If your brand is under attack by lookalike domains, you know the damage goes beyond lost revenue—it strikes at your reputation. Customers mistakenly blame you for phishing scams, counterfeit sales, and fake login pages set up by scammers mimicking your domain.
These bad actors use sophisticated tactics like typosquatting, combosquatting, or homoglyph modifications to create deceptive lookalike sites. And without the right tools, identifying and removing these threats can feel like an uphill battle.
That’s where Red Points can help.
Our AI-powered platform has enforced over 522,000 fake site takedowns for businesses just like yours. With our expertise, you can safeguard your brand, restore trust with your customers, and stay focused on growth.
Read on to discover how to take control of domain name protection and stop scammers in their tracks.
How lookalike domain attacks work
Lookalike domain attackers use a range of techniques to dupe users, from copycatting and combosquatting to homograph attacks.
Copycatting
Criminals impersonate your website to make people believe they are dealing with a respectable business. They’ll copy your logo and brand name to fool visitors into giving personal or financial information or purchasing counterfeit items.
What to look for: Monitor the web and e-commerce sites for unauthorized use of your logo and branding. You can use reverse-image search engines or automate monitoring with Red Points.
Combosquatting
With combosquatting, attackers add words or phrases to a well-known domain name so it seems related to the original brand. For example, a fraudulent website might use a domain like apple-support.com to impersonate a legitimate service from Apple.
What to look for: Monitor for domains that use your name plus navigational or transactional words like shop, deals, support, or login.
Typosquatting
The typosquatting tactic employs frequent URL misspellings that users are either likely to make on their own or are unaware of. For example, an attacker might use “Hundai” in a domain to lure people who misspell Hyundai.
What to look for: Think about common misspellings of your brand and consider registering these domain names. Our AI-powered brand protection platform can search domain registrations for possible typosquatters automatically.
Similar top-level domain exploitation
Cybercriminals register a domain using the same second-level domain (SLD) as a target brand but with a different top-level domain (TLD). If the original website is example.com, attackers might register example.net, example.org, or example.biz. This attack is effective because people often remember the brand name but not the TLD.
What to look for: Search for registrations of your brand with different TLDs. Better yet, register multiple TLDs like .net and .org to limit access.
IDN homograph attacks
Attackers register domain names using characters from different scripts, such as Cyrillic or Greek, that visually resemble Latin script characters. For instance, a Cyrillic ‘a’ might be used in place of the Latin ‘a’, to make the domain look exactly like the legitimate one.
What to look for: Homograph attacks can be harder to spot since they look like your brand’s name. In this case, our platform can locate homograph urls in domain databases quickly with the help of automation rules.
SEO poisoning
Attackers use black-hat SEO techniques to boost their sites ahead of legitimate brands. Techniques involved include keyword stuffing with popular brand names, creating backlinks from other deceptive sites, and exploiting trending topics to drive traffic.
What to look for: Keep an eye on search rankings for your branded terms to see if malicious sites are ranking unusually high.
AI-generated content
Advanced AI technologies can generate high-quality, relevant articles, fake user reviews, and other types of content that imitate legitimate websites. This content improves the site’s SEO and also helps to deceive visitors into believing they are interacting with a genuine brand.
What to look for: Scanning a suspicious website with an AI detector can confirm your beliefs that the site may be fake.
Why proactive domain protection is critical
Domain names and the websites they host are critical to an organization’s online reputation and brand. They are often the first point of contact between your organization and a prospective client, business partner, or employee. Cybercriminals are fully aware of this and are attempting to exploit the present situation by launching similar domain name attacks.
It’s not enough to be aware of the issue and wait for attackers to exploit it. You have to proactively safeguard your brand. This means putting monitoring tools in place to know when someone is using a variation of your domain without authorization. Acting on potential threats early can prevent your customers from ending up on a phishing site or purchasing counterfeit goods.
Automating domain monitoring with Red Points
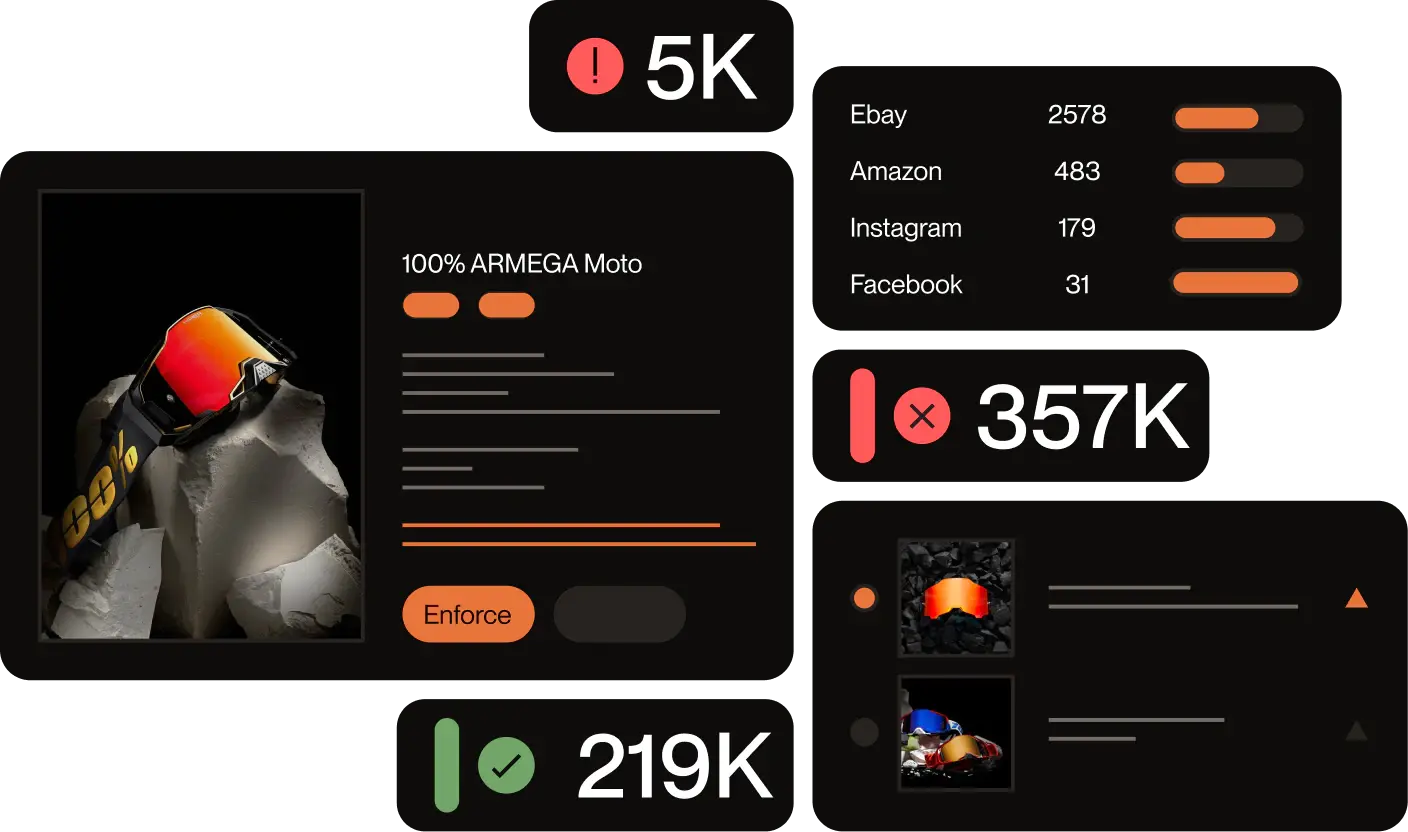
Instead of manually searching for lookalike domains that could use any of the techniques above, you can automate domain protection with Red Points. Our domain management software detects infringing sites and facilitates their suspension or removal.
We understand brands can have many domains, so our domain management system secures your portfolio across territories and can help register new ones to fill gaps. Domain impersonators are creative and act fast, so it’s important to meet the threat head-on.
Building a robust lookalike domain defense strategy
So what can you do to defend your domain online? Start by building a foundation by expanding your domain portfolio and strengthening your online presence.
- Register similar domains: Register common misspellings, typos, and variations of your brand’s domain name to prevent others from doing so. Consider registering your brand across multiple top-level domains (TLDs), such as .com, .net, .org, etc.
- Use trademark protections: Ensure your brand name is registered as a trademark. This provides legal grounds for taking action against lookalike domains.
- Strengthen your brand’s online presence: Optimize your site so it ranks high in search, and maintain verified social media profiles across major platforms, which makes it easier for users to identify legitimate content.
- Educate your audience: Improving audience awareness can help your customers avoid scams. Use blogs, videos, and social media to educate customers and partners about the risks of lookalike domains and how to recognize your official website.
Set up real-time lookalike domain alerts
Once you have your foundation of domain defense in place, you’ll want to monitor for infringements. With Red Points, you can get alerts when our systems find an infringing domain in real-time. We detect fake sites that use typosquatting, combosquatting, homoglyph attacks, and more. This means bad actors have less time to take advantage of your brand and deceive users into using a fake site. Real-time notifications let you take action right away.
Leverage automated takedown processes
Automated takedowns go hand-in-hand with domain alerts. Once we identify a risky domain, our platform can automate the rest of the enforcement process. This includes sending takedown notices and liaising with domain registrars to deactivate fraudulent domains efficiently. However, every step is backed by human oversight to ensure accuracy and compliance. We can follow through with the full process and even help you take legal action against offenders. Or, if you’d prefer to handle the issue yourself, we can support you as you take the next steps.
Your brand can maintain ongoing protection with Red Points’ experienced customer success team, which helps identify gaps in your domain strategy and suggest improvements based on existing data to ensure that you always stay one step ahead of cybercriminals.
How to monitor and detect lookalike domains – 4 effective strategies
- Register your trademark
You can monitor your domain on your own in a few ways. For example, registering your trademark with the Trademark Clearinghouse can alert you when someone attempts to use it during a new TLD launch.
2. Leverage domain monitoring tools
You can also use domain monitoring tools like DomainTools, Farsight, and WHOIS Monitoring to track and identify registrations similar to your brand.
3. Set up Google Alerts
Another option is to use Google Alerts for your brand name and its variations. You’ll receive an email when someone mentions your brand or publishes content on a site similar to your domain.
4. Use Red Points’ AI-powered monitoring service
Using Red Points’ AI-powered monitoring service is the simplest way to stay ahead of attackers profiting off your domain. Our custom algorithms don’t sleep. We analyze over 2.7 billion monthly data points to uncover fake sites as soon as they appear. And since we have partnerships with popular content platforms, hosts, and registrars, we can remove infringements fast. In fact, our system removes 86% of infringements automatically.
Success stories: Defending against lookalike domains
Based in Portland, Oregon, KEEN is a favorite footwear brand for outdoor enthusiasts. Unfortunately, domain attackers set their sites on the brand and attempted to profit from its growth.
KEEN’s leadership noticed fake websites appearing almost out of thin air. These sites would copy KEEN’s logo and visuals and funnel customers through Facebook ads. KEEN’s customer service team received 1,400 complaints in a single day as customers fell for the scam.
By partnering with Red Points, KEEN was able to identify lookalike domains and fake sites to remove them at the source. KEEN used our AI detection and removal system to take down thousands of online infringements. Ultimately, this protected the company’s customer base from further harm and safeguarded KEEN’s reputation.
What’s next
Similar domain name attacks continue to be an increasing threat—we’ve seen standalone website infringements grow by 161% since 2022. It just takes one malicious website to erode years of trust you’ve built with customers. Scammers can take advantage of a similar domain name in many ways, as we’ve covered. This includes typosquatting, copycatting, and SEO poisoning.
Bad actors will use any tool they can find to get an edge. That’s why being proactive in your defense is so important. Companies around the world trust Red Points to monitor, detect, and remove lookalike domains automatically. Instead of spending precious time manually searching for domain lookalikes, let our AI-driven platform eliminate them in real-time.
Don’t wait for brand impersonation to snowball into a bigger issue. Schedule a demo today to protect your customers and stay ahead of attackers.