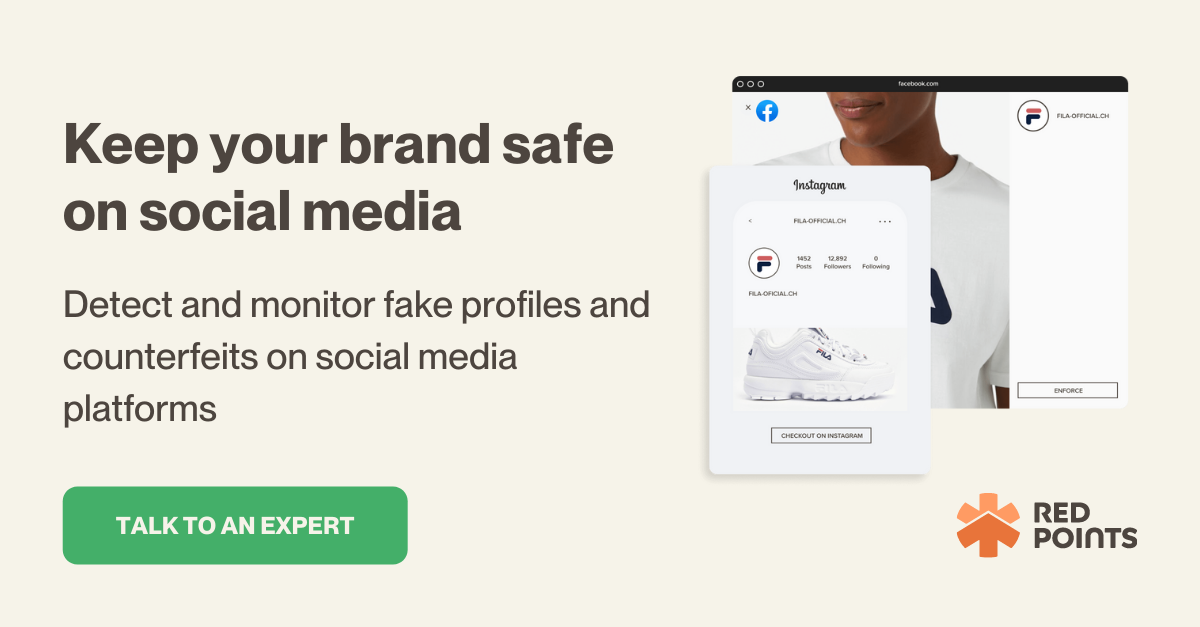
The massive popularity of social media can bring so many benefits for both businesses and individuals. Yet, naturally, they also invite bad actors or cybercriminals to these platforms looking for victims to exploit.
Among the many different forms of malicious attacks targeting social media users, social media identity theft—also called social media impersonation—is among the most popular and dangerous forms.
Social media identity theft can cause severe damage to your brand when not properly managed. In this article, we’ll explain how social media impersonation works and what you can do to protect your business from these identity theft attempts.
By the end of this guide, you’d have learned about:
- What is social media identity theft?
- What type of information is commonly stolen from social media accounts?
- What to do if you or your business becomes a victim of social media identity theft?
- Best practices to protect your brand from social media identity theft.
Without further ado, let us begin this guide with the basics.
What is social media identity theft?
Social media identity theft, also known as social media impersonation, is the malicious practice of impersonating a brand’s identity on social media.
This is commonly done by using the brand’s photos, videos, content, and personally-identifiable information to create a fake social profile impersonating the company.
Why do cybercriminals perform this type of attack? As with any other form of identity theft, there are many ways to monetize social media impersonation, which naturally makes it attractive to cybercriminals.
Below are just a few examples of how identity theft on social media can be monetized:
- Phishing or social engineering attempts to manipulate the victim’s followers into thinking the fake profile belongs to the real individual or organization and then tricking this victim into divulging their sensitive information, discrediting the owner of the impersonated brand, or even asking the victim for money
- Setting up a fake online store and driving the victims to visit this online store from the fake social media profile.
- Spreading malware (including ransomware) to victims
- Using the account to spread fake news to cause confusion and unrest
This is not an exhaustive list, and there are numerous other ways bad actors can exploit their victims using fake social media accounts.
What matters is that social media identity theft can be very dangerous for the business the account is impersonating and the victims tricked by these fake accounts.
Left unchecked, social media identity theft can cause:
- Long-term or even permanent reputational damage
- Potential financial and legal repercussions
- Your consumers can get scammed, compromising your credibility
- Compromised accounts due to leaked credentials
This is why learning how to identify and prevent this type of threat is crucial, especially for businesses with any form of social media presence.
How can social media lead to identity theft?
Due to the social nature of social media, a high volume of sensitive and personally-identifiable information is circulated on these platforms every single day. This information is accessible to everyone, including bad actors that will use this information to perform identity theft.
Not to mention, creating new accounts on major social networks (Instagram, Facebook, Twitter, etc. ) is very easy and free. This means that attempting a social media impersonation attack on these social platforms is also very easy.
On the other hand, with the increased global popularity of social media, a successful social media impersonation attempt can be very profitable, and there are more opportunities than ever to steal identities on social media.
In short, the low difficulty and high potential profitability attract bad actors to perform identity theft and other related malicious attacks.
How does social media identity theft affect businesses?
In this web 3.0 age, social media has become a critical part of many businesses’ marketing strategies. Social media platforms such as Instagram, Facebook, LinkedIn, and even YouTube can offer businesses great opportunities to engage their target customers, build credibility, and promote their products or services.
However, this phenomenon also creates a significant vulnerability for businesses against social media identity theft. Malicious parties may use various techniques to impersonate a brand’s identity on social media, which can significantly impact a brand’s online presence, reputation, and even financial stability.
Here are some common examples of how different social media identity theft techniques affect businesses:
- Account takeover
In this type of social media identity theft, a malicious party (i.e., a hacker) gains access to a business’s social media account using various methods (phishing, brute force attacks, credential stuffing, etc.)
Once the malicious party has access to the account, they can change the account information (i.e. with derogatory content), post unauthorized content, or even delete the account.
- Impersonation
In this type of identity theft attack, a malicious party creates a fake social media account impersonating the brand’s legitimate account. This technique is also often known as brandjacking.
The malicious party can then use this account to post damaging or fraudulent messages (or content) while impersonating the brand and may trick customers, partners, or stakeholders into making unauthorized purchases or providing sensitive information.
- Malware distribution
A malicious party may post a link to a fake website, social media account, or even an email impersonating a brand (in the case of an email, it can also include an attachment). When users click on this link or download the attachment, their devices will be infected with malware that can disrupt operations, steal confidential/private information, or cause other damage.
These social media identity theft attacks (and more) can have a significant negative impact on businesses, including but not limited to:
- Reputation damage: fraudsters and hackers can post damaging content that can harm the business’s reputation in a long-term way that can be challenging to undo. This can result in the business losing trust and credibility among customers, partners, and other stakeholders.
- Revenue loss: social media impersonation attacks may lead to financial loss for the business, and may damage a business’s relationship with customers, partners, and other stakeholders.
- Legal repercussions: businesses may be held liable for damaging, defamatory, or discriminatory content posted by a cybercriminal. These legal issues may also result in fines, legal fees, and other expenses.
- Loss of control: a hacked social media account or a fake website gaining traction may mean the business loses control over its online presence. When, for example, a hacker responds to customer inquiries inappropriately using a stolen social media profile, it can lead to various issues and especially a loss of control over the brand’s reputation.
What should I do if my brand becomes a victim of social media identity theft?
While ideally, you’d want to prevent being a victim of social media identity theft, complete prevention is admittedly very difficult.
If you find fake social profiles in your name or impersonating your brand, don’t panic, and you can take the following action:
- Facebook: check out our Facebook’s guidelines for reporting impersonating pages here.
- Twitter: see how to report fake Twitter accounts impersonating your business here.
- LinkedIn: you can report fake profiles on LinkedIn here.
- Instagram: learn how to report fake accounts impersonating your business on Instagram here.
- Pinterest: follow this steps to report fake Pinterest profiles here.
- Snapchat: visit Snapchat’s safety reporting page here.
If you are a US-based business or a business with operations in the US and are currently a victim of social media identity theft (or other forms of online/offline identity theft), then it’s important to file a report to the Federal Trade Commission. Fortunately, doing this is very easy, and you can simply go to IdentityTheft.gov and follow the on-screen instructions to file your report.
How to protect your brand from social media identity theft?
While 100% prevention against social media identity theft is very difficult, there are ways to lower the risks, especially by being careful about what you share and whom you share it with on social media.
With that being said, here are a few actionable tips on how to protect yourself and your information on social media:
- Register your IP rights
The first thing you should do is register your business’s intellectual property (IP) rights.
Your IP rights will be the legal basis for protecting your brand on social media and will give you the exclusive right to use your brand name, logo, slogan, design, and other distinctive brand elements that uniquely identify your brands, products, or services.
Make sure to register your intellectual property rights in the countries (or regions) where you operate or plan to operate in the future, so you can prevent others from using and taking advantage of your brand identity without your permission.
With the registered IP in place, in the event that there’s an infringement, you can take the necessary legal action, including against those who try to pass off their products/services as yours.
Not to mention registering your IP rights can also help you establish and increase your brand recognition and value in the market.
- Establish control over your social media pages
In this social media age, it’s possible that your brand’s official pages on social media are the main communication channels with your customers and followers. It’s also quite often that these pages will be the first touchpoint—and first impression—many people will have of your brand.
With that being said, make sure to establish control of your social media pages by keeping them verified, always up-to-date, and engaging.
Take the necessary steps to verify your pages with social media platforms to get those blue check marks (or other badges/marks) that confirm your page’s authenticity. This will significantly help in differentiating yourself from fake pages that may try to imitate your brand.
Then, aim to regularly post valuable and relevant content that showcases your brand’s values and unique personality. Maintain two-way interactions with your audience by promptly responding to their comments, feedback (including and especially negative ones,) and questions.
- Implement a social media policy and approval process
Assuming you’ll have employees or partners who will post on your brand’s behalf on social media, make sure to establish clear and consistent social media guidelines and an approval process.
The social media policy should clearly define how your brand should be represented on social media, controlling aspects like a style of writing, tone, type of content published, hashtag usage, and so on.
Having a consistent and, if possible, distinct social media presence will also make it more difficult for bad actors to impersonate your brand.
- Leverage social media platforms’ reporting features
Most major social media platforms offer mechanisms to protect their users from harmful or infringing accounts or content: blocking, hiding, flagging, reporting, or even removing content or accounts from the platform.
Leverage these safeguard mechanisms to your advantage. For example, make sure to report any accounts and content offering counterfeit products under your brand name (or likeness.) Doing so will also help in building trust between your brand and the social media platform. Once they notice you as a credible source of reports, they may also provide faster responses in the future in the event of more reports and takedown requests.
- Act quickly to suspected breaches
If your business suspects that its social media account has been compromised, make sure to act quickly to regain control of the account.
This may include reporting the breach to the respective social media platform right away, resetting passwords, and removing unauthorized posts as soon as possible.
- Consider using third-party solutions
Using a third-party provider to protect your business against social media identity theft can be highly beneficial if your brand is continually targeted by scammers. Third-party providers have the necessary expertise and resources to monitor social media platforms for any signs of impersonation or brand infringement, something that can be challenging to manage in-house.
Red Points’ Social Media Protection Solution provides real-time detection, reporting, and removal of fake social media accounts while ensuring that the necessary evidence is gathered for legal action if needed.
What’s next
Among the many different types of cybersecurity threats, social media identity theft is among the most potentially detrimental due to the global scale of these social networks. Fake accounts impersonating your brand can negatively affect your brand’s reputation and may hurt your revenue.
The bad actor can then use this fake social media account to sell counterfeit goods or launch phishing scams that may affect your prospective or existing customers, hurting your reputation in the process.
To prevent these impersonation attacks, consider investing in a Business Impersonation Removal Solution. This will help to protect your organization, avoid costly legal issues and stay one step ahead of cybercriminals.