Table of Contents:
Last updated on: October 6, 2022
Wallet hacks and digital theft are significant concerns for individuals and businesses who transact with cryptocurrencies.
As a result of its meteoric rise in value over the years, the cryptocurrency market has caught the eye of both legitimate investors and malicious hackers. According to Chain Analysis, crypto hackers and scammers made away with over $14 billion worth of cryptocurrency in 2021.
Cybercriminals have many ways to get into people’s wallets and are constantly looking to exploit any security loopholes. You can prevent yourself from falling victim if you take the necessary precautions. This guide will let you know all you need to protect yourself.
In this article, we talk about:
Hacking is a common problem in the crypto industry. As of July 2022, hackers made away with $1.9 billion worth of stolen cryptocurrencies, according to Chainanalysis.
While the crypto industry continues to evolve and innovate new methods to fight these bad actors, there are some security best pratices you can implement now to protect your crypto from crypto hackers..
It is not a good idea to keep all of your cryptocurrency in a single wallet, instead you should use separate wallets for separate purposes. For example, you can use one wallet for transactions, and another for saving your crypto. Not only is this one of the most effective techniques to safeguard your cryptocurrency wallet in the case of major incidents like data breaches, but it will also protect you from losing everything in a worst case scenario event where your wallet is hacked.
Using public Wi-Fi or unsecured internet can offer hackers access to your crypto wallet. Use a secure internet connection and, for added peace of mind, connect to a virtual private network (VPN) whenever you engage in online trading or access your cryptocurrency wallet. A virtual private network, or VPN, is a service that encrypts your web surfing activity to protect it from being monitored and disrupted by cybercriminals. It also enables users to change their IP address and location.
Be sure to update your passwords on a regular basis. If hackers know you use the same password in multiple locations or websites, it will be much simpler for them to figure out your password and gain access to your cryptocurrency wallet. Changing your password often and using complicated passwords is one way to protect your crypto wallet. If your wallet or device supports two-factor authentication (2FA), use it. This will provide you with an extra layer of security against hackers. To avoid repeating passwords, use a password manager that generates strong ones.
Be wary of clicking on suspicious link or emails. Cybercriminals often use this to steal cryptocurrency from those who do not realize they are being targeted. A hacker can trick victims into giving up their private keys and other sensitive information by sending them a fake email or advertisement seeming to come from the legitimate crypto company.
Cryptocurrency cold wallets store your crypto offline in a hardware device, safely out of reach of anyone without the private key to access them. Use a cold wallet to hold your long term crypto investments. The likelihood of a hacker gaining access to your investment portfolio is virtually nonexistent.
Cryptocurrency scams are ploys and tricks scammers employ to gain access to the funds of unsuspecting users either directly, or by tricking them to send it to them.
Swindlers often target new users who are just transacting with cryptocurrency for the first time, as they are most susceptible to their tricks.
Scammers are confident in getting away with fraud becayse of the irreversible nature of cryptocurrency transactions and the anonymous nature of blockchain networks. Fortunately, however, as result of user education campaigns as well asimproved security best practices, incidences of crypto scams are actually on the decline.
According to ChainAnalysis, the total scam revenue for 2022 so far sits below $1.6 billion, which is a shocking 65% lower than it was mid-2021.
However, this does not mean these scams have completely disappeared. There are actually three surefire ways to identify a cryptocurrency scam.
The easiest way to detect a fraudlent crypto investment is to simply ask yourself, “How is this crypto project making money?”
Cryptocurrencies are volatile by nature, and any investment is ostensibly a gamble, which means definitively that is never “risk free”. Any crypto project that promises guaranteed returns, with no risk of losing funds is almost certainly a scam.
No financial investment can guarantee positive future returns because investments can go down as well as up.
Any serious cryptocurrency project must possess a well written whitepaper. The contents of a project’s whitepaper is often what determines if a project will be successful or not. A well written whitepaper should enlighten readers about:
If the whitepaper of any cryptocurrency project you are interested in is confusing, poorly written, or is missing any of the above information, you should, at minimum, proceed with caution, if not, avoid the project entirely.
Crypto deposits are uninsured. Hence, it can be quite challenging to get your money back from cryptocurrency scammers because most crypto assets are neither regulated or controlled by the government. There are some cryptocurrencies and crypto platforms that have the infrastructure in place to report and investigate these kinds of incidents, but, even in these scenarios, recovering your crypto is still rather unlikely. This means that in a majority of circumstances you are not likely to recover stolen crypto once it has been removed from your digital wallet.
When all is said and done, buying and trading crypto is “caveat emptor” – at the owner’s risk. Users ultimately bear the onus of safeguarding their funds from crypto hackers and scammers.
Crypto scammers often target crypto friendly brands and businesses in the hopes of an illegal payout. These scams can be
There are three major methods that crypto scammers often user when they attempt to target businesses:
Crypto scammers will often try to gain access to a digital wallet or other sensitive information by sending emails and text messages containing bots and malware viruses. Avoid clicking suspicous looking and spam emails on your work desktop, no matter how trustworthy the sender of the mail is usually, they could have been hacked, meaning their email is compromised.
These maliscous scams often direct victims to a fake website that might perfectly emulate a website that they log onto frequently, however when they try to log in here, their login information is revealed to the scammer.
When a dependable company client suddenly starts demanding that they be paidt in cryptocurrency, or in a different crypto wallet than usual, without properly explaining why, you should be cautious. It’s highly likely that their login has been compromised or a scammer has created a fake online persona and is posing as them in order to steal your money.
To spot these cases, it is crucial that you pay careful attention to things like a difference in their email address, a change in profile pictures, or simply if their writing style seems to have suddenly changed.
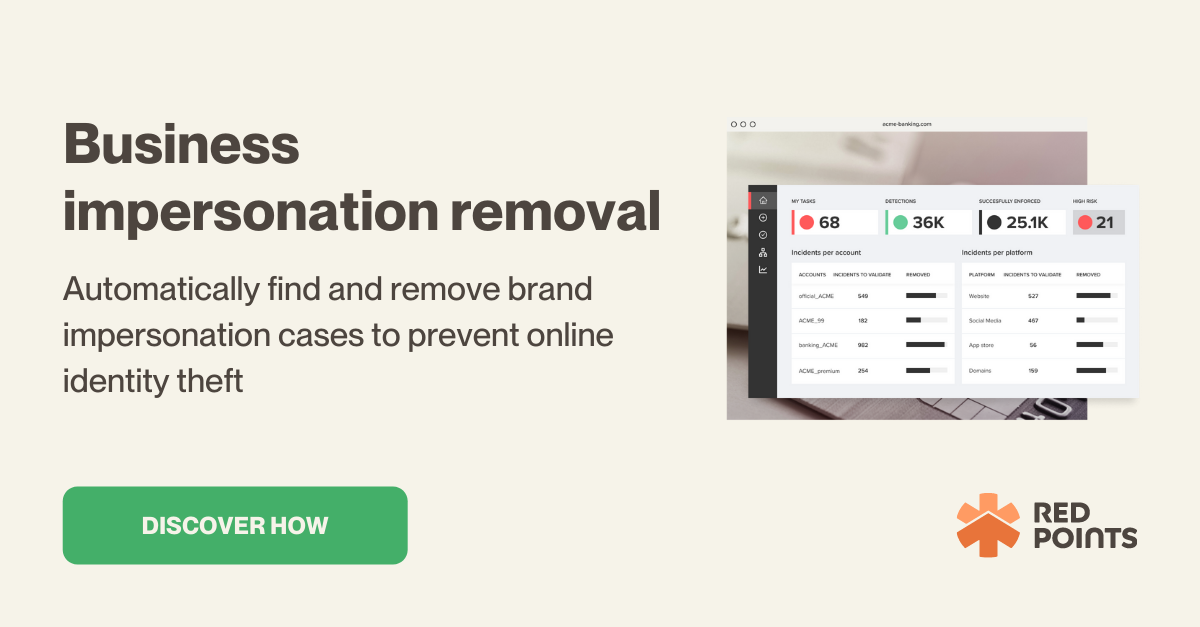
There may even be a moment where your own business is being impersonated and send our messages demanding payments in cryptocurrency, which happens quite often these days. To prevent being targetted by such a scam, businesses can utilize a proper tools, such as Red Points’ impersonation removal software, which can take down these scam accounts before they do irreparable damange to your business’s reputation.
In investment scams, a hacker, or a team of hackers, will create a fake but highly believable version of a real crypto trading platform. To get people to believe that the platform is real, they might post fake ads on social media and hire content influencers to “shill” their site. The aim is simply to get people to make cryptocurrency deposits, which in turn can never be withdrawn.
Unfortunately, yes, your digital wallet can be hacked. The reality is that bad actors are constantly evolving their tactics to keep up with the development of new security protocols. There are several ways a digital wallet’s defenses can be beat, but fortunately many of those methods require confidential information from you that won’t be exposed if you are cautious.
As we’ve described above, there are a number of best practices for safety that you should implement immediately, regardless of whether you use cryptocurrency for personal or business purposes.
Cryptocurrency hacks and scams are constant dangers for brands and businesses that transact with cryptocurrencies. As a result, businesses need to take proactive steps to mitigate any risk and prevent these incidents from occuring.
Red Point’s Impersonation Removal solution can effectively prevent, detect and stop your business from being targeted by crypto scammers and bad faith actors.