impersonation Removal technology, you can rest assured that your company’s reputation is being safeguarded around the clock.