Impersonation fraud happens when you disclose personal and financial information to someone pretending to be your bank, a family member, a business partner, or even a brand doing a giveaway.
These scams generally start with a phone call, a text, a direct message on social media, or even an email that seems legitimate. In many cases, imposters will also create fake social media accounts or fake websites just to mislead customers into spending money on a scam or disclosing their personal information.
In this article, we discuss:
- What is impersonation fraud?
- How can you prevent impersonation fraud?
- How can you report impersonation fraud?
What is impersonation fraud?
In an impersonation fraud scam, an impersonator typically solicits a fake payment or personal data request from a victim. For the most part, a criminal will pose as someone with the power to demand money or personal information from another party (e.g., directors, executives, or even vendors). Scams can start in a variety of ways, including over the phone, by email, fax, or text message. Wire transfers are the most common method of transferring payments quickly in these types of scams and often once a wire is sent the fraudster will completely cut contact.
Today, impersonation fraud takes on many different forms, not only can impersonation fraud apply to singular people that are victims of identity theft, but it can also apply to entire businesses. In fact, one of the most impactful types of impersonation fraud is actually business impersonation, which can, again, take many forms…
These cases of fraud could range from phishing scams to fake websites, counterfeit listings, or fake social media accounts. The reason why these types of fraud are so damaging is not only because of the financial and personal information stolen from your potential customers but also the damage it can do to your relationship with your customers. Over time, this type of impact on your business’s customer relationship can actually have an immense impact on your overall revenue.
What are the most common ways that impersonation fraud can happen to you as an executive?
Scammers are taking advantage of people’s fear and anxiety over potential economic changes brought on by the COVID-19 pandemic, leading to a substantial increase in impersonation fraud.
After factoring in the most recent statistics from the Social Security Administration, it becomes clear that the stated expenses have climbed by an alarming 85% year over year, reaching a total loss of $2 billion between October 2020 and September 2021.
Since the beginning of the pandemic, there have been 12,491 reports of government impersonation fraud and 8,794 cases of business impersonation fraud related to COVID.
How does business or executive impersonation fraud happen?
Vendor fraud
The term “vendor fraud” refers to unethical business actions that can be undertaken to obtain personal gain by a single vendor, several suppliers, or an individual working in an organization’s accounts payable department (AP).
To put it more plainly, it is a sort of fraud that includes making up a recipient’s or a vendor’s account details to redirect the money fraudulently. Fraudulent activity involving payments can be carried out by:
- One or more employees
- One or more vendors
- Collusion between the vendor(s) and the employee (s)
- An unknown outside source alters a vendor’s payment information.
Because of the complexities involved, detecting vendor fraud may be challenging, leaving businesses open to potentially catastrophic losses. One recent case of vendor fraud allowed a man to swindle major businesses like Google and Facebook out of more than 100$ million after targetting them in a phishing scheme.
Executive impersonation
To conduct an executive phishing attack, a hacker poses as a high-ranking executive, such as the CEO or CFO, to trick their targets into giving over confidential information or initiating a financial transaction.
An example of a business email compromise (BEC) assault is executive phishing. This sort of attack is characterized by the fact that the perpetrators falsely appear to be a trusted entity and seek to steal financial or data information by using context, persuasion, and urgency.
Because of their specificity, lack of dangerous payloads, and social engineering, these attacks can bypass conventional defenses. Whaling, CEO fraud, and executive impersonation are all names for executive phishing.
What are the different types of business impersonation fraud?
Businesses can be targeted by impersonators in a number of different ways, many of which can leave a business with a tarnished reputation and a disgruntled customer base. Depending on the nature of your business, you may be more susceptible to one form of impersonation than another, but that does not mean that the risk is zero. Because of that, business owners should consider monitoring mediums for impersonation that they may not initially consider. These mediums include social media, fake websites, and of course fake apps.
Impersonation fraud on social media
Social media is a haven for scammers and bad actors because it is filled with potential victims. While most platforms like Facebook, Instagram, TikTok, or Twitter do have some authentication processes in place when creating an account. Despite these processes, such as email verification or verification badges for business or celebrity accounts, there are still ways bad actors manage to fool users.
One of the most famous examples of this was a fake Twitter user impersonating Elon Musk was able to fool users into wiring over funds so that “Elon” would double their ‘investment’ and send it back to them. This scam managed to steal an incredible amount of money, including one UK man who lost over £400,000 after falling victim to this impersonation fraud.
Despite the example above being a notable celebrity, this type of scam often impersonates brands’ official social media accounts and can message users directly in an attempt to retrieve private information, such as personal or financial data. These impersonators can also launch fake advertisements using a brand’s name and likeness to fool its victims into a scam that steals their logins or financial information. In these cases, victims are often left scratching their heads while getting upset with the actual brand that was being impersonated, even though they had nothing to do with the scam.
Impersonation fraud on the web
Fake websites also referred to as rogue websites or impersonating websites, can be particularly damaging to businesses from a revenue perspective. These cases of impersonation fraud typically involve typosquatting or other underhanded tricks which can fool potential customers to think they are on your brand’s official website when they actually aren’t. In these cases, an impersonator may create a website with a name that is extremely similar to the one your business uses, perhaps only switching a letter in the domain name or the domain suffix at the end of the URL. Then these impersonators clone your business site entirely, meaning that any customer that enters this site incidentally may not even recognize it’s a fake until it’s too late.
These fake websites then monitor the users’ actions closely, recording any financial information that is entered if they try to make a purchase or even username and password information if the victim tries to log in on that fake website. Once this valuable information has been captured by the scammer they can either go on to commit more fraud using the users’ financial information, or they may sell all that data in the internet’s black market.
While this type of impersonation fraud can do significant damage if left unattended, if you know how to take down fake websites, the process of taking them down can be rather easy.
Impersonation fraud using fake apps
Fake apps are actually a major channel for impersonators to funnel victims into their scams. These apps can replicate businesses’ real apps in terms of design and structure, fooling users into using their payment system which will funnel users’ funds straight into the pockets of the impersonator.
However, even if your business does not use a mobile app, that doesn’t mean your customers can’t be fooled into downloading what they think is your app. These types of scams can have a big impact on your business’s reputation as the negative reaction from customers that fall victim to these scams may hold the business responsible.
Fortunately, businesses can protect revenue and their reputation by having the right protective software, such as Red Points’ Mobile App Protection Software.
How can businesses prevent impersonation fraud?
Cybercriminals have a field of opportunity when it comes to executive impersonation. Why? It’s normal for bosses to send demands for large amounts of money or important data to their staff, and these requests are often followed without hesitation.
Providing proper safety for clients online has become financially vital, given the ongoing digital interactions between companies and consumers. As a result of phishing assaults perpetrated by hackers, organizations must take greater measures to defend their brands. It is possible to do this in a variety of methods, including:
- First and foremost, cybersecurity and marketing teams must have a mutually beneficial relationship. You can tell if emails sent from your brand’s domain are malicious or not if you often communicate with your customers (or other internal departments). This limits the potential for a phishing scheme to succeed both internally with employees and externally with your customers.
- To keep consumers, business partners, and workers from getting emails from impersonators, use the DMARC email validation system. This system is meant to discover and prohibit the delivery of all unauthenticated mail.
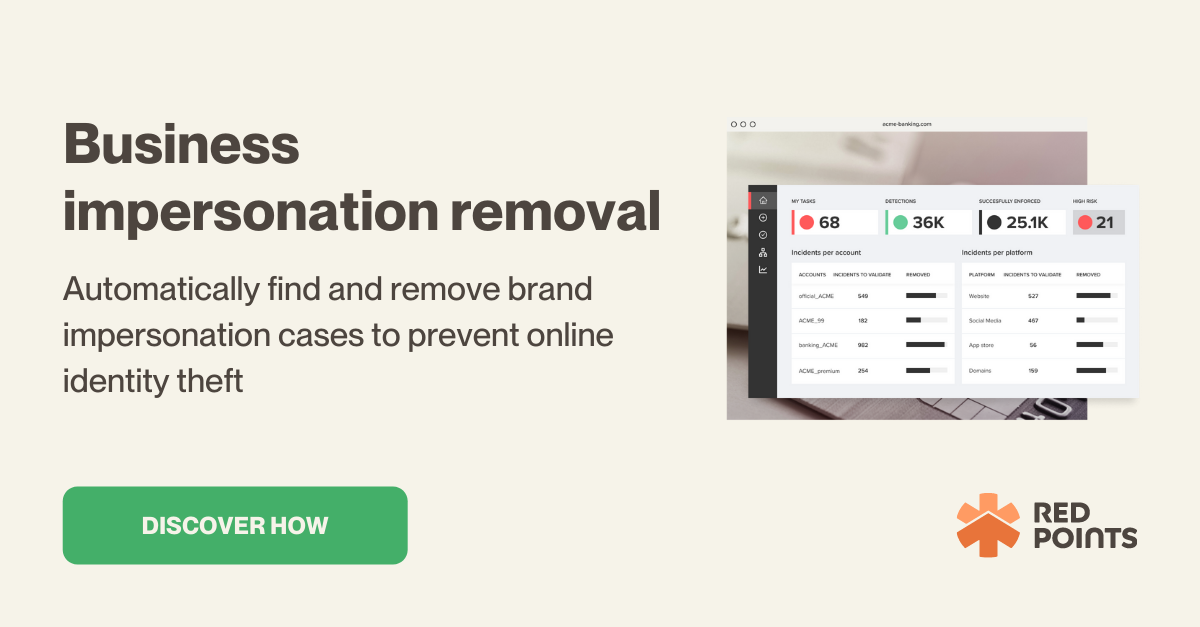
- Proactively search for and remove domains and impersonation from the web. Impersonation Protection Software like Red Points can be used to accomplish this. Machine learning combined allows this solution to detect impersonation attacks early on to protect your brand integrity and revenue.
- All accounts should have two-factor authentication. At the very least, the hacker will not have easy access to your account, making executive impersonation fraud far less likely.
- You can’t assume your entire team knows what they’re doing at all times. All security procedures must be documented so that any employee who encounters a possible danger can spot it. This is useful in the event of a breach. Your staff will know exactly what they need to remedy the issue.
You can remove as many fake accounts, applications, websites, and domains as you like with the help of Red Points’ automatic brand Impersonation Removal software.
Red Points automates social media account monitoring, enables the removal of fake profiles, and enhances search results through the use of machine learning that recognizes trends and responds appropriately.
Our automated services for protecting brands from counterfeiting consist of three stages.
- The first step is a bot-driven search to locate any impersonations quickly.
- Second, we use image recognition to weed out hundreds of cases of brand imitation.
- Third, everything that might endanger your consumers is immediately removed.
How can you report impersonation fraud?
Reporting impersonation fraud as an individual
Scam reports are collected by the Federal Trade Commission (FTC). The Federal Trade Commission may be contacted online or by phone at 1-877-382-4357 to report the fraud (9:00 AM – 8:00 PM, ET). You can file a complaint with the FTC if you’ve been a victim of any of the following common scams:
- Messages exchanged through telephone
- Emails
- Scams in the field of IT
- Scams perpetrated by counterfeits
- Fake bank accounts
- Requests that you hand them money (check, wire transfers, gift cards)
- Loan and scholarship fraud
- Offers of cash, prizes, and grants
Reporting impersonation fraud as a business owner
As a business owner, detecting impersonation is a difficult task that requires constant vigilance. These tye of impersonation fraud scams can vary greatly, ranging from fake ads on social media to entire fake websites created specifically to redirect customers’ funds. Protecting your business from impersonation fraud not only can protect your revenue, but also your customers as well. Meaning that you’ll be able to maintain a positive and loyal customer base who can advocate for your business.
Business owners hoping for a high-quality automated service should consider using the Impersonation Removal software offered by Red Points. With Red Points, you can shut down an infinite number of fake accounts, applications, websites, and domains with just a few clicks.
It works to uncover impersonations in seconds with a bot-powered search by sifting through thousands of potential brand impersonation infringements. The machine learning technology works by employing keyword recognition and allows users to automate the submission of takedown requests to whatever they define to the machine learning technology as a potential infringement.
What’s next
Cybercrimes involving the impersonation of brands are becoming an increasingly pressing issue for companies all over the world. The potential consequences are loss of money, faith in the brand, and even consumer loyalty. As a result, businesses need to adopt preventative measures to address this issue and eliminate any infractions as soon as they become aware of them.
The Impersonation Removal solution offered by Red Point can efficiently avoid, identify, and put an end to any and all types of business impersonation assaults, which in turn may help protect your brand reputation.
See how Red Points’ Impersonation Removal Software can help your business deal with impersonation fraud targeting your business or its customers.