Today, the freemium business model has become increasingly popular within the software industry. It is convenient for consumers and it has proved to be rewarding for many software companies.
Unfortunately, the convenience and profitability of freemium software have also attracted many digital pirates. Freemium software piracy is now a major threat to software companies and consumers. So, what is the impact of freemium software piracy and how do you prevent this alarming trend from damaging your software business?
In this blog, we explore freemium software piracy and how to combat it by highlighting a few key topics including:
- Why is piracy a problem for freemium models?
- What’s the impact of freemium software piracy today?
- Examples of freemium software piracy
- What laws protect software against piracy?
- How to combat freemium software piracy?
- Why is a dedicated anti-piracy solution a game-changer?

Why is piracy a problem for freemium models?
Freemium, a combination of “free” and “premium”, is a modern business model that has become particularly popular in the digital age. Under the freemium model, a business provides free products, features, or services to the consumer to set up the foundation for monetization in the future.
Around 83% of the highest-grossing social media apps have a freemium model. The typical freemium conversion rate is between 2%-5% but some of the most popular freemium platforms like Slack and Spotify have conversion rates exceeding 30%.
Modern digital piracy seeks to take advantage of this model. Piracy is a problem for freemium models for the following reasons:
- Unchecked piracy undermines consumer trust. Users will be unlikely to give over their details or sign up for paid services further down the line if they believe there is a risk of being targeted by scammers.
- It is an easy way for pirates to elicit customer information. Freemium models draw a wide user base, including users who might be reluctant to sign up for a paid service. The barrier to entry is low. Pirates can take advantage of this convenience and collect sensitive information without users feeling like they’ve been scammed.
- It is expensive and time-consuming to combat freemium pirates. Scammers will steal intellectual property, mislead consumers, and taint a brand’s image. However, in a digital world, it is expensive and impractical to manually pursue and take down all these scammers, particularly if you are running a freemium model business.
What’s the impact of freemium software piracy today?
Software piracy occurs when software is copied, modified, distributed, sold, or used without permission and a proper license. Software is a key resource for businesses across a wide variety of sectors and it is a hotbed for piracy.
The most recent Global Software Survey conducted by the BSA revealed that 37% of software worldwide is unlicensed. The cost of freemium software piracy in particular can be felt deeply across the industry in several ways.
- Reputational damage
If you allow pirates to steal, distribute, and sell your freemium software the reputation of your software and your business will suffer. The brand image you have cultivated will be undermined if you are shown to have weak security.
Equally, the reputation of your software products will suffer if consumers know that there are easily accessible pirated versions online. As your reputation suffers so will your connection with users and your ability to reach new users. It can also become more difficult to collaborate with partners who will be reluctant to expose themselves or their assets to any piracy risks.
- Poor user experience
Often scammers steal software without understanding or caring about how to support the way users may use the software. They cannot provide updates to improve the user experience and they also remove the ability for companies to provide support.
Pirated software lacks quality control. Consumers who download the software are more likely than not to find it frustrating and dissatisfying. This will impact customer service teams as they will have to deal with an influx of complaints concerning problems that are largely out of the control of the software company.
- Lost revenue
The Global Software Survey also revealed that the commercial value of unlicensed software worldwide was $46.3 billion. This is representative of how freemium software piracy can impact your ability to monetize your assets and maintain steady levels of revenue.
Examples of freemium software piracy
Bad actors use a variety of piracy techniques to take advantage of freemium software on the market. From theft to unauthorized modification, here are a few of how software piracy is conducted today:
- Copying and distributing legally acquired freemium software without permission
With freemium software, there are no upfront costs. This makes it easier for scammers to legally acquire the software. From there they will then copy and distribute the software in violation of licenses, end-user agreements, and copyright law. They can use this method to gain sensitive user information.
- Selling modified or cracked versions of software
Scammers will also gain access to freemium software to modify it. They may install their malware or modify it to suit their interests. Most licenses will prohibit such modifications as they put consumers at risk, undercut monetization opportunities, and cannot be supported.
Software cracking involves removing copy protection from a piece of software. This is a violation of copyright law. Cracked versions of freemium software often include malware, unwanted adverts, and outdated features. If they are allowed to proliferate on the market they will undermine the freemium software business model.
To learn more about the legal use of software and the general fight against software piracy, check out the Federation Against Software Theft (FAST).
What laws protect software against piracy?
In the US, the Copyright Act of 1976 protects against the unauthorized copying or distribution of a work of authorship. In 1983, this law was extended to protect computer programs and software. Therefore today, a software programmer or company automatically owns the copyright of any software they write (this copyright extends for 70 years after the death of the author).
The wording under federal copyright law is as follows, “Users may not create a copy of a piece of software for any other reason other than as an archival backup without the permission of the copyright holder.”
Some key elements of the law protecting software:
- Companies or individuals that break this law can be penalized as much as $150,000 for each case of software copyright infringement.
- More serious criminal copyright violations are considered felonies and offenders can receive up to 5 years in prison. The fine for selling illegal software can be as high as $250,000.
- The statute of limitations to file a software copyright infringement lawsuit is 3 years after the incident.
How to combat freemium software piracy?
- Establish software licenses and keys
Software licenses allow individuals or organizations to use software in ways prescribed by the software publishers. An end-user license agreement (EULA) outlines what the user can and can’t do with the software. Usually, these licenses will say that the user can use the software but they cannot distribute it, sell it, or modify it without permission.
You can also combine this method of protection with a license key. Essentially, your freemium software will be locked when installed and can only be opened if the correct license key or password is entered. This helps to restrict your assets to people who have paid for your software.
- Software watermarks
Beyond copyrights and license keys, you can also combat freemium software piracy by watermarking your software products. A watermark can be used for proof of authorship and to identify the original purchaser.
This will help you detect and track illegal distribution of your freemium software. Watermarks can sometimes also serve to deter scammers from pirating the software in the first place because they will know that their theft will be easy to track.
Why is a dedicated anti-piracy solution a game-changer?
The best way to combat software piracy is with a sophisticated technological solution. It is almost impossible to properly protect your business’s assets from digital pirates with manual methods of defense. It is time-consuming, costly, and inefficient to search the entire web for freemium software pirates on your own.
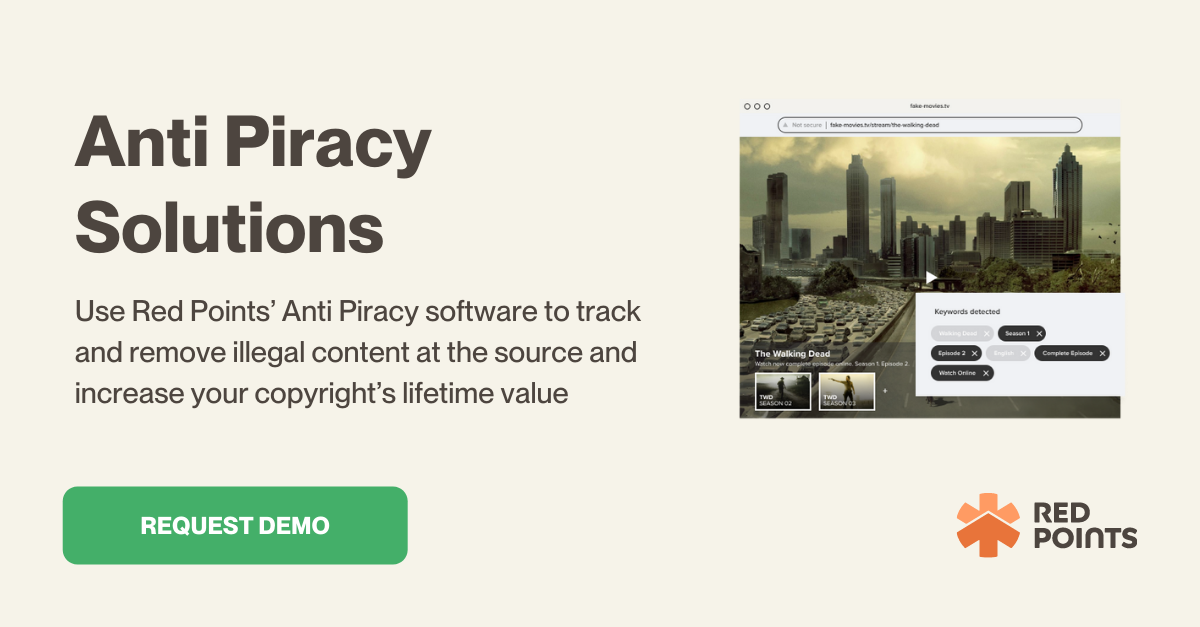
Red Points’ Anti-Piracy solution is the ideal tool to allow businesses to track and remove pirated software and safeguard intellectual property assets. Powered by automation and supported first-class tools, our anti-piracy solution will empower you to track, find, and take down freemium software pirates wherever they operate.
Here’s how it works:
1. Track
This phase involves the systematic scanning of the internet to identify unauthorized copies of freemium software. Leveraging advanced automated bots, the system combs through various online platforms including apps, social media, file-sharing sites, and cyberlockers. This thorough tracking ensures comprehensive detection of pirated copies across the digital landscape.
2. Validate
The next step is to validate the identified potential infringements. This process involves confirming whether the suspected copies are indeed pirated. The validation can be conducted either manually or through an automated system set to specific criteria, aiming for precise identification.
3. Hide
The validated pirated content is then subjected to a delisting or hiding process. This stage aims to reduce the visibility and accessibility of unauthorized software, thereby mitigating its potential impact. The promptness of action in this stage is crucial for effective piracy control.
4. Enforce
In this stage, specific actions are taken against the confirmed instances of piracy. These actions may include legal proceedings, sending takedown notices, or working with hosting services to remove the content. Continuous enforcement is vital for addressing both new and existing piracy issues.
5. Measure
The final stage involves measuring and analyzing the outcomes of the anti-piracy efforts. This includes the use of analytics tools to evaluate the impact of the strategies implemented, tracking the volume of identified and resolved infringements, and using these data to inform and refine ongoing anti-piracy measures.
Our anti-piracy solutions protect software, apps, video games, press and publishing, e-learning info products, TV on-demand, and cinema. Across a wide variety of environments, Red Points’ software works with precision and efficiency to protect assets from digital piracy.
What’s next
Unfortunately, freemium software piracy is here to stay. For software companies, this means that investing in the best protection is vital. If you fail to act now, you will become vulnerable to the schemes of digital pirates who want to attack your revenue, your IP, and your users.
The most effective way to fight piracy is to proactively invest in the best technological solutions. Manual searching and reporting is simply too slow and expensive. An automated, specialized anti-piracy tool will give your software business the ability to search widely, quickly detect pirates, and aggressively pursue any infringers.
To learn more about how your business can mitigate the impact of freemium software piracy, talk to one of our experts.