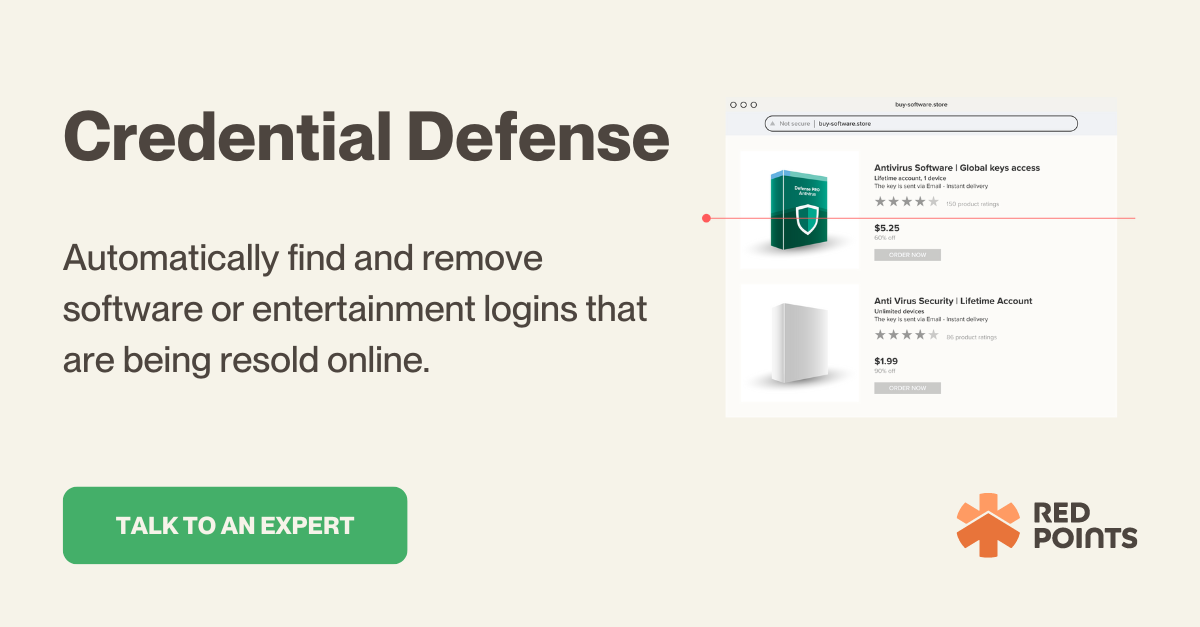
Password sharing is one of the biggest industry challenges for subscription-based businesses because of lost revenue year after year. Analysts claim that account sharing will cost video streaming platforms and pay-TV companies at least $12.5 billion in 2024.
In fact, Red Points’ research on credential sharing found that 51% of consumers currently use shared passwords in some capacity, and 66% of consumers would be willing to resell their credentials in the future if new subscription-based services were to emerge. This not only shows how pervasive password sharing is in society today but also how difficult it will be to address going forward as more businesses switch to subscription-based business models.
Fortunately, several options are available to brands to help fight password piracy and credential sharing. This guide will highlight some of these solutions.
In this article, we will discuss :
- Is password sharing illegal?
- How hackers steal and resell credentials online
- How password sharing impacts brands
- How Red Points can protect your business from password sharing
Importance of preventing password sharing
As a business, protecting your brand is essential to ensure customer loyalty and maintain a strong reputation. One issue that arises in the digital age is the act of password sharing. While some online platforms may allow password sharing, most prohibit it unless explicitly stated in their user agreement. For example, when Apple Music launched in the European Union, they explicitly stated that password sharing was not allowed and would not be tolerated.
It is important to note that password sharing is not just a violation of company policy, but it can also be illegal in some regions of the world. In the United States, the Computer Fraud and Abuse Act makes unauthorized access to a computer system and/or information, which includes password sharing, prosecutable.
Even in regions where password sharing is not clearly illegal, it is still frowned upon by companies and consumers alike. As a business, it is important to communicate your policies on password sharing clearly to your customers and take appropriate measures to prevent it. This not only protects your brand but also ensures that your customers’ personal information remains secure.

How hackers steal and resell credentials online
Password sharing isn’t always the user’s fault. Sometimes, hackers and bad-faith actors infiltrate innocent users’ security systems, retrieve their passwords, and sell these details to willing buyers online.
Some of the methods hackers employ to steal users’ credentials online are:
- Phishing
Phishing is a term that refers to obtaining sensitive information from users by deceiving them into divulging their own personal data to the attacker unwittingly. In particular, phishing attacks try to trick users into providing information required to access subscription-based services or unlock paid software. These attacks may use convincing messages, links, and even phone calls to trick users into divulging key login credentials, such as passwords or security tokens.
- Credential stuffing
Credential stuffing is a form of cyber attack where the attacker uses an existing username, Password, or other account credentials on one website to attempt to gain unauthorized access to another unrelated account on a different website.
This technique is usually used when a website or service provider is compromised, and hackers obtain a large amount of data from a breach, like usernames and passwords. The technique is often successful, as users often use the same password and login details across different websites.
- Brute force
Hackers use various methods to gain access to your accounts, but the most common and direct is using brute force.
Brute force attacks try to guess passwords by using many combinations of letters and characters until they hit on one that works.
Brute force attacks are often effective against weaker passwords that are not in a password manager and weak passwords in general.
- Malware
Malware is another way hackers get credentials. Malware comes in many forms and can be used for various malicious purposes, from spying on your every move to completely locking you out of your computer to stealing your credentials and reselling them online.
A typical example of malware software is a keylogger. This software records every keystroke typed on the keyboard or pin pad and relays it to the hacker. Once the hacker has this information, they can use it to attempt to guess the victim’s password.
Malware can also be concealed in fake mobile apps in a repackaging scam, which is why it is common to find malicious software in apps gotten from third-party stores. Unsuspected consumers download these fraudulent apps thinking they are the genuine thing, but end up having their personal data stolen.
Last, but not least, there is malware that steals information from browser caches (such as passwords) while remaining undetected in the background.
How does password sharing impact your brand?
Password sharing has several drawbacks for subscription-based businesses.
They range from the obvious, like lost revenue, to secondary considerations, such as data collection, optimization, and the possibility of data breaches.
The consequences of password sharing include :
- Revenue loss
The most significant and obvious disadvantage to password sharing is reduced revenue. Suppose a subscriber gives out their credentials to a large group of people. In that case, it’s reasonable to infer that some of those people may have otherwise paid their membership fees for content access if not for the shared password.
The effect of reduced revenue is particularly pronounced amongst video streaming platforms and paywalled websites. And while the financial juggernauts of streaming might be able to absorb some of these losses, many businesses would be much less likely to survive over any extended period of time.
The risk of losing revenue is greater for businesses that lock away their content or software behind paywalls. While businesses with this model typically rely on single-use access keys to download the content or software, the distribution of access to multiple users stemming from only one purchase limits sales.
- Compromised data collection
Understanding your audience is crucial for all businesses.
So, when customers share passwords, it not only costs businesses money. It also prevents them from gathering vital first-party data, such as customers’ demographics, likes, preferences, and other specific information that enhances user experience and customer satisfaction. For many businesses, this data is their most valuable asset because it can help them offer a more personalized consumer experience tailored to each user.
- Data breaches
When users’ passwords are sold online, personal details (such as login info, email address, and in some cases, names) are given to unknown individuals, possibly even bad actors with bad intentions.
Even worse, the account holder could potentially have their other personal accounts that use the same credentials exposed.
A compromised user account can put other online businesses at risk as well, as hackers will probably try the compromised credentials across other services as well in a bid to unlock more “free” services.
How can Red Points protect your business from password sharing?
Password sharing is, first and foremost, a digital rights management problem.
To address this challenge, businesses need to take a proactive approach to digital rights management by employing robust protection measures and software. This is where Red Points comes in. Red Points’ Anti Piracy services are designed to help businesses safeguard their digital assets and prevent unauthorized access to their content.
By working with Red Points, businesses can benefit from a range of Digital Rights Management solutions that are tailored to their specific needs. For instance, our Credential Defense software can detect and disable unauthorized sharing of passwords, thereby preventing non-paying users from accessing premium content.
How does Red Points work?
Red Points’ software works in three key stages:
- Detection
- Validating
- Enforcing
The first stage relies on our advanced machine learning technology to conduct bot-powered searches of the web for any potential cases of infringement. In this case, these could be listings offering unauthorized access to your business’s content or software. All potential infringements found online are then compiled on our platform for review.
This leads us to the second stage, validation, which is the process where you, the user, review the potential infringements we’ve detected and decide whether or not to have them taken down. In order to save users time and ultimately money, this stage in the process offers users the option to implement smart rules that can automatically validate specific types of detected infringement. This ensures that guaranteed infringements are immediately enforced whenever they are detected, greatly reducing the impact on your business.
The ultimate stage of this process is enforcement, which is the stage in which Red Points takes down the infringement. This stage is handled entirely by Red Points, which gives users their time back and allows them to focus on other aspects of their business.
Once enforcement has been completed Red Points notifies the user and provides them with a detailed report. Other detailed reports tailored to the needs of the users’ business are readily available on the platform to be viewed at any time.
What’s next?
While it is nearly impossible to identify, from sign-up, a user prone to sharing passwords, you can nonetheless proactively protect your business from the dangers associated with password sharing by employing robust digital rights management measures and protection software.
Red Points’ Anti Piracy expertise, coupled with our state-of-the-art detection and enforcement technology, makes it possible to provide a comprehensive credential protection service.