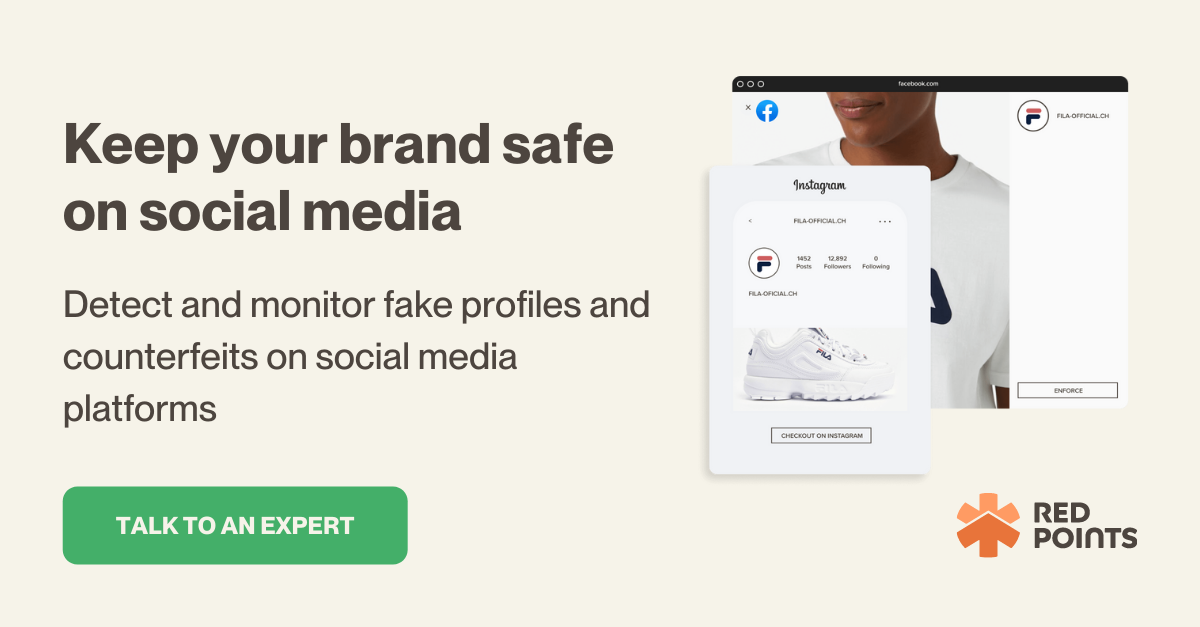
Your customers’ security is paramount to you and your organization. That’s why cyber scams like brand and social impersonation harm businesses of all shapes and sizes. According to the Federal Bureau of Investigation (FBI), impersonation attacks between 2017-2022 caused losses of more than $2 billion. Stealing your client’s sensitive information and money, can erode the confidence of the victims and ultimately impact your customers’ trust in your organization. In this post, we will take a look at the different types of impersonation, and how brands can fight back.
Summary
- Scammers posing as your brand are becoming a significant risk to customers and businesses as they often use sophisticated techniques to make their attacks appear credible.
- Through social media, scammers are able to impersonate your organization and spread lies about your brand.
- There are many different types of impersonation, from phishing scams that ask for personal information to be sent to an outside account to full-blown online fraud that has you buying products from illegitimate sellers.
What is social media impersonation?
Impersonation in social networks refers to accounts that use the name, image, or other identifying elements of a person, company, or organization for fraudulent purposes. Generally speaking, it is the act when a person pretends to be someone else on social media platforms. Social media impersonation differs from other legitimate uses of a brand or person, such as fan accounts, parodies or criticism, and information pages.
Are impersonation and identity theft the same thing?
Although similar, identity theft and impersonation are not exactly the same thing. Impersonation by itself is not a criminal offense (unless the person being impersonated is a police officer, a doctor, or a solicitor). When it comes to the impersonation of a brand, however, the actions taken in order to carry out such an act involve illegal actions, such as trademark infringements, breaches of privacy, and financial fraud.
Identity theft involves the theft of your personal information or your business’s private data in order to gain access to your financial details. Impersonation is more simply the act of someone pretending to be an individual or a business.
Types of impersonation
There are many different types of impersonation, from phishing scams that ask for personal information to be sent to an outside account to full-blown online fraud that has you buying products from illegitimate sellers. Here are some of the most common ways scammers have been impersonating brands:
- Phishing: by impersonating a brand (or its employees), scammers seek to obtain sensitive customer information or data, such as social security numbers, passwords, or bank details. The financial sector (particularly many FinTech companies, which tend to have more interaction with their users through social networks) is one of the most impacted by these practices.
- Counterfeiting: these are fake pages of a brand that try to deceive its consumers by selling them inauthentic products. They often operate through aggressive advertising campaigns that target brand consumers and redirect them to a website outside the social network where the transaction takes place. This practice affects a multitude of industries but is particularly relevant in the luxury and fashion industries.
- Fake news: these are accounts that impersonate politicians, celebrities, public institutions, or advertising agencies, among others, with the aim of disclosing false information and news.
- Scams: although not always carried out by impersonating a third party, many of the main frauds on the Internet (coupons, romance fraud, 491 scams, account takeover, etc.) have their origin in identity theft through social networks.
How do impersonators operate?
The way impersonators operate is very diverse and depends on the social network, the objectives pursued by the impersonator, and his level of sophistication. However, there are some common behaviors that have been observed in different impersonation attacks:
- There is usually a correlation between the number of impersonations a brand suffers from and its social media presence. At one end, brands that do not have an official account are often an easy target for fraudsters, who will try to take advantage of this gap to deceive the brand’s followers. At the other end, we tend to observe that brands with more presence (number of followers, posts, campaigns, etc.) are also a prime target for impersonators, as they know there is a large base of brand customers to defraud.
- Impersonators often use the same photos, names, descriptions, posts, hashtags, etc. as the official accounts. It is also common for them to impersonate “support” or “customer service” pages or run raffles and promotions. The fact that a given account has few posts does not imply that it is risk-free: it may be sending private messages or running aggressive ad campaigns on the social network and redirecting those affected to external web pages on which to defraud them.
- On many social networks, newly created accounts can take up to several days to appear in search results. The most sophisticated impersonators take advantage of these periods when they are less visible to launch very aggressive attacks, often through ad campaigns targeted directly at the brand’s consumers.
- The type of social network strongly determines the forms of impersonation. On networks such as LinkedIn, for example, impersonations of brand executives or employees are more likely to be encountered. In networks such as Facebook, impersonations are most commonly done through “Pages”, although sometimes they are also carried out through “Profiles”, “Groups” or “Events”. It is important to understand the way each platform works and its audience in order to correctly identify the different types of impersonation.
Impersonation on social media: a self-help guide
Most platforms provide reporting tools for those affected, but they usually leave the responsibility of identifying and reporting any impersonation to the impersonated individual or organization. In this regard, the first piece of advice is clear: be proactive about the problem, because no one is going to solve it for you.
However, if you’re a growing brand and impersonators increasingly target you, you may find that there aren’t just one or two copycat accounts lurking, but hundreds, if not thousands of fraudulent accounts profiteering off your brand. At this point, manually taking each one down becomes a game of Whack-A-Mole. Instead, you should consider an Automated Social Media Protection Software that scopes out impersonators before your brand reputation and profits fall into their hands.
The following are some key considerations to have in mind when dealing with social impersonation:
- Automation: in very serious cases, the use of technology for daily tracking and reporting of violations is a must. Consistency and speed in detecting and reporting these accounts is key: this prevents them from expanding their follower database and consequently, the damage they can cause.
- Broad Keywords: in addition to the brand name, searches should be performed with all kinds of variations of the brand name (misspellings, separations, alphanumeric combinations, etc.). It is recommended to monitor hashtags or keywords frequently used by official accounts.
- Logo recognition: Image and logo recognition models help to identify the presence of logos and other distinctive brand signs in profile pictures, which can be very useful both to remove false positives and to determine criticality and risk of confusion.
- Risk & Similarity scores: the use of algorithms based on account parameters (name, description, photos, number of followers and followed, posts, opening date, etc.) can help determine the criticality of a particular account or the risk of confusion with official accounts, key elements when prioritizing and choosing the best enforcement strategy.
- A comprehensive brand protection strategy should monitor brand usage beyond social media to sites such as domain names, websites, and app stores.
Click on the following links in order to find out how to report impersonation accounts on specific social media platforms:
- How to report an impersonation account on Instagram
- How to report a Twitter account for impersonation
- How to report a Youtube channel for impersonation
- How to report fake accounts on TikTok
Automated Social Media Impersonation removal for busy executives (with Red Points)
Monitoring
Red Points’ Social Media Impersonation Removal Solution detects and takes down impersonators on social media, apps, and standalone websites 24/7.
Detecting
Next, Red Points will use image recognition software and bots to detect any infringements, listing them in your Red Points dashboard. Try detecting 36,000 infringements without the help of bots…
Validations & Prioritization
Image recognition and keyword searches will filter thousands of brand impersonation infringements. On your dashboard, you will then be able to review (1) Red Points’ selections and attend to social media infringement cases that, according to your pre-established rules, the platforms consider high risk (2).
Enforcing
Depending on the rules you set for the automated takedown process, you can either request the takedown of accounts that Red Points has detected, or you can let Red Points do that automatically.
Reporting
Red Points Impersonation Removal Dashboard allows you to visualize a lot of data about your infringements, including which apps are most often used for impersonation.
This is a powerful tool for sharing data with relevant stakeholders and tracking the success of your brand protection efforts.
What’s next
Social media impersonations represent a growing problem affecting thousands of brands and individuals across most platforms. The associated risks include loss of revenue and traffic and, most notably, reputational issues and loss of consumer trust. Brands must take a proactive approach to the problem, ensuring that a comprehensive and scalable protection system is in place to identify and remove such infringements as quickly as possible. Technology and expertise in intellectual property enforcement are key elements to ensure the success of this strategy. With the Red Points’ Impersonation Removal solution, you can take advantage of machine learning and AI to automatically find and remove fake sites, apps, and domains to protect your customers and reputation.