As businesses become increasingly reliant on technology, they face a growing number of cybersecurity threats. Among these threats are social engineering scams, which manipulate people into divulging sensitive information or performing actions that compromise their security.
It was estimated that cyber-attacks resulting from social engineering techniques increased by 270% in 2021.
These scams can result in significant financial losses, reputational damage, and even legal ramifications for businesses.
In this article, we discuss:
– What social engineering scams are
– The different types of social engineering scams
– How businesses can protect themselves from these scams
– How Red Points’ software can bolster security measures to further safeguard businesses against these malicious activities
What are social engineering scams?
Social engineering scams are fraudulent schemes that exploit human psychology, rather than technology, to deceive people into revealing sensitive information or granting unauthorized access to systems. These scams often rely on a scammer impersonating a trusted individual or entity, such as a colleague, customer, or service provider. The goal of these scams is typically to gain access to sensitive data, commit fraud, or steal company resources.
Phishing
A phishing scam is a widespread social engineering scam that involves bad actors sending deceptive emails or text messages to unsuspecting targets. These messages often appear to be from reputable organizations or individuals, such as banks, colleagues, online retailers, or government agencies. The main goal of phishing is to trick recipients into revealing sensitive information, such as login credentials, financial details, or personal information. This is typically achieved by urging the target to click on malicious links or download infected attachments. To make their messages more convincing, scammers often use a sense of urgency or authority, threatening the target with negative consequences if they fail to take the requested action. By recognizing the telltale signs of phishing and implementing strong email security measures, businesses can reduce the risk of falling victim to this scam.
Pretexting
Pretexting is a type of social engineering scam where scammers create a fabricated scenario or assume a false identity to manipulate their targets. The scammer may impersonate someone with authority, such as an executive, a police officer, or a representative from a financial institution, to establish trust with the target. The ultimate goal is to persuade the target to divulge sensitive information or perform actions that compromise their security. Pretexting often involves extensive research on the target, using information gathered from social media or other online sources to enhance the scam’s credibility. To protect against pretexting, businesses should implement policies and training to educate employees on the risks, verify the identities of callers, and safeguard sensitive information.
Baiting
Baiting is a social engineering scam where scammers entice victims with the promise of something valuable, such as free software, exclusive content, or monetary rewards. This “bait” is used to lure victims into taking actions that lead to security breaches, such as downloading malware-infected files, providing login credentials, or visiting compromised websites. Scammers often rely on the target’s curiosity or greed to manipulate them into taking the bait. To defend against baiting, businesses should educate employees about the risks associated with unsolicited offers, encourage skepticism, and establish guidelines for handling suspicious communications.
Quid pro quo
Quid pro quo scams involve scammers offering a benefit or service in exchange for sensitive information or access to the target’s systems. This type of social engineering scam often targets individuals in a professional setting, where the scammer pretends to be a colleague, a vendor, or a service provider. The scammer might offer technical support, free gifts, or exclusive access to valuable resources in return for the target’s cooperation. Targets may be enticed by the prospect of gaining something valuable and unwittingly divulging sensitive information or granting unauthorized access. To prevent quid pro quo scams, businesses should establish clear policies for sharing sensitive information, verify the identity of third parties, and provide employee training on social engineering risks.
How to protect your business from social engineering scams
To defend against social engineering scams, businesses can adopt several strategies, including:
Employee training and awareness programs
One of the most effective ways to protect your business from social engineering scams is by investing in employee training and awareness programs. Employees are often the first line of defense against these scams, so it’s essential to ensure that they are well equipped to identify and respond to potential threats. Training programs should focus on common social engineering techniques, such as phishing, pretexting, baiting, and tailgating, and teach employees how to recognize and report suspicious activities. Regularly updating and reinforcing this training can help keep employees vigilant and maintain a strong security culture within the organization.
Customer education and communication:
Educating your customers about social engineering scams and providing them with resources to protect themselves can be an effective method for safeguarding your business. By raising awareness among your customer base, you can reduce the likelihood of them falling victim to scams that could ultimately impact your business. Communicate regularly with your customers through newsletters, blog posts, or social media updates, sharing tips on how to recognize and avoid social engineering scams. Encourage customers to report any suspicious activities to your organization, enabling you to take swift action and minimize potential damages.
Implementing multi-factor authentication (MFA)
Multi-factor authentication (MFA) is a security measure that requires users to provide two or more forms of identification to access sensitive information or systems. By implementing MFA, you can significantly reduce the risk of unauthorized access to your business’s data and systems, even if an attacker successfully obtains a user’s login credentials through social engineering. MFA can be implemented using various methods, such as text message verification, biometrics, or hardware tokens, making it more challenging for attackers to bypass your security measures.
Monitoring and assessing online presence
Perform manual searches online to identify fake websites, phishing emails, or social media profiles that may be targeting your business or customers. Regularly assessing your online presence can help you spot potential social engineering threats and take appropriate action to mitigate risks. Consider using tools like Google Alerts to monitor mentions of your brand online and stay informed about any potential issues that may arise. Additionally, ensure that your organization’s domain name and social media accounts are properly secured to prevent unauthorized access or impersonation.
Registering your intellectual property (IP)
Another clear way to prevent your business from being targeted by social engineering scams is by registering your IP with relevant government agencies. While this may not prevent these types of scams from ever occurring, registering your IP will allow you to take legal recourse against any bad actor that is using your IP as part of your scam. This not only allows you to protect your business and its image more effectively, but it can also protect your customers as well by giving you a path to quickly take down infringers without any drawn-out processes.
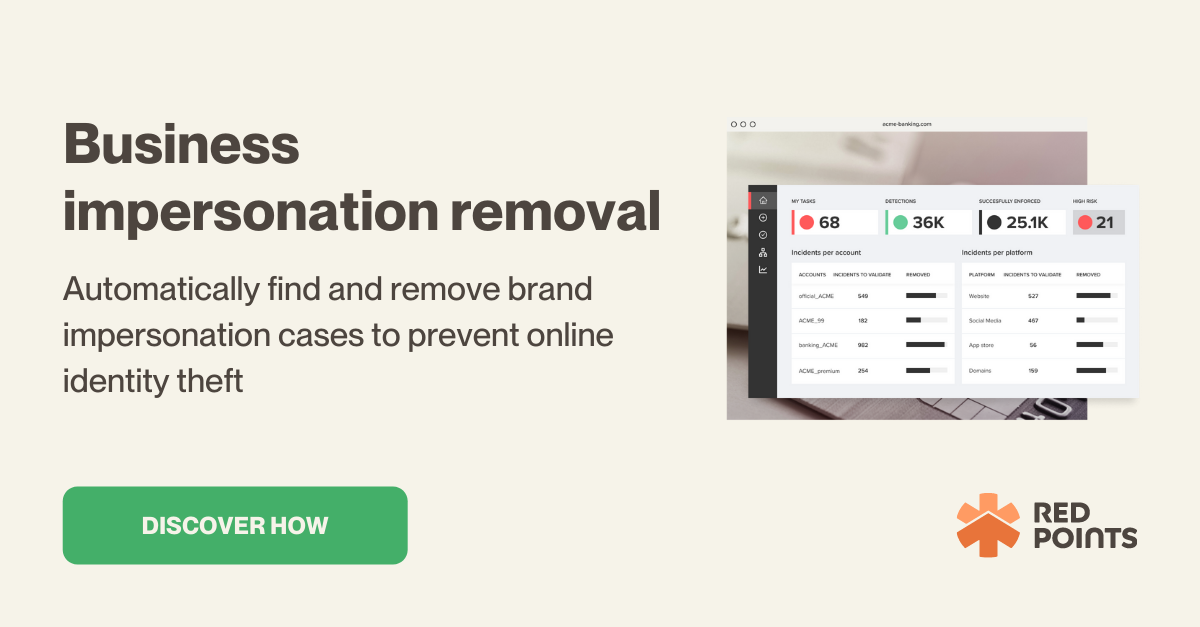
Using Red Points’ Impersonation Removal Software to protect your business
Red Points’ Impersonation Removal software is an advanced solution designed to help businesses safeguard their online presence by detecting and removing fraudulent impersonations of their company, brand, or employees. This powerful tool enhances your existing security measures and strengthens your overall security posture by proactively addressing potential threats posed by scammers.
How Red Points’ Impersonation Removal Software works:
Monitoring and detection:
Utilizing advanced algorithms and AI technology, Red Points’ Impersonation Removal Software continuously monitors the internet, including websites, social media platforms, and online marketplaces, for instances of impersonation. The software scans for unauthorized use of your company’s name, logo, or employee information that may be used by scammers to deceive customers or gain unauthorized access to sensitive information.
Validation and reporting:
Once potential instances of impersonation are detected, Red Points’ software validates the authenticity of the content and provides detailed reports on the identified infringements. This enables businesses to stay informed about potential threats and take appropriate action to protect their online presence and reputation.
Takedown and removal:
After detecting and validating instances of impersonation, Red Points’ software automates the takedown process, ensuring the rapid removal of fraudulent content. The platform can issue takedown notices to the hosting providers of the infringing websites or social media platforms, effectively removing unauthorized content and minimizing the risk of your customers or employees falling victim to scams.
Ongoing protection:
Red Points’ Impersonation Removal Software provides ongoing protection for your business, ensuring continuous monitoring and swift removal of fraudulent impersonations. This proactive approach helps maintain a strong security posture and minimizes the risk of your business being targeted by scammers.
By integrating Red Points’ Business Impersonation Removal service into your security strategy, you can effectively protect your business from the risks posed by scammers impersonating your company or employees. This advanced solution complements your existing security measures and provides an additional layer of protection against the ever-evolving landscape of online threats.
What’s next
Social engineering scams pose a significant threat to businesses, making it crucial to implement robust security measures and educate employees on how to recognize and respond to such threats. Ignoring the risks associated with social engineering scams can result in serious consequences for businesses and their customers which will only get worse over time.
By investing in Red Points’ Impersonation Removal software, businesses can effectively bolster their security measures, protecting their reputation, finances, and customer trust.