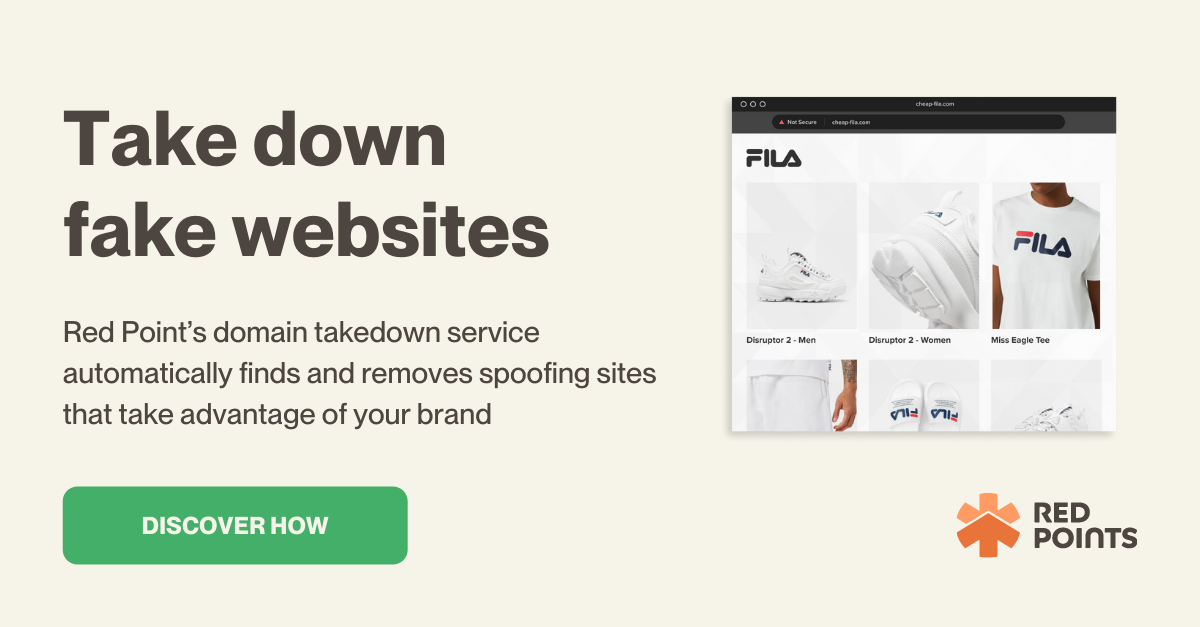
In today’s digital age, businesses are becoming increasingly reliant on their online presence to reach customers and drive sales. However, with this reliance comes the risk of cyber threats such as typosquatting.
Typosquatting is a form of online fraud where cyber criminals register domain names that are similar to established brands or trademarks but with small typos or variations, with the aim of redirecting traffic to malicious websites or stealing sensitive information.
In this blog post, we’ll explore typosquatting in more detail and discuss strategies for detecting and mitigating this threat to your brand.

What is typosquatting?
Typosquatting is a type of cybercrime in which bad actors register domain names with purposeful misspellings of the names of well-known websites. Bad actors use this tactic to divert unsuspecting users to malicious sites on the internet.
These scams often target unsuspecting consumers in one of the following two ways:
- Via direct traffic, meaning that they depend on users to misspell the domain name of the real website they want to visit (such as basebook.com rather than facebook.com). Once the user is on the website it could potentially be an exact clone of the real site, but its only intention is for you to reveal private information, such as your email and password or your financial data.
- Via phishing scams. These can be elaborate scams that include the impersonation of a business or an individual to reach out to users in an effort to fool them. These scams can be particularly damaging to businesses’ reputations because the victims of these scams may hold the actual business responsible more than the bad actor themselves.
The effectiveness of these both scams relies on the quality of the fake website that the bad actor has created by typosquatting on your domain address. It could easily happen that a fake website appears the exact same as your real website, so you can imagine how easily an unsuspecting user could fall for the scam.
How to detect typosquatting
Typosquatting is a growing threat to businesses today; these fake domains can cause serious harm to businesses if not addressed immediately, including brand degradation, losses in revenue, and damaged customer relationships.
To counter this threat, businesses need to monitor their domains and identify any suspicious activity before it’s too late. By doing so, businesses can mitigate the risks to their brand’s reputation and revenue.
Businesses can employ several methods to detect typosquatting attempts.
Firstly, they can conduct regular manual searches of their domain names using variations in spellings and top-level domains. However, this approach can be time-consuming and may not be comprehensive enough to identify all potential threats.
The most effective method for typosquatting detection is a scalable solution such as Red Points’ Impersonation Removal software. Red Points’ software offers a more efficient and effective way to detect and mitigate typosquatting threats. Our advanced AI-based technology uses machine learning to continuously monitor domain names and detect suspicious activity across various online platforms. With our Impersonation Removal services, businesses can rest assured that their digital assets are being actively protected against all types of brand abuse, including typosquatting.
How to report typosquatting?
The Anticybersquatting Consumer Protection Act (ACPA) was passed in 1999 in the United States to create legal recourse for trademark and name infringements that manifest themselves in the registration, sale, or use of domain names that are confusingly similar to, or dilute the strength of, an existing trademark or name.
This regulation was enacted to stop “cybersquatters,” or those who register domain names containing trademarks with the goal of selling them to the trademark owner or a third party rather than using them to host a genuine website.
Since the passage of the ACPA, domain name owners have had the burden of proving their good faith use of the domain and that it is not confusingly similar to an already established trademark, brand, or website.
You might potentially seek arbitration under the Uniform Domain Name Dispute Resolution Policy (UDRP). The procedure might lead to the transfer of the domain name to you if harmful conduct is identified. You will need evidence of your trademark rights and the duration of your trademark use in order to win a UDRP. Before contacting the domain name owner or adopting a recovery strategy, it is important to take into account the aforementioned reasons.
Google can also be contacted for complaints. You may notify Google about certain forms of abuse involving domain names registered through Google Domains. A support agent looks at each report of abuse individually in the form of a ticket. Domains may be stopped, and the user may be alerted through email if the user’s actions violate Google’s Terms of Service.
Google Domains is solely responsible for handling domain name registrations. Domain name system-based abuse may fall within their purview. Misuse that takes advantage of several web services, including content hosting, may nevertheless proceed undetected.
E-mail registrar-abuse@google.com if you see any phishing activity with a domain name registered through Google Domains.
If you know the domain’s or host’s registrar, you may report suspicious activity by visiting their website and clicking the “report abuse or fraud” link, which should be located on the Contact page or in the footer. If you’ve exhausted all other options, you can send an email to abuse@ + the company’s primary website address (for example, abuse@hostingcompany.com).
Don’t forget to add as many of the specifics you’ve learned as possible, such as:
- Justifications for your suspicions that the site contains false or harmful content, including relevant URLs (if not on the homepage)
- Screenshots
- headers and body for any suspicious or offensive emails
If all fails, litigation can be an alternative approach that involves taking the offending party to federal court is an option if counterfeiting or other criminal activity has caused damage.
What can businesses do to prevent typosquatting?
Losing customers due to typosquatting is bad for business. If visitors are taken advantage of on fake domains, traffic to your site might be redirected elsewhere, and your reputation could be damaged.
Businesses should thus take measures to prevent the growth of typosquat domains.
Here are six strategies that businesses may use to counteract them:
1. Register domains that are similar. If you want to prevent users from going to typosquat domains instead of your own, you should register comparable domains before typosquatters do. This contains both common typos and intentional variations like adding or removing hyphens. In addition to generic top-level domains like.com and.org, it also supports country-coded TLDs (e.g. .co.uk). After registration, these domains can be pointed to your primary domain and website.
2. Create a trademark registration with TMCH. To prevent cybersquatting, ICANN (Internet Corporation for Assigned Names and Numbers) recommends that businesses register their trademarks with Trademark Clearinghouse (TMCH).
3. Obtain an SSL certificate immediately. An SSL certificate is one of the best ways to establish a website’s credibility. All claims made by a website need to be verified. The presence of advanced certifications (which the vast majority of businesses should have) also demonstrates the reliability of the site and the safety of its data transmissions. A secure sockets layer (SSL) certificate is a good indicator that you are on a legitimate site and not a typosquat.
4. Inform the relevant stakeholders. If a company has reason to think that someone is impersonating them or is planning to do so, it should notify its stakeholders rather than try to tackle the issue of typosquatting in the dark. Reputational harm may be mitigated via open communication with customers, staff, and other stakeholders regarding the existence of harmful typosquat websites.
5. Introduce a complaint to the World Intellectual Property Organization. Trademark holders have recourse against typosquatters under the World Intellectual Property Organization (WIPO)’s Domain Name Dispute Resolution Policy (UDRP). With this process, domains can be recovered if the complaint can provide evidence of the following:
- Their trademark is identical to, or very close to, the registered domain name.
- There is no evidence that the registrant is actually connected to the domain in any meaningful way.
- Bad faith usage of the domain name.
6. Take use of ICANN’s tracking system. ICANN stands for Internet Corporation for Assigned Names and Numbers. The Trademark Clearing House is a service provided by ICANN that allows website owners to monitor the usage of their trademarks across all top-level domains. All trademarks, whether based in the United States or elsewhere, are eligible for this service.
These six tips can help businesses protect themselves from the harm caused by typosquatting.
How does Red Points’ typosquatting detection work?
Red Points’ Impersonation Removal software leverages advanced technology to monitor the web for frauds that are using your brand’s likeness as part of a scam. Our state-of-the-art platform grants its users a detailed overview of our impersonation removal process and is built to save them and their businesses both time and money.
The software carries out impersonation removal with three unique steps: detect, validate, and enforce.
The first step, detection, relies on our machine learning platform that uses a bot-powered search to find any potential cases of impersonation online. Once detected these potential cases of impersonation are collected and listed on our platform for users to review.
This is the second step in the process, validation, which is when the user validated whether or not each case is in fact impersonation. While the only manual step in our process that requires action from the user, our platform has smart rules that can enable users to automate this stage in the process if they choose.
This ultimately brings us to the third and final step in the process, which is enforcement. This stage is handled completely by Red Points on behalf of the user. We initiate the takedown process for our users and follow through on the process until the impersonation has been removed from the web.
Once an instance of impersonation is taken down, for instance in this case a fake domain, Red Points will notify the user and provide a detailed report on the incident. However, in addition to this report Red Points’ platform also provides users with a number of detailed data reports that can be tailored to the needs of the user.
What’s next
Although laws in the United States and other countries can help protect websites against typosquatters, the burden remains on the right holder to enforce their IP, which can sometimes be a time-consuming and expensive process.
Proactive impersonation removal solutions are preferable because of the time and effort required to track down and remove fake websites. Your brand will be safe from cybercriminals like those who engage in typosquatting, phishing, malware, and the like if you employ the services of a reputable service provider like Red Points.
If you don’t take action against phishing sites using your brand name, you risk losing the confidence of your site’s users.
See how Red Points’ Impersonation Removal software can protect your business from typosquatters.