If you’ve recently experienced a downturn in sales, slowed growth or an inability to reach your customers, you may be being undercut by scammers and bad actors. Unfortunately, today there are many fraudulent apps on third-party mobile app marketplaces whose sole purpose is to take away customers and revenue from legitimate brands.
So how do you stop this? Below is a guide to help you learn how to detect malicious apps to ensure that you are capable of protecting your customers, revenue and reputation.
In this blog we will explore:
- What are malicious apps?
- What is the impact of malicious apps?
- Why 3rd party apps stores represent a growing security risks for brands
- How Red Points can help detect malicious apps
What are malicious apps?
Malicious apps appear in various sinister forms across a wide variety of app marketplaces. The intent of these malicious apps is always to steal, mislead and damage.
When consumers are using third-party app stores they are vulnerable to stumbling upon a number of these malicious apps. Here are some of the most common examples of the types of malicious apps:
Malware app
According to the Federal Trade Commission (FTC), malware includes “viruses, spyware, ransomware and other unwanted software that gets secretly installed onto your device”. As soon as the malware is downloaded onto your device whether it is a phone, tablet or laptop, scammers can use this software to steal sensitive information, send unwanted ads, make your device vulnerable to further attacks and demand fraudulent payments.
Payment scam apps
Payment scams are some of the most damaging ways malicious apps will attempt to take advantage of users. Apps will pretend to be enabling you to send money to a legitimate payee but will in fact be directing the bank transfer to a fake account. The user will have lost their money before they know it and it will be very hard to retrieve. These kinds of scams will also be harmful to brands because users will quickly lose trust and become wary of using any app-related payment system.
Counterfeit apps
Phishing is a form of cybercrime in which scammers attempt to trick users into clicking a bad link that will direct them to a fake website or make them download malware. One of the key features of counterfeit apps is that they will include phishing features and attacks that will take users away from the app and on to some other dodgy website. They can be quite subtle, misleading and nightmarish for uninformed consumers.
Repackaging attack
This is a very common type of attack on Android devices. In such an attack, attackers modify a popular app downloaded from app markets, reverse engineer the app, add some malicious payloads, and then upload the modified app to app markets.

What is the impact of malicious apps?
Malicious apps will impact two main areas: Revenue and Reputation. Both areas will be key to your legitimate app’s growth and potential. Therefore it is important to understand how fake apps impact these areas and what you can do to overcome the negative effects.
Revenue
When fraudulent apps redirect payments to illegal sites, brands will lose out on revenue. Every fraudulent sale to a malicious app amounts to revenue that a legitimate brand is missing out on. Legitimate app owners should therefore rightly feel aggrieved when marketplaces allow malicious apps to run riot on their platforms. While Apple claims to have stopped nearly $1.5 billion in fraudulent app transactions on their app store in 2021, this level of fraudulent activity is also an indication that millions of dollars of revenue are being lost every year to malicious apps.
Reputation
Equally damaging is the loss to reputation. Malicious apps will distort user perception and you will start to see negative reviews that have nothing to do with your brand. This will impact the ability of your brand to organically grow the app through positive word-of-mouth. If your brand is constantly associated with malware, phishing and payment scams, you will gain a reputation for being untrustworthy and faulty. On your own, this will be difficult to recover from.
Why 3rd party apps stores represent a growing security risks for brands
Detecting malicious apps is relatively easy when they are all funneled through one app store. But, what if they are spread out across a diverse array of third party app stores? This is the issue facing brands today following the implementation of the EU’s Digital Markets Act.
While third party app stores present a valuable opportunity for quirky app makers and interested consumers, they also represent fresh hunting ground for scammers and makers of malicious apps. Apple has always blocked third-party app stores from operating on its devices in order to protect their own revenue and uphold their strong security standards. However the Digital Markets Act, which entered into force on November 1, 2022, will force Apple to change their stance in European markets.
Traditionally, the app store has played an important role in ensuring the integrity and security of iOS devices. Every app must follow Apple’s guidelines. However, this new legislation will likely increase the trend of ‘sideloading’ – allowing apps to be loaded onto devices from sources not approved by Apple or other device owners. Apple has often said that sideloading, in this case via third party apps, will degrade security and expose their users to security risks.
Allowing third party app stores to grow in prominence on millions of devices may also lead to an increased threat of brand impersonation. The majority of third party app stores will have a lower barrier to entry and less security infrastructure than industry leaders like the Google Play Store or Amazon’s App Store. This means it will be easier for scammers to introduce malicious apps and create dodgy app impersonations.
It will also potentially be difficult for users and brands to detect these malicious apps across a variety of third party app stores. If these malicious apps install malware or include phishing scams, this will lower the security of devices, cause consumers to lose trust and harm legitimate brands.
How Red Points can help detect malicious apps
Below we’ve outlined the steps of the process we use to detect, and deal with, malicious apps:
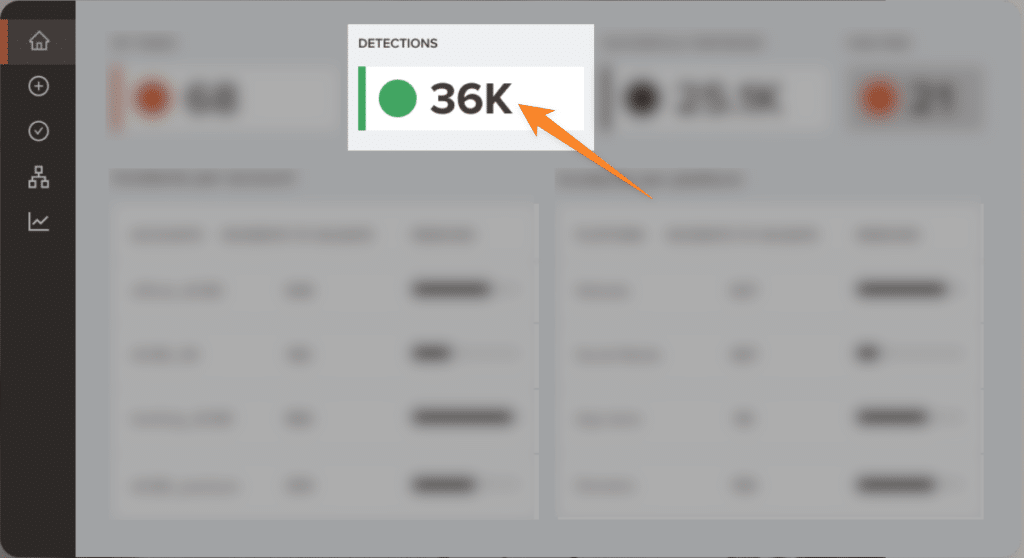
Monitoring & Detection
Red Points monitors the entire online world looking for scammers and fraudsters that may be eating away at your profits and stealing your IP. To find unauthorized apps our bots will crawl official and third-party app stores every day. Over time, machine learning makes these bot searches more accurate and we are able to find malicious apps more quickly.
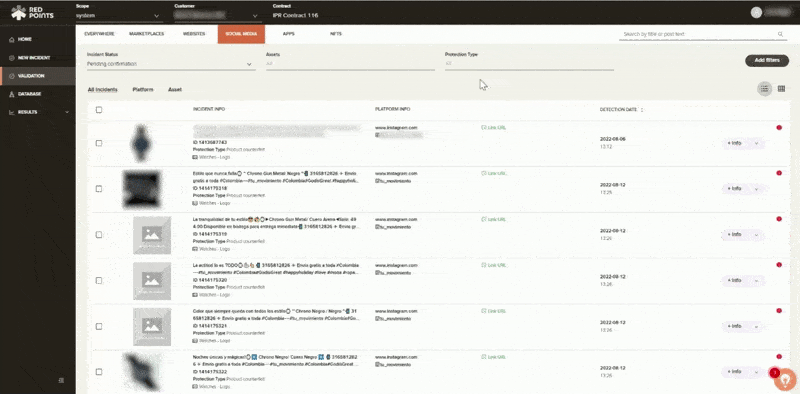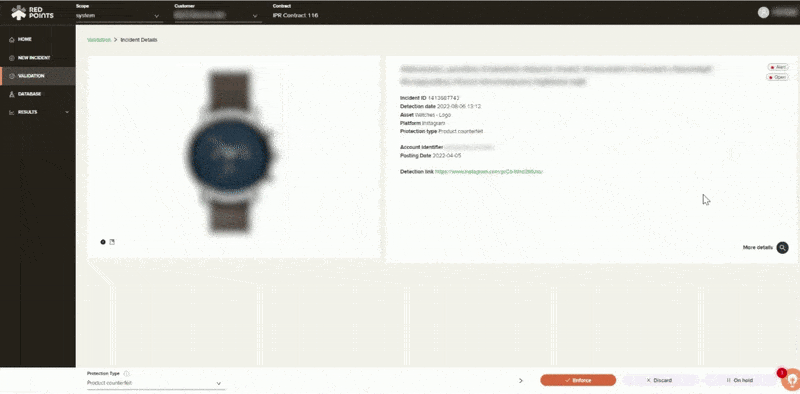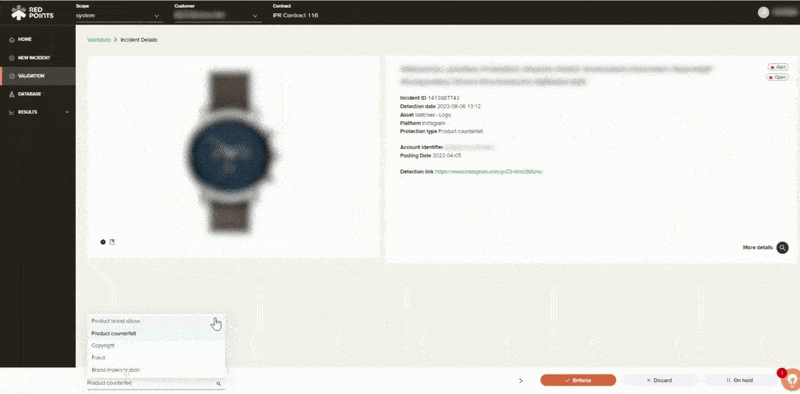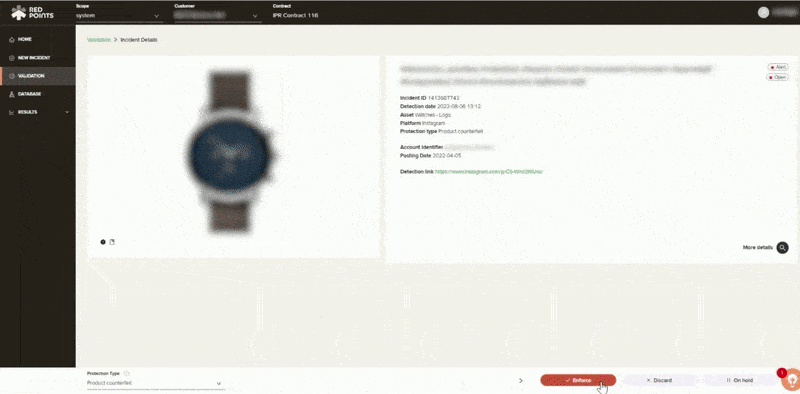
Validation & Enforcement
Once we have found those malicious apps, you will get control over the validation and enforcement process. You can kickstart the enforcement process by enabling automated rules that will allow Red Points to immediately take down certain infringing apps on your behalf. You will also then be able to manually validate and request takedowns of specific malicious apps.
Takedown and follow-through
Once an infringement is confirmed and you decide to enforce your IP rights, Red Points handles the entire takedown process. Regardless of the process or platform, whether it be a form to fill out, submitting evidence, or contacting authorities, Red Points handles it all until the process is complete.
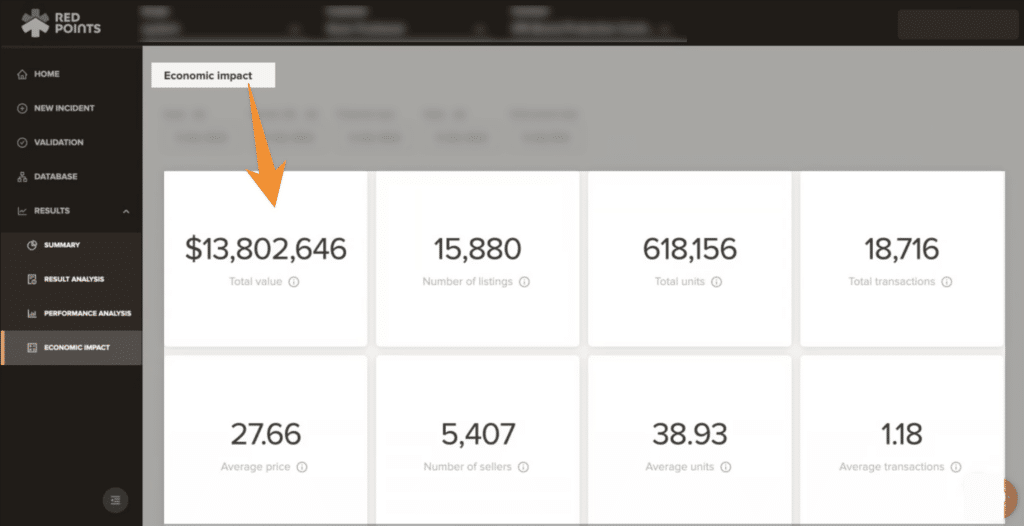
Following enforcement, Red Points then provides you with the ability to measure the impact of the mobile app protection actions. Red Points enables you to see performance dashboards and insightful, personalized reports. This will help you calculate the economic impact of your actions and look forward to a future free of malicious apps.
What’s next
Malicious apps are prevalent across a number of marketplaces. With new malware, phishing and payment scams emerging every week, mobile app owners need to remain vigilant if they want to maintain growth and hold on to their revenue.
Ultimately, only the pursuit of scammers and the removal of malicious apps will help to protect legitimate mobile apps. This is where Red Points can help. Through monitoring, detection, validation, enforcement and reporting, Red Points will ensure that you are protected from malicious apps and capable of proactively growing your legitimate app.
To learn more about how Red Points can protect your mobile apps, talk to one our experts.