Intro
In 2026, brand protection is essential to preserving brand integrity. As brands expand across online marketplaces, social commerce, and paid ads, exposure to counterfeits and impersonation has become constant. Both Red Points and Marqvision offer solutions to mitigate these threats, but their approaches differ. This comparison explains why choosing the right platform matters for your customer trust and growth outcomes, analysing how each vendor handles channel coverage, enforcement limits, and support.
Comparison table (matrix)
| Feature | Red Points | Marqvision |
| Unlimited takedowns | ✅ Flat-fee model with unlimited detections and takedowns | ❌ Volume depends on package limits |
| Always-on protection | ✅ Marketplaces, social media, web, domains, ads, and apps | ✅ Broad multi-channel coverage |
| Priority enforcements | ✅ Platform APIs, priority escalation, adaptive enforcement | ⚠️ Not disclosed |
| Dedicated specialists | ✅ Fully managed service with end-to-end support operated by IP experts who manage detection and enforcement, with flexible validation ownership. | ✅ Analysts available |
| AI risk prediction | ✅ Incident prediction and seller risk models | ❌ Rule-based prioritization |
| Domestic China | ✅ China-domestic platforms coverage (Goofish, Pinduoduo, WeChat, Douyin) | ✅ Korea-focused coverage |
| Seller clustering | ✅ Cross-channel seller intelligence (2.7B datapoints) | ✅ Seller network intelligence |
| Gray market | ✅ Automated gray market, unauthorized sellers and parallel imports removal | ✅ Gray market monitoring |
| Public reviews | 100–250 | <50 |
Core difference
The core difference lies in the level of expertise and scalability: Red Points’ solution offers highly scalable protection with 10 years of refined enforcement. Marqvision is ideal for companies just starting brand protection efforts, with a particular emphasis on the Korean market.
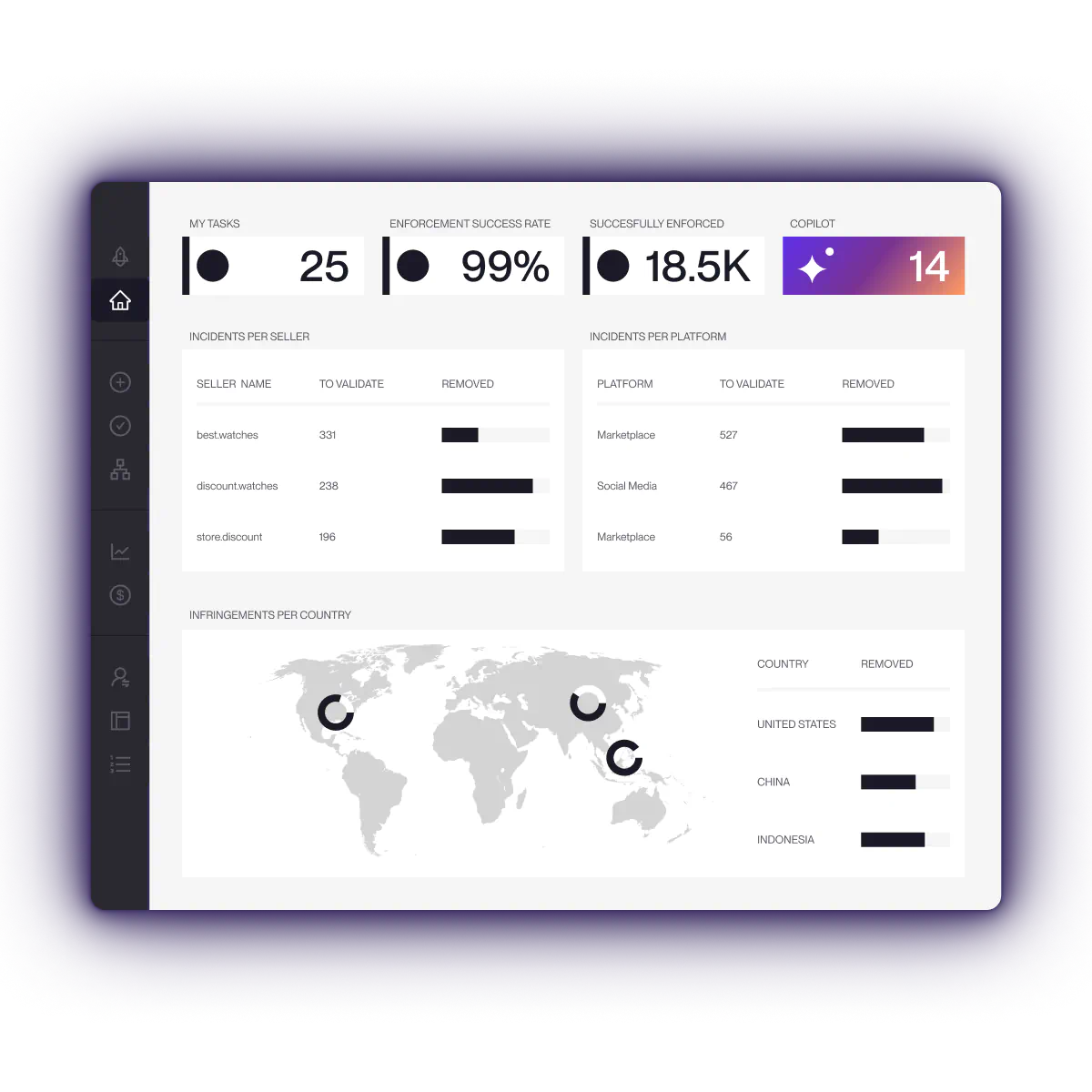
Red Points offers end-to-end AI-led protection, fully managed by experts — continuously adapting detection logic, automation rules, and enforcement to evolving infringement tactics. Red Points combines operational maturity with scalable technology to protect brands of all sizes: SMEs (35% of its client base), mid-market (35% of its client base) companies, and large enterprises (30% of its client base). It is built on a database of 2.7 billion monthly data points and over 50 million infringers, allowing it to integrate AI for incident prediction and high-risk seller prioritization. Its philosophy is based on “always-on” protection where detections and takedowns are not capped by analyst hours, enforcement packages, or credit systems.
Marqvision is a newer company (founded in 2020) that offers a suite of brand protection services with a particular focus on Asia. While it provides a good variety in channel coverage and allows for smart rules to customize automated enforcement, its model is often tied to package and credit limits rather than unlimited scale.
Detection & monitoring
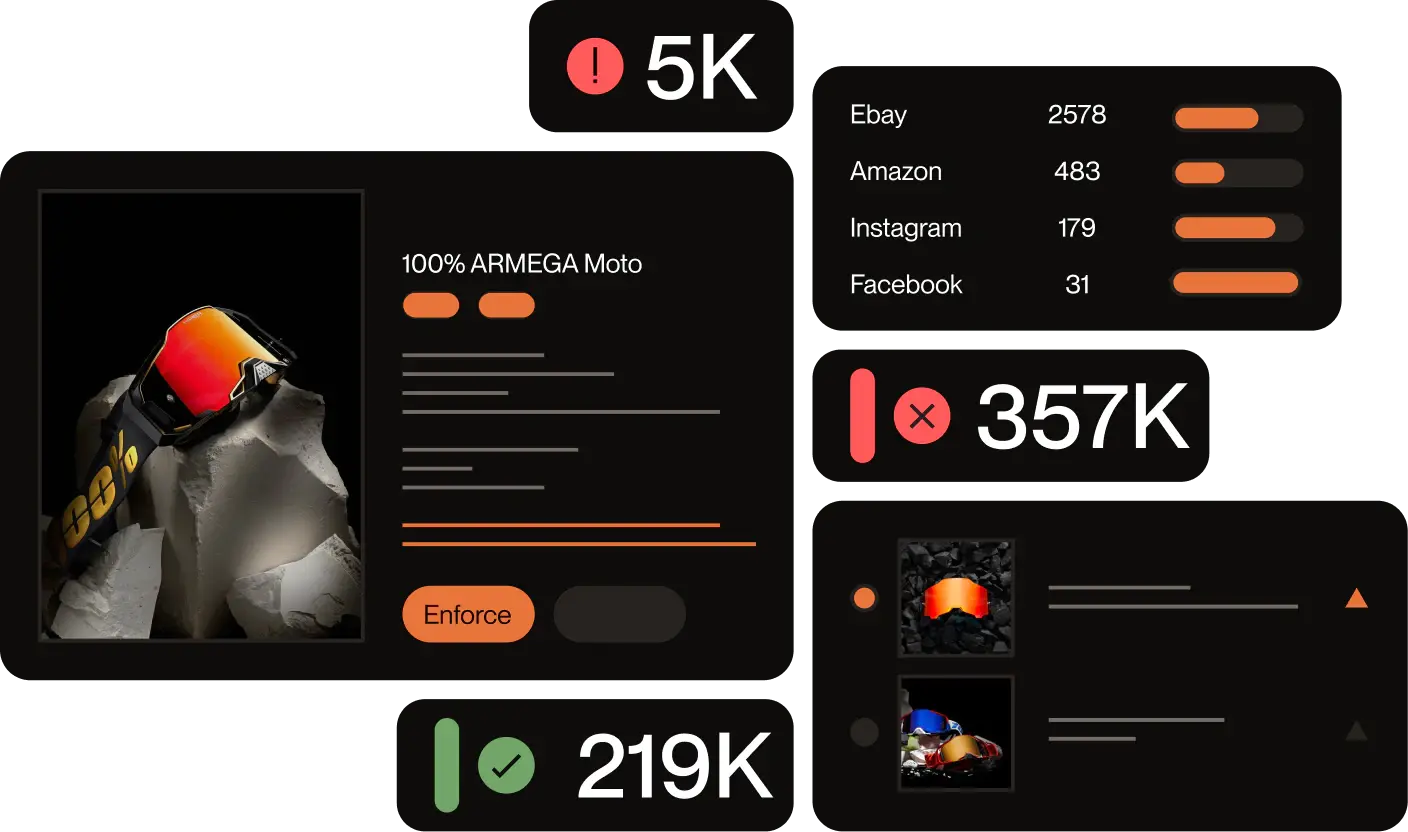
Red Points monitors intellectual property across all digital channels, including marketplaces, social media, websites, deep web, and ads. A key strength is its cross-channel intelligence, which uses seller clustering to identify networks of infringers rather than just isolated listings. It also provides specialized coverage for China’s domestic marketplaces that are often inaccessible from outside the mainland.
Marqvision removes fakes on over 1,500 marketplaces and has a specific strength in social media image protection. Like Red Points, it provides China-domestic coverage with investigative support. However, its detection capabilities are currently missing coverage for some channels outside of e-commerce, such as rogue websites.
Enforcement & scalability
Red Points offers unlimited takedowns across all channels. The platform is designed to handle high volumes without bottlenecks; every case is reviewed, risk-scored, and refined through AI and expert oversight. Crucially, enforcement is not limited by analyst hours, ensuring consistent protection even during spikes in infringement.
Marqvision allows for automated enforcement through smart rules, but its enforcement capacity can be tied to package limits and scalability issues. This means the volume of takedowns you can execute, as well as the speed in which they are addressed, depends on the plan you purchase. Enforcement capacity may vary during peak periods depending on these limits and manual validation requirements.
Customer experience & support
Red Points provides a fully managed AI platform. Every protection program is fully operated by experts using predictive AI custom to every brand, battle-tested playbooks refined over a decade, ensuring continuous validation, optimization, and strategic enforcement. Additionally, Red Points offers a Revenue Recovery Program to recover tangible revenue through high-scale litigation.
Marqvision offers support where analysts are available and provides offline support for investigations and litigation. They also offer trademark management services (registration and renewal), which Red Points handles through industry partners rather than in-house.
Pricing model
Red Points uses a flat-fee model that includes unlimited detections and takedowns by channel. This provides cost predictability for fast-growing brands, as the price does not increase with the volume of enforcement.
Marqvision’s pricing depends on the number of detections and enforcements you want. While often affordable, this model means costs are variable based on the volume of activity and the specific package limits selected.
Final verdict
Which platform is right for you?
Choose Red Points if:
- You are a global brand seeking end-to-end scalable protection.
- You need unlimited takedowns and a predictable flat-fee pricing model to avoid cost volatility.
- You require fully managed protection (operated by IP-Ops experts) included in your plan.
- You want predictive, seller-focused prioritization to address the highest-impact threats first and enable deeper enforcement when needed.
- You want access to a Revenue Recovery Program to recover funds from infringers.
Choose Marqvision if:
- You are a small team or company just starting brand protection efforts.
- You’re testing brand protection impact on a smaller scale.
- You are focusing specifically on the Korean market.
- You need a solution that includes trademark registration and management in-house.
FAQ section
1. Which platform offers better cost predictability? Red Points. Red Points uses a flat-fee model that includes unlimited detections and takedowns. This allows brands to scale protection without cost volatility, even during seasonal spikes in infringement. Marqvision’s pricing depends on the number of detections and enforcements, which can vary.
2. How do the enforcement models differ? Red Points offers advanced AI-driven prioritization combined with 10+ years of platform priority enforcement and expert teams, ensuring that high-risk threats are tackled first,, utilizing AI trained on 2.7 billion data points to assess risks. Marqvision’s enforcement volume depends on the package limits of the plan you select, which may restrict capacity during peak periods.
3. Do both platforms cover China? Yes. Both platforms offer coverage for domestic China. Red Points covers platforms like Goofish, Pinduoduo, WeChat, and Douyin. Marqvision also provides China domestic coverage with investigative support.