Cybercrime has become a hot topic, particularly with the rise of AI, deep fakes, and other advanced technologies designed to trick or bamboozle unsuspecting victims.
At its core, cybercrime involves offenses that aim to damage someone’s reputation or cause them physical or mental harm, using the internet or mobile networks as either the tool or the target.
Breaking it down, there are essentially two main types of cybercrime: using the computer as a tool and targeting the computer itself. The latter demands a high level of technical skill and is often the work of organized groups rather than individuals acting alone.
These crimes, which include deploying viruses, malware, and other attacks, pose a significant challenge due to their sophistication and the collective effort required for their execution. Thankfully, these are less common because of the expertise needed.
On the other hand, crimes that use computers as tools to exploit human vulnerabilities—such as scams, theft, and harassment—are far more prevalent. These activities have been around for ages, well before the advent of computer science, and rely less on technical prowess and more on exploiting human weaknesses.
In our market research, which surveyed 150 leading Ecommerce businesses, sheds light on this increasing concern and the need for vigilance in this area.
In this article, we will be focusing on:
- The five most common types of cybercrimes
- How are they perpetrated
- How you can protect your brand and yourself

5 most common types of cybercrimes
Phishing scams
Phishing is one of the main forms of social engineering attacks. Its goal is to trick unsuspecting users into giving away their personal information.
Usually, these cybercrimes are committed by impersonating trusted and popular brands by creating fake social media profiles and rogue websites to lure users into them. These sites copy the appearance of the real website to create a sense of security and usually ask victims to fill out forms with personal information to receive some kind of benefit, such as discounts.
This information is later monetized, and in the worst-case scenario, bank information could be stolen. The most refined of these sites might include malicious scripts that scrape this information out of your browser, without the need for forms. So even if no bank information was given, there are plenty of ways to gain profit from personal information as the Cambridge Analytica scandal proved.
From a business perspective, these scams are usually trying to impersonate potential providers.
How to stay safe from phishing scams
The nature of phishing scams means that they are not always easy to spot. They might replicate an authentic website that you recognize and trick you into sharing information with ‘that’ company. Or they may send you an email pretending to be a person or business that you know and trust. While others are less refined and easier to spot as a scam.
To be sure that you don’t fall victim to more sophisticated phishing attempts, it’s important to check any domain links that are sent to you. Do not provide any kind of information on websites that are not secure—you can identify secure websites easily as they always display a little padlock at the start of the URL bar.
Pay attention to social media profile names and domains too. Big brands will usually have their social media profiles verified and their website copy will always be grammatically correct. Domain typosquatting is a very common tactic whereby scammers slightly misspell words in the hope you don’t notice—if example using a capital I in place of an L or missing letters out of longer words.
You should also always check that a sender’s email address is legitimate and doesn’t use incorrect spellings or address formats in an attempt to imitate the legitimate address owner.
Of course, applying common sense is very important too against these scams. If it’s too good to be true, it usually is.
From a business standpoint, instruct and educate your employees, since ultimately it comes to individuals to stay safe from this type of cybercrimes.
Internet fraud
This type of scam usually asks people to send money with the promise of a much larger sum in the short term. The most famous one is the “Nigerian” scam, also known as the “419” scam which is the number of Nigerian laws it violates.
These scams were already widespread through fax, telephone, and traditional mail, but the Internet made them much easier to pull off and as a result, they have become more widespread.
Usually, the victim receives communication from someone in need of help to move a large sum of money from a foreign country. There are plenty of variations of this scam and more are developed each day.
The victim will be asked to cover a small portion of the cost of moving the money or asset and will be promised a bigger cut of the benefits when the process is over.
If the victim falls for it and transfers money, they will likely be told that complications have arisen and that more money will be required. Of course, the victim will not recover anything and this will go on until the scammer feels like there’s nothing to gain from this victim anymore. Then they will simply jump to the next one.
Another common kind of internet fraud is related to fake job listings, where the victim is asked to pay some money to cover the cost of paperwork or pre-onboarding information.
How to stay safe from Internet fraud
Common sense is our best defense against this type of cybercrime. As with phishing scams, if an offer is too good to be true, then it’s probably an attempt at internet fraud.
Be cautious of unsolicited communications from strangers offering very attractive deals, and never pay in advance for any services or arrangements until you have thoroughly researched them—even checking in with trusted friends or acquaintances—and 100% confirmed their legitimacy.
Online intellectual property infringements
The most common types of Intellectual property infringements include t:
- Counterfeit and replica goods: products created to look identical to an existing product made by a legitimate brand; while counterfeits are branded, replicas are not.
- Piracy: piracy is the unauthorized reproduction, copying, and spreading of copyrighted materials.
- Patent infringement: these are products that exactly copy the functionality and mechanism of products protected by utility patents.
How to protect your brand against online intellectual property infringements
There are two main ways to protect your intellectual property online.
You can hire in-house detection and law teams to manually search the internet and enforce against infringers. This is a method that requires a lot of time and effort, as is better suited to small companies that do not have a big problem with IP infringements.
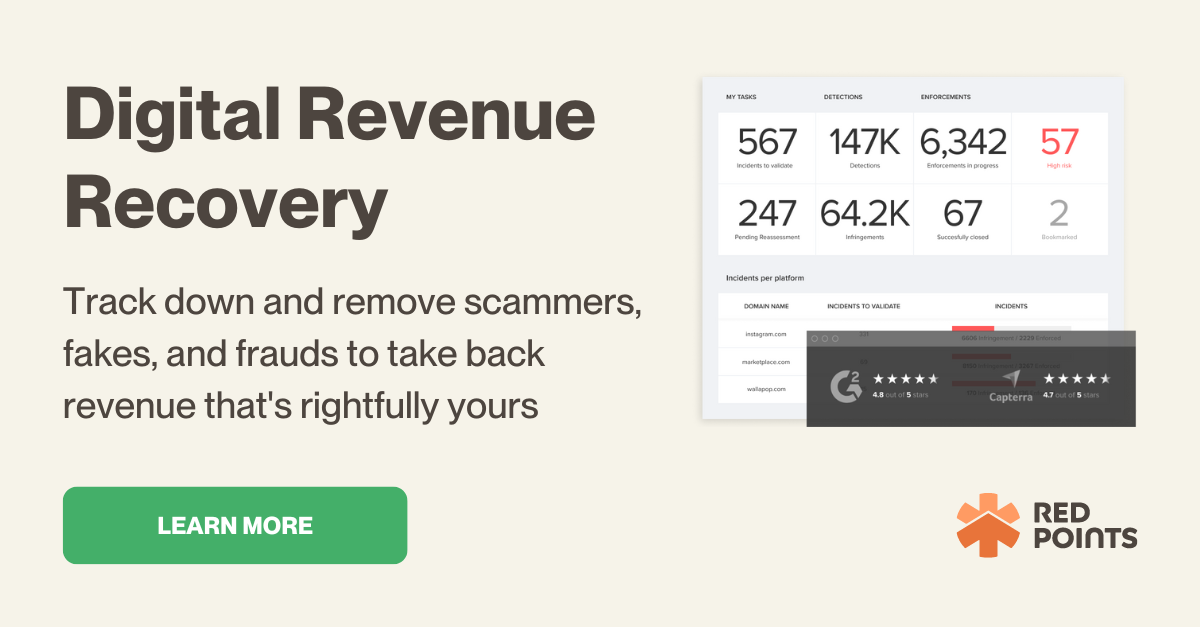
But if the problem is more than your team can keep up with or you just don’t know where to look for scammers that infringe on your IP, there are automated solutions that can help. Enter our Brand Protection software and Anti Piracy software. These AI-powered services allow you to scale your anti-fraud efforts in a fast, more streamlined, and cost-effective manner. To help you decide what the best approach to these cybercrimes is for your company we recently wrote a blog on how to choose the right brand protection solution for your business.
Identity theft
Identity theft is closely related to phishing scams. They also often use the computer as a tool to commit cybercrimes, but they existed long before the internet. Unfortunately, improvements in technology have improved their reach and ease of execution.
The damage caused by identity theft depends on the information that is stolen from the victim. If only personal information or access to accounts without payment methods saved were stolen, the fraudster may still have enough information to illegally impersonate their victim. However, if an identity thief has access to credit card information or accounts containing bank details, the repercussions can be much worse since the cybercriminal can make purchases charged to your account.
This also applies to companies, and employers should be careful to restrict access to confidential information as former or disgruntled employees may retain access to your account details.
How to protect against identity theft
The easiest and least expensive way to protect your identity online is to share as little information about yourself as possible.
You should also keep an eye on your online account activity, and proactively report any suspicious activity as soon as it happens.
Online harassment and cyberstalking
Harassment is sadly very widespread in today’s digital world. And it’s a problem that gets even worse when people feel protected by the anonymity granted by the internet. One of the fastest-growing and most publicized forms of online harassment in recent years has been revenge porn. And with the rise of AI imagery and deep fakes, harassers now even have the opportunity to create their own revenge porn images with which to torment their victims.
Online harassment and cyberbullying are usually contained within social media in the form of posts, comments, or direct messages; but they could also be sent through email. These messages mostly tend to be defamatory or threatening, either against one individual or group.
Cyberstalking is another type of harassment that focuses on a single person, who the criminal monitors closely. It is likely that employers, colleagues, and familiars of the victim will also be contacted both to slander the victim and to try and extract more personal information to deepen their stalking activity.
Cyberstalkers will usually resort to doxxing if they want to push the victim harder. This phrase refers to the releasing of the victim’s personal information for malicious intent, usually in toxic online communities where they hope to find others willing to join the stalking.
These cybercrimes are extremely damaging to the victim’s mental health, and there have been multiple reports of victims who developed mental illnesses and even ended up committing suicide as a result of online harassment. This then takes the crime committed to new and even more serious heights—even if it was not the harasser’s original intention.
How to protect against online harassment and cyberstalking
The first course of action against online harassment and cyberstalking is to report all cases to the relevant social media platform, and to the competent authorities.
The problem is that usually the victim will feel too scared to report these cybercrimes in case the criminal steps up their efforts and the harassment becomes worse. This is especially true in cases where the victim knows their attacker. But you do not have to be the victim of abuse to report it. If you suspect someone is being harassed or stalked you can report on their behalf.
What’s next
As we have seen, cybercrime takes many forms from impersonation to domain spoofing to stalking and harassment. Not all of these crimes came about with the dawn of the internet. Many of them have been around for decades—if not longer—and the internet has simply made it easier and more widespread.
If your business is at risk of cybercrime, then you might benefit from Red Points’ Anti Piracy software. By detecting and combating illicit activities more efficiently than human teams can, this software protects businesses against revenue loss, reputational damage, and the unauthorized use and distribution of intellectual property.
There’s also our Brand Protection software that automatically scans thousands of sites, identifying, reporting, and taking down any pages or listings that infringe upon your copyrights. Want to learn more about how these services can keep your company safe against cybercrime? Request a demo today.