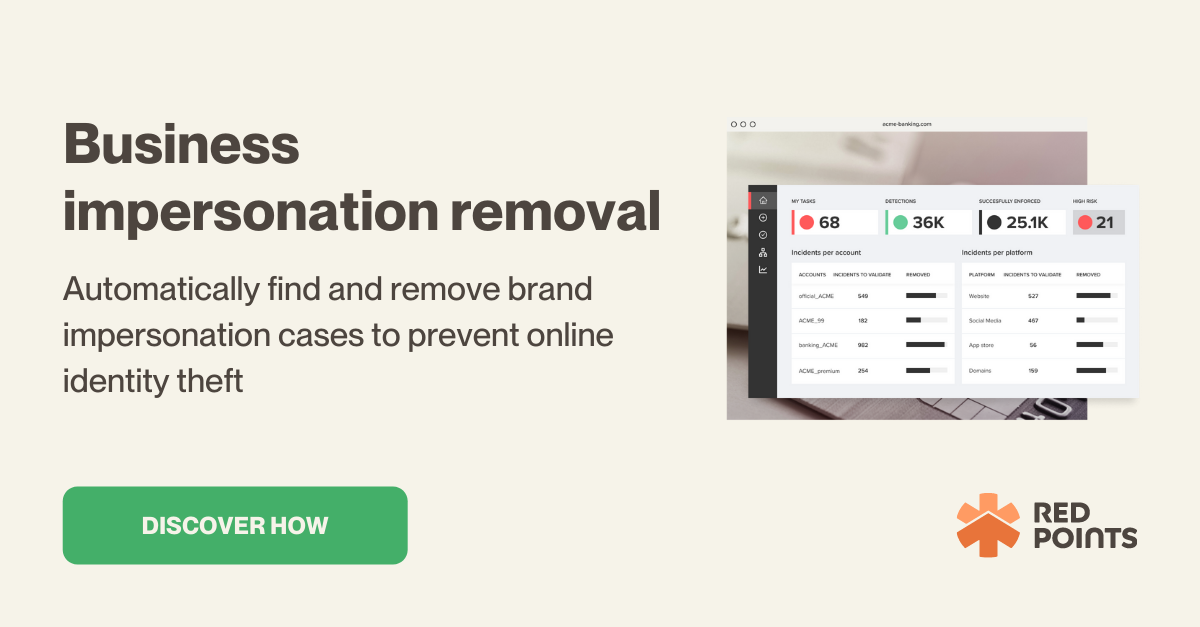
No matter how stringent internet safety measures are, impersonation scams continue to defraud companies and their customers of huge sums of money. Between 2017-2022, the Federal Trade Commission received 2.5 million reports of impersonation scams, with the loss to consumers coming in at more than $2 billion.
Companies are forever implementing additional security checks and spending more time and money fighting cybercriminals – so why are impersonation scams so successful? The secret lies in human error; cybercriminals prey on human psychology. Pixel-perfect fake websites, urgent emails from company “CEO’s”, and invoices sent from fraudulent third-party vendors, are all common impersonation scams that affect businesses both large and small.
In this article, you will learn:
- What businesses impersonation scams are,
- Examples of business impersonations scams,
- And how to prevent these attacks from affecting your business.
What is a business impersonation cyber attack?
An online business impersonation attack is when a cybercriminal poses under the identity of a business or business representative for malicious purposes. As with all online impersonation scams, the aim is usually to obtain money or sensitive data.
Often we think of cybercriminals as tech-savvy coders who create complex software systems to hack into company computers. The truth is, many cybercriminals – especially impersonators – have little more tech knowledge than the average person. They simply prey on people’s tendencies to trust a well-worded phishing email, to breeze past a mistyped domain name, or to do what their boss tells them (even when it’s a fraudster pretending to be the boss).
All it takes is the creation of a similar-looking email address, or copying and pasting logos, content, and products across from the original website or social media account, to a fake one. In just a few clicks, the cybercriminal is ready to begin duping customers and employees into divulging sensitive information.
Is business impersonation a cybercrime?
Cybercrime is essentially an umbrella term for all sorts of fraud and crime that takes place on the web. This can include installing ransomware on computer systems, hacking peoples’ email accounts, and harassing individuals online. Online impersonation – whether impersonating a business or individual – is no exception. It constitutes a type of identity theft, where a fraudster steals an individual’s or business’s identity to defraud or harass.
What are the consequences of a business impersonation cyber attack?
The consequences of a cyber attack on a business depend in part on how the impersonation attack is conducted. Is it a phishing email? Or a fake website? Or a copycat social media profile? The impact will always, however, be felt by the bottom line.
Financial losses: Impersonation causes financial losses in multiple ways. For example, a fraudster posing as a CEO or senior executive may send an email requiring a lower-ranking employee to wire them money. In a similar fashion, supply chain compromises are when bad actors disguise themselves as third party vendors and request payment of a false invoice. It’s also worth considering that every customer stolen from you by an impersonated website or phishing email, is a sale lost.
Lowered search visibility: Impersonators who create lookalike websites draw clientele into their trap through a variety of methods. They may use promotional techniques such as paid ads and fake social media profiles, or they may get their fraudulent website to appear at the top of search engine results through black hat SEO. All of these methods will divert traffic away from the legitimate business’s website, and lower its search visibility. In the end, this amounts to a loss in potential customers.
Reputation damage: Business impersonation can be terminal to a brand’s reputation. Not only will new customers be forever scarred by a bad ordeal if their first experience with your brand was in fact with a fraudster impersonating your brand, but repeat customers will also associate your brand with malpractice if you allow the problem to persist. Customers are even likely to blame your brand, and not the fraudster, for the fault.
According to a recent report by Comparitech, the share prices of companies compromised by data breaches fell by 3.5% on average. It’s therefore vital that brands always do the utmost to protect their brand reputation.
Intellectual property (IP) infringement: Product designs, websites, logos, technology, and content are among a company’s most valuable – yet intangible – assets. For S&P 500 firms, 90% of their value were intangibles in 2020. Often, however, unscrupulous fraudsters will steal your IP via fake websites selling counterfeit goods, or impersonated social media profiles, thereby hitchhiking on your brand’s reputation and simultaneously eroding it.
Business operations overhaul: When your business has been hit by cybercrime, and the issue hasn’t been caught early enough, it can lead to system changes. These are not always a bad thing, of course, but can constitute a setback and interfere with company goals. Payment practices, logins, software, and even branding, may need to be changed, as well as staff education, so that impersonation attacks can be prevented in future.
Examples of business impersonation cyber attacks
Executive impersonation
Also known as CEO fraud, Business Email Compromise (BEC), and whaling, executive impersonation boomed during the pandemic. A more sophisticated cybercriminal may hack a senior executive’s email account, but in general, fraudsters simply create a spoofed email address that looks genuine. Posing as a senior executive or CEO, they will send an email to a lower-ranking employee requesting a money transfer, usually in an urgent manner.
Clearly a psychological tactic, the cybercriminal hopes that the lower-ranking official will unquestioningly do what their boss tells them. Added to that, the urgency means the employee doesn’t have time to question the email’s authenticity. This impersonation scam is highly effective and a favorite among fraudsters. Famously, a lone wolf once defrauded internet giants Google and Facebook of more than $100 million using this method.
Supply chain compromise
This type of impersonation is a kind of BEC, where a bad actor impersonates an external third party to redirect company funds. They accomplish this in one of two ways. The more sophisticated cybercriminals may be able to infiltrate a vendor’s email account through malware or phishing attempts. This allows the hacker to gain more than just a one time invoice, since if they engage in ongoing conversations with the company, they may get sensitive information, too.
The other method is simply to mimic the vendor’s email address and create a lookalike website. This allows them to imitate the third party and redirect payments for invoices. This can be very financially damaging for both parties involved.
Lookalike websites
It doesn’t require a tech pro to copy across the identifying elements of a brand’s website and pass it off as their own. Impersonating a brand’s website – also called similar domain name phishing – allows cybercriminals to hijack a good brand reputation, gain trust from the customer, enough for the customer to then spend their money or share valuable information with the fraudster.
Cybercriminals use tactics such as typosquatting, whereby they create a domain with a typo’d version of the legitimate brand’s name. For example, amzon.com instead of amazon.com. Website impersonation is a significant infringement of your brand’s IP, since they are using your products, content, logos, and other identifying factors to create a fraudulent website.
Fake social media profiles
Social media impersonation refers to accounts that use the name, image, or other identifying elements of a person, company or organization for fraudulent purposes. In the case of business impersonation, cybercriminals can go about defrauding individuals in a number of ways. After copying the identifying elements of a brand, they may take advantage of brands who have little-to-no social media presence to deceive followers. At the other end of the spectrum, brands with big social media presences are a good target due to their large base of potential victims.
Newly created accounts can take days to appear in search results. This offers a small window of opportunity where sophisticated cybercriminals can launch aggressive attacks through ad campaigns without going noticed.
7 ways to prevent a business impersonation cyber attack
1–Implement security checks
Wherever sensitive information or money is concerned, make sure your business has several systems in place to avoid any mishaps. Every financial transaction system should be configured so as to have secondary authentication. This can be done in a number of ways, such as through sending an authentication code, or having a call with the finance controller before the transaction takes place.
2–Update your copyright and trademark
Make stealing your company’s IP less appealing by registering your trademark and copyright. While all your intellectual property is automatically protected under copyright law, you have a much better chance of winning an infringement case if you’ve registered your copyright and copyrighted your website content. Criminals won’t be so tempted to impersonate your website if they know they may face legal action.
3–Employee training
Over 95% of security breaches occur due to human error. Some of those errors can be catastrophic, such as when hackers tricked three British private equity firms into wiring them $1.3 million. It’s therefore hugely important to educate your employees about cybercrime and let them know what to look for in an impersonation attack. However, this option is not foolproof. According to a survey done by the Harvard Business Review, 67% of those polled admitted to not following protocol in some instances, with the most common reasons cited as workloads and deadlines.
4–Consumer education
Harder to enforce, is consumer education. It can certainly help, however, to alert consumers to any scams circling the internet. Frequently banks will also tell consumers that they would never ask for personal or credit card details over email.
5–Protect your domain name
In order to protect your business from copycat websites, make sure you have registered all the typo’d versions of the brand name to avoid typosquatting. You can also trademark your domain name for added protection. One of the most effective measures for protecting your business against lookalike websites is through domain management software that automatically detects and takes down domains that are infringing your trademark.
6–Monitor social media platforms
Actively monitor social media platforms on a regular basis to prevent social media impersonation of your brand. You could search for branded hashtags as well as business names similar to yours.
7–Get automated impersonation removal
The most effective method to ensure social media, email, and website impersonations are taken down before they have a chance to do any damage, is through automated software. Red Points automated Brand Impersonation Protection scans websites, social media platforms, and app stores 24/7 for any instances of infringement. Once found, Red Points sends out takedown requests so that customers, employees, and revenues remain untouched by fraudsters.
What’s next?
As we’ve seen, the methods cybercriminals use to impersonate businesses are manifold. Most of them don’t even require specialist tech knowledge. Rather, these criminals rely on psychological tactics to squeeze financial information or private details from customers and employees. With 95% of security breaches down to human error, clearly one of the chief preventative measures should be to educate employees and consumers.
While this is an important step in fighting cybercrime, it’s not foolproof. A comprehensive and effective way of ensuring that your business doesn’t fall victim to impersonation, is through automated software. Get unlimited takedowns of fake accounts, apps, sites and domains with Red Points automated brand impersonation protection.