In almost every data breach or cyber attack, perpetrators try to mislead users into giving away sensitive data such as their login credentials or financial information. Particularly common are phishing scams, these scams rely on the impersonation of someone you trust, of a brand.
In this article, we’ll go over:
- What is a phishing site
- How brands can report it
- How Red Points can help automate the
What is a phishing site?
A phishing site is a fraudulent website that is designed to trick users into revealing their sensitive information such as usernames, passwords, credit card numbers, or other personal or financial information. The attackers create these sites to look like legitimate sites of well-known brands, financial institutions, or government agencies, and send out phishing emails or other messages that lure the unsuspecting users to click on a link to the fraudulent site.
Phishing sites can have a significant impact on brands, as they can tarnish the brand’s reputation and erode the trust of their customers. When users fall victim to phishing attacks, they often blame the brand whose identity was used to trick them. This can result in negative publicity and damage to the brand’s image.
Phishing attacks can also result in financial losses to the brand and its customers. If the attackers are successful in stealing the users’ sensitive information, they can use it for fraudulent activities such as making unauthorized purchases, opening credit accounts, or committing identity theft. This can lead to significant financial losses and legal liabilities for the affected brand.
How to report phishing sites
Google provides a service called Suspicious Site Reporter for users to report spam, harmful, and phishing websites. The Suspicious Site Reporter add-on for Google Chrome is fantastic for spotting malicious web pages.
To inform Google about a website, do the following:
- Check out the Safe Browsing Report page.
- Paste in the address of the web page you want to see.
- You must complete the CAPTCHA entry.
- Defend your report with a solid justification (optional).
- Submit Report by clicking.
To use the Suspicious Site Reporter and send in websites for examination by Google Safe Browsing, you’ll need to use Google Chrome or a Chromium-based browser.
Since it’s an add-on, you only have to get it from the Chrome Web Store. The application adds an icon to the top right of your browser window after launching it. If you see a website you think is malicious, you may easily report it by clicking the button.
With the addition of human reviewers, Google Safe Browsing has become much more helpful.
After you report a website, many browsers, including Google Chrome, Mozilla Firefox, Opera, and others, will stop being able to access it. Get rid of the site in Google’s index and prevent Gmail from receiving any emails that contain the URL. Links to the site from other Google services, such as Google Maps evaluations, YouTube videos, or Blogger posts, will also be disabled.
You can report websites suspected of hosting malicious code or spam or engaging in unethical link schemes to artificially boost their search engine rank.
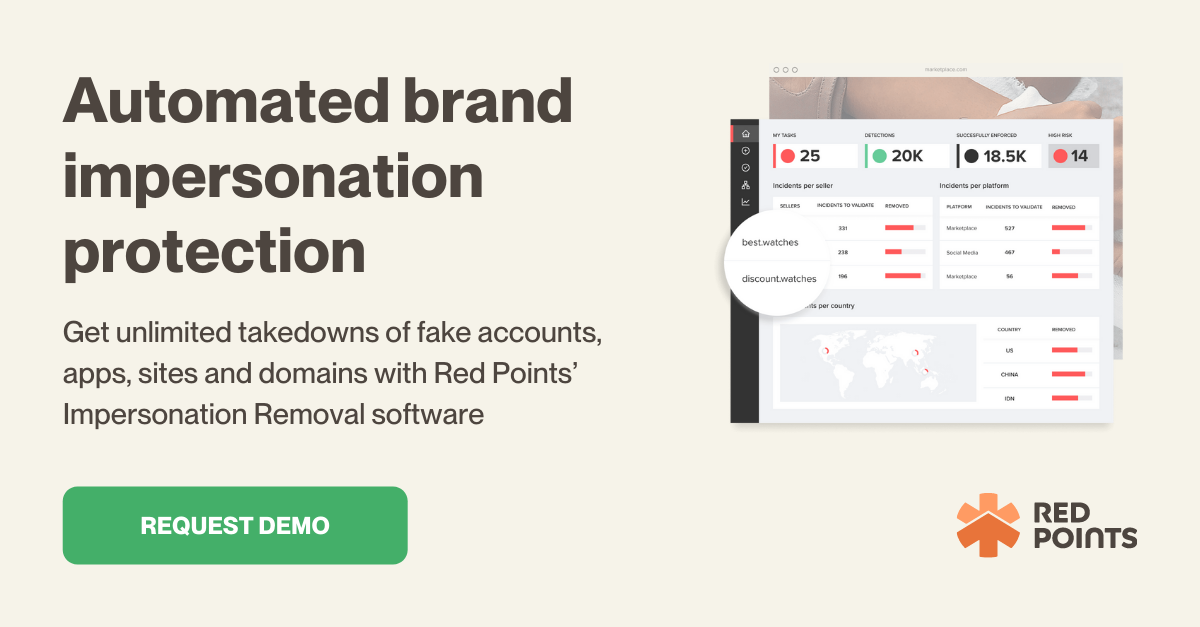
Using the most cutting-edge impersonation protection technology in conjunction with world-class specialists, artificial intelligence tech solutions simplify your life by protecting your brand against fake social accounts, standalone websites, and lookalike applications.
With the use of Red Points’ Impersonation Removal software, you may shut down an infinite number of fake accounts, applications, websites, and domains.
What’s next
More than ever it is crucial for brands to take measures to prevent phishing attacks and protect their customers’ sensitive information. This includes educating customers about the risks of phishing, implementing security measures such as multi-factor authentication and encryption, and regularly monitoring for and taking down phishing sites that impersonate the brand.
When you use Red Points, you can feel confident that your company and its brand image are meticulously guarded against fake websites and other forms of online fraud.
Use Red Points’ Impersonation Removal tool to protect your customers from phishing scams!