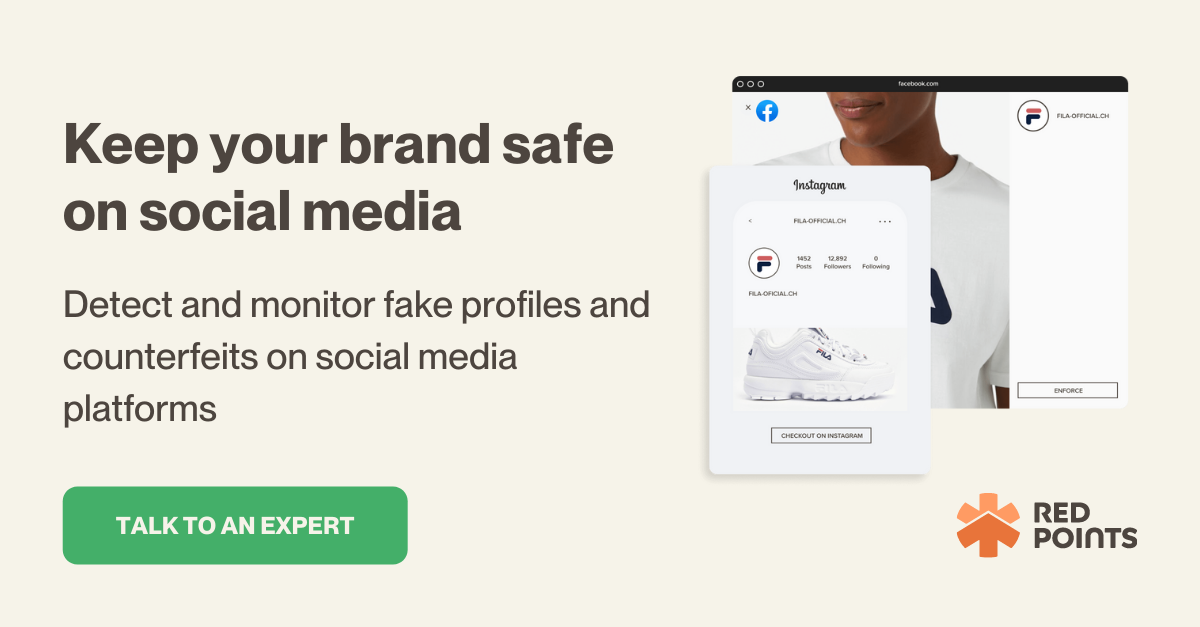
With nearly 260 million active daily users, Twitter has become a staple of online life in the 21st century. Although it is only the 15th most-used social network overall, it is one of the most popular online spaces where people go to actively seek information, rather than just chat with friends. In fact, 34% of Twitter’s users say that they use Twitter to follow brands or companies. That means that if someone is using Twitter to post false or negative information about your brand, or even worse to impersonate you or your company, you need to know how to take down a Twitter account with malicious or fake content.
Why should brands monitor and report Twitter accounts?
Monitoring Twitter is crucial to understanding your customers, and competitors. It’s how you discover new trends and important discussions. It tells you what your customers care about, and you can keep tabs on your competitors.
However, there is a darker side to Twitter. People often post offensive, defamatory, or fake content on there, or even create fake or spoof accounts for malicious purposes, such as phishing scams, spoofing, or other forms of fraud from bad actors. According to a recent survey, a disturbing 18.3% of business owners questioned said that they would sabotage a competitor’s online business if they could get away with it.
Fake accounts
Fake accounts purporting to be your business can be utilized by scammers for a number of purposes:
- To use your brand name with the sole purpose of diverting internet traffic
- To sell counterfeits, by using a fake profile to mimic your brand
- To commit fraud, by stealing your users’ financial information and personal details
Infringement of your copyright such as passing off your intellectual property as their own, using it without permission or selling fake goods, or any similar infringement can have a detrimental effect on your revenue, for example by using something without permission that you could have monetized. Possibly worse, your business’s reputation can be damaged irreparably in the eyes of your customers, especially in the case of a security breach leading to the loss of their personal information.
How do you get someone’s Twitter account taken down?
Step 1
Report the tweet, by pressing the three dots on the right.
Step 2
Define the reason why you are reporting the tweet.
Step 3
You will then be asked to confirm if you are sure this is the reason for reporting the account, after which you will be taken to the relevant online form to fill in.
Twitter usually takes between 12 hours and 7 days to suspend offending accounts.
Trademark or copyright violation
This is something that Twitter takes very seriously, and offending accounts will be suspended immediately if they are found guilty. Found in the “authenticity” section of Twitter’s terms of use, “commercially-motivated spam, that typically aims to drive traffic or attention from a conversation on Twitter to accounts, websites, products, services, or initiatives” is banned, as well as “Using another’s trademark in a way that may mislead or confuse people about your affiliation”
You can fill in an online form to report these issues.
It is important to bear in mind that reporting a trademark or copyright violation is a legal process, so you need to be prepared to submit all necessary documentation in order to prove your case. In the USA, this is:
- A physical or electronic signature of the copyright owner or a person authorized to act on their behalf;
- Identification of the copyrighted work claimed to have been infringed, such as a link to your original work or a clear description of the materials allegedly being infringed upon;
- Identification of the infringing material and information reasonably sufficient to permit Twitter to locate the material on our website or services;
- Your contact information, including your address, telephone number, and email address;
- A statement that you have a good faith belief that the use of the material in the manner asserted is not authorized by the copyright owner, its agent, or the law;
- A statement that the information in the complaint is accurate, and, under penalty of perjury, that you are authorized to act on behalf of the copyright owner.
If you are reporting the content of a Tweet, you must also include a direct link to that Tweet.
How can I find out who is behind a Twitter account?
Twitter is a bit of an outlier among the main social media platforms, in that it doesn’t require users to submit their personal details when creating an account. This can make tracing the owner slightly tricky. However, there are things that you can do which may reveal who is behind an account.
Step 1 – DM the account holder!
Not every account that infringes on your intellectual property (IP)may be doing it intentionally. Start by sending the user a DM and asking them straightforwardly to take down any content that infringes on your rights as the IP owner. If their intentions are malicious they are unlikely to answer, but it’s worth a try as it could save you a lot of time and hassle if it is just a case of basic misunderstanding.
Step 2 – check their bio
When registering on Twitter, all users have to fill in an online form. The problem is, that there is no guarantee that the user has given their genuine details. If they are using the account for malign activities, it’s quite unlikely they have, but in any case, this is a good starting point.
Step 3 – check their website
If the user is using Twitter to sell goods or services, it’s quite likely that they also have a website. Click on “about” to find the author’s information or other contact details. This information should be easy to find on the websites of all reputable companies.
If this fails, you can search on Google or WhoIS to find out who the domain is registered to. If you’re lucky, you will find the name, address, and telephone number of the owner, but it is possible that they protected this information.
Step 4 – search other social media platforms
Very few people have only one social media account. Searching Facebook or Instagram for linked or similar-looking accounts may turn something up.
Step 5 – use paid online tools
Tools such as Spokeo and BeenVerified are not free to use, but they are very powerful in the event that the other methods didn’t turn anything up.
Can I take legal action against a fake Twitter account?
There are several instances where you might be able to take legal action against someone for their activities on Twitter.
Under UK law, if any tweet is read and serious reputational damage has been suffered then you may be able to pursue a claim for online libel. Likewise, the Fraud Act 2006 protects against fraudulent activities. An impersonator who opens a Twitter account could be exposed to a claim for fraud if the person who has been impersonated suffers loss or damage as a result of the impersonation. A claim for fraud can result in criminal charges with a penalty of up to 10 years of imprisonment and fines.
In the USA, creating a fake Twitter account and posting knowingly false tweets falls under defamation laws, for which you can also take legal action against the user.
How Red Points can help you deal with business impersonators who are causing negative reviews
Red Points is a Revenue Recovery Platform. We can help detect fraudsters who are impersonating your business on Twitter and other platforms, causing needless damage to your reputation resulting in losses in your revenue.
Through our smart software, Red Points helps to ensure that businesses can not only recover revenue lost to fakes and scams but also retain the trust and reputation they’ve worked hard to maintain.
- Monitoring and detecting
Manually checking for online impersonators is completely impractical for any growing business, given the volume of potential infringements online. Red Points’ Business Impersonation Removal software offers scalable impersonation detection and removal solutions that allow brands to retain revenue and focus on growth.
With bot-powered searches across the web, social media sites, and app stores, Red Points can identify scammers who might be impersonating your business. Our system monitors the surface web 24/7 for infringements, for constantly watching your brand and conducting keyword searches.
In addition to this, our platform leverages technology such as image recognition, machine learning, and automated keyword searches each of which we use to protect your brand and its revenue as much as possible.
- Validation and prioritization
Red Points creates a list of potential cases of infringement, tailored to your business. It is important to check this list carefully before enforcing any takedowns, as it gives you complete control over who you want to take action against. It is important to note that enforcing a takedown is a legal process, so it is vital to correctly identify any fraudulent content before initiating takedown proceedings.
Additionally, by creating a High-Risk shortlist, you can prioritize which cases require urgent attention, and visual cards allow you to view all potential infringements in one place, without running the risk of missing anything.
- Enforcing
As soon as you confirm a detected potential case of infringement as real and click the “enforce” button, Red Points’ removal process will be triggered, meaning that any fake sites which could damage your business will be taken offline as soon as possible. Once the enforcement process has been started Red Points will monitor the entire process, ensuring that the take-down request is followed through on as quickly as possible regardless of the platform.
As well as this, our data-driven approach will provide you with metrics to track the success of your anti-impersonation efforts, and data that can be used to protect your brand in the future.
- Economic impact reports
At Red Points, we are very aware of the serious negative impact on your business that being impersonated on Twitter or other platforms can have. Companies just like yours lose revenue every day that is rightfully theirs to scammers, infringers, and fraudsters. We are passionate about helping our clients recover their revenue from these bad actors.
Our economic impact reports reveal the return of revenue based on total enforcements, the enforced economic value, and the number of incidents per asset. It is vital for any business to be able to quantify this impact. As soon as any takedown requests have been sent, you will have full access to information about the revenue you have recovered. Our performance dashboards enable you to discover the overall economic benefit you are gaining from using our solutions.
- Custom reports
Red Points’ custom reports contain lots of essential data in connection with fraudulent incidents. You can request information that is not shown on the dashboard, ranging from the number of enforcements by infringement type to the average number of days elapsed between notification and takedown. This allows you to see exactly what type of threats your business is facing, and how quickly the threats are being dealt with. Is your business being hit by scammers who have impersonated your website or profiles to steal your customers’ personal information? Is phishing an issue? Or are you being targeted by counterfeiters? All of this information will help you to assess the risks and threats facing your business, and counteract them in a timely manner.
What’s next?
With Twitter being such an influential platform, ensuring that nobody is using it to harm your brand’s reputation has never been so important.
At Red Points, we offer sophisticated Business Impersonation Removal software to ensure that you can find, track, and report sites that are stealing your identity. If you want to protect your brand identity online through an automated solution, request a demo today.