Online impersonation can include everything from fake social media accounts to a business email from the purported “CEO” of a company. The goal is usually always the same: to make money through fraudulent means.
The pandemic and the cost of living crisis have both given rise to a variety of scams, and as recently as 2021, Nationwide found that 26% of survey respondents had fallen victim to an impersonation scam. If you think that only naive, tech-shy individuals fall for impersonation scams, think again: a lone wolf famously conned even tech geniuses like Google and Facebook for more than $100 million by pretending to be one of their third party vendors.
When impersonators target businesses, money isn’t the only thing at stake: brand reputation can suffer, too. In this article, we will cover the following:
- Different types of online impersonation
- When impersonation becomes a criminal offense
- Examples of online impersonation
- What to do if someone impersonates your business
- How to prevent online impersonation from impacting your business
What is online impersonation?
Online impersonation is when a person uses an identity other than their own for malicious purposes. Usually, the aim is to obtain money or ruin a brand’s reputation. But online impersonators can also be out to harass, intimidate, and threaten their victims.
On an individual basis, online impersonators could ask close acquaintances for money, open a crowdfunding account, or get a loan in the impersonated individual’s name. If their aim is to do you harm, they may post offensive or embarrassing material. Bad actors can also fake websites, commit CEO fraud, and create false smartphone apps, all of which cause substantial losses for both the business and the customer.
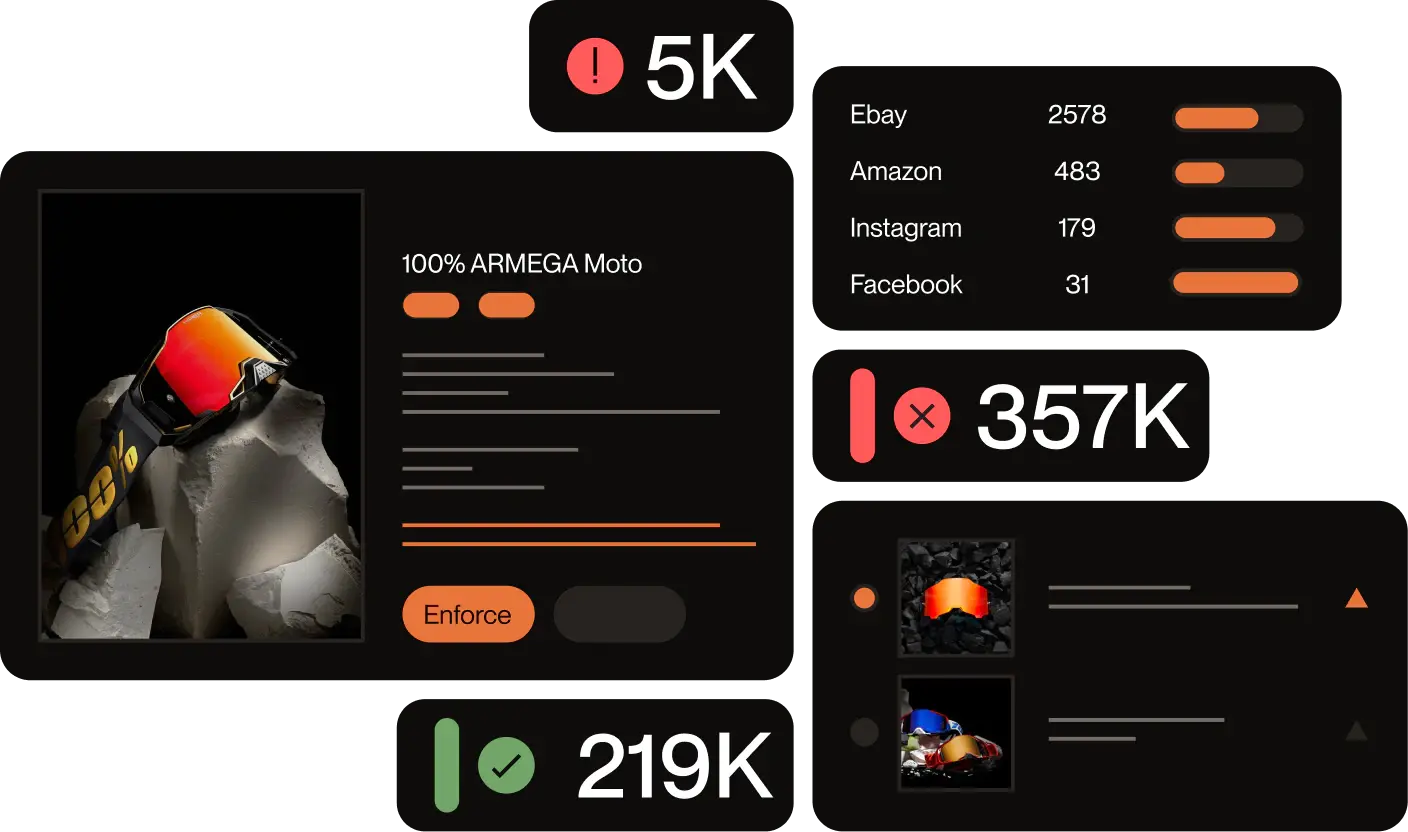
Often, individuals and businesses won’t know that their details are being used by a cybercriminal until significant reputational and financial harm has been done. This is why it’s important that brand’s get automated software to monitor and takedown any offending profiles, websites, or apps.
Examples of online impersonation
Website impersonation
Also known as domain spoofing, website impersonation can be carried out in a number of ways. Essentially, website impersonation is when someone creates a lookalike website and dupes customers into buying counterfeit or nonexistent products as well as handing over their personal or financial data. This is highly damaging to businesses, since the fake website may lower your search visibility, defile your reputation and relationship with customers, or even impact your business’s bottom line.
Cybersquatting is one means of website impersonation. Fraudsters claim domain names in order to take over someone else’s trademark or brand name. Domain name ownership needs to be regularly updated, often on a yearly basis, but individuals and smaller companies sometimes don’t realize this, and end up allowing their domain to expire incidentally. Cybersquatters spot the opportunity and claim the domain name for themselves.
Even if domain owners regularly update their domain registration, cybersquatters may find extensions of the same domain and then use those to dupe customers. For example, the original, legitimate website may be called domainname.com and the cybersquatter may spot that domainname.co.uk is free, so they buy that one instead. It is always recommended for companies to register not only their own brand name, but any variations to avoid this happening.
Sometimes, the aim is to sell the domain name back to the original owner for an increased fee. Other times, and even more insidiously, cybersquatters may wish to divert traffic away from the original website and sell counterfeit services and products.
Typosquatting is similar to cybersquatting, but it relies on the easily made mistake of typing a web address incorrectly. For example, instead of amazon.com, you may type amzon.com, be redirected to a lookalike website, and give away all your valuable details (and money) to a fraudulent entity.
Social media impersonation
Social media impersonation refers to the act of creating an account that uses the name, image or other identifying elements of a person or organization for fraudulent purposes. The cybercriminal may even steal your details and hack into your account.
Many people will either know someone or be themselves a victim of social media impersonation. More difficult to detect than the all too common fake celebrity account, however, are businesses that are impersonated on social media. Social media platforms such as Instagram and Youtube, for example, have robust systems in place whereby users can report dishonest activity or suspected scams.
It can, however, take some time for that account to be taken down. Finding out that you have been impersonated in the first place isn’t straightforward either, so businesses should always use preventative measures.
Mobile apps
Cybercriminals are getting smarter, and can even go to the extreme of creating a fake mobile app. The fintech industry has been a particular target of this type of impersonation scam. Essentially, the fake mobile app operates in much the same way as fake websites: the fake app mimics the design and function of a legitimate app and tricks people into downloading it. Once installed, cybercriminals may intercept the input of sensitive data and information, divert payments, or execute ransomware attacks.
Executive impersonation
Also known as CEO fraud, executive impersonation is when a cybercriminal assumes the identity of someone working at the company – usually in a leading position – to gain sensitive information and money. Sometimes they do this through creating a fake email address (known as email phishing), and other times they hack the company’s email system.
Usually, executive impersonators send an email to someone at the company requiring urgent transference of funds. Since the impersonator appears to be a senior member of the company, lower ranking executives may give the transfer of data or money the green light without double-checking the email address or other giveaway scammer details.
Third-party impersonators
Fairly common in the world of impersonation scams is when attackers pretend to be third-party vendors or suppliers. They may send employees at a company invoices for their services, complete with look-alike websites and email addresses. Once again, this falls into the category of fake websites and email phishing.
Is internet impersonation illegal?
Impersonation by itself is not a criminal offense, unless the impersonated individual is a police officer, doctor, or a solicitor. However, if someone is impersonating an individual or a brand, the actions subsequently taken are usually illegal and therefore punishable in a court of law: breach of privacy, trademark infringement, misuse of private information, defamation, harassment, and financial fraud.
Identity theft and impersonation are similar, but not the same. Identity theft involves someone stealing your personal information or your business’s private data to access your financial account. Impersonation is when someone else pretends to be an individual or a business, usually for nefarious purposes.
What to do if someone impersonates your business?
Protecting your brand identity is paramount to maintaining a positive brand image and a healthy bottom line. Monitoring the internet for fraudsters pretending to be your brand and getting them taken down is a full-time job in itself. That’s why the most thorough and efficient way of protecting your brand is through automated software such as Red Points’ Impersonation Removal software.
If you find out that your business is being impersonated, each platform will have its own system you have to follow in order to send a takedown request. Below are step-by-step guides for some of the most common incidents of business impersonation:
- How to report a fake Facebook business page
- How to report an impersonation account on Instagram
- How to report a Twitter account for impersonation
- How to take down a fake website: full guide to protect your brand
- How to take down a Google My Business page
- How to report fake Google ads that pretend to be your business
- How to report a fake account on TikTok
- How to report a fake online store that pretends to be your brand
How to prevent online impersonation?
Employee training
It’s a known fact that most security breaches are down to human error. This means one of the best preventative measures you can take is to continuously train your employees and make them aware of any current scams.
Many companies have cybersecurity manuals that employees must read at the beginning of their employment. Top tips include regularly changing account passwords and never signing in from public devices.
Consumer education
Less straightforward to execute, but also highly important, is educating your consumers. Let them know how your company operates in the process of requesting customer details or accepting purchases. For example, perhaps you never ask for customer details over email. Let your customers know about this, so if they receive a phishing email they will know it shouldn’t be trusted.
Protect your company domain
Domain spoofing, cybersquatting, and typosquatting are all ways that cybercriminals attempt to dupe your customers. You can trademark your domain name as well as register variations of your domain name or common typo variations. These actions, together with a domain management software, will help to protect your domain name.
Monitor the web for impersonation attacks
Monitoring the internet for fake apps, fake social media accounts, and fake websites is a 24/7 job, and that’s before you begin the task of issuing takedown requests and making sure bad actors have complied. Red Points’ automated Brand Impersonation Protection uses bots to scan the web night and day for any attempts at impersonation. Once caught, Red Points will make sure any bad actors are taken down, so that you can concentrate on building your business instead of worrying about leaking profits.
What’s next
There are a multitude of ways bad actors can take advantage of the brand you have so carefully built. Online impersonation is the fastest growing type of cybercrime and it can take many forms. Whether it be email phishing schemes and CEO fraud or fake mobile apps and websites, businesses have to remain constantly vigilant to the threat of cybercrime.
Impersonation attacks can divert traffic away from your site, negatively affect your brand reputation, cause you to lose new and repeat customers, and ultimately, siphon away your revenue. Get unlimited takedowns of fake accounts, apps, sites and domains with Red Points before the problem gets out of control.