Companies large and small have been the targets of phishing scams since they first began alongside the inception of the internet. Today, ease of access to the web has made it far easier for scammers to prey on companies, and the effects can be detrimental. Brand owners should take the proper steps to set up phishing protection in order to keep their employees, customers, and businesses safe.
Summary:
- Most common types of phishing to prepare for
- How to protect your company from phishing online
What is phishing?
Phishing is a type of cybercrime used by scammers to trick online users into clicking on virus links, giving up sensitive information, and more. Phishing scams can target entire companies, and it only takes one employee clicking the wrong link to cause irreparable damage.
With the rise in remote work, online shopping, and digital brands due to the pandemic, phishing has never been a more active threat to brands. An attack can be set up and implemented by scammers in minutes, and companies need to be prepared.

9 most common types of phishing
There are many types of phishing out there as digital scams evolve every day, but there are common phishing scams you can prepare for. Here are some of the most common types of phishing that brand owners should know about:
Email phishing
Scammers typically use email phishing to steal sensitive information from the victims of their attacks. Usually, these emails look like they are coming from a trustworthy source or even a higher-up like the CEO of the company. Scammers can pose as employees’ bosses and request them to send them money or personal info or click on a malware link.
Email phishing is especially easy to fall victim to, and poses a very real threat to businesses. It’s essential to prepare your employees for phishing emails and teach them how to identify them to prevent this from happening.
Spear phishing
Spear phishing is similar to email phishing, but targets specific individuals within an organization. Many companies post their employees’ names and contact information online, which makes it easy for scammers to target people within the company.
This can be extremely dangerous for your brand, as scammers may be able to gain access to private business information, customer info, and more.
Whaling
Whaling is an even more targeted type of phishing that includes impersonating a higher-up or CEO of a company. By making their email appear like it’s coming from the CEO, scammers then contact other high-level senior employees in an attempt to get sensitive information. This is another reason every employee at your company, from entry to senior level, should be aware of phishing threats and how to protect themselves.
Domain spoofing
Domain spoofing is another type of phishing that utilizes impersonation to trick online users into giving up sensitive information. Scammers can fool customers and employees by stealing content like photos, blogs, or copy, and using a similar domain as an existing company.
Domain spoofing can be a great risk to brands, as potential customers may be taken advantage of alongside employees of your company. Monitoring for domain spoofing will help keep your brand protected from these attempts.
Pharming
Pharming is a sophisticated form of phishing that redirects online users searching for a specific website to a fake site instead. To do this, a company’s server usually has to be infected with malware from a previous email phishing attempt.
Once done, the scammer can redirect traffic to this fake website without users ever realizing it’s happened. Then, they may give up sensitive personal information, customer credit cards and financial info, and more. This can be devastating to a company and can be very difficult to detect until damage has been done.
Search engine phishing
Search engine phishing is simple for scammers to pull off because they let search engines like Google do the heavy lifting for them. Scammers create websites featuring highly discounted products and then get their site indexed so it appears in online searches. When shoppers search for products, these sites will appear and can be extremely difficult to identify as scams until it’s too late.
While search engine phishing is generally targeted toward consumers, it can still be a threat to your business. If your employees are searching for something on their work computer and end up clicking on a malware link, your server could be exploited.
Angler phishing
Among the new tactics in the world of online scamming, angler phishing uses social media platforms to target victims. Scammers pose as customer support specialists of certain brands, or the platforms themselves, to trick users into sending them their login information and more.
As a brand owner, you should ensure your marketing team and anyone else who often uses social media for work prepare for angler phishing.
Vishing
Vishing is a form of phishing that has been around for years, known as voice phishing, and usually occurs over the phone. Scammers call victims and pose as an official or authority to trick them into giving up personal information.
Because employee personal information like phone numbers is so readily available online, your employees should be prepared for vishing attempts. Scammers may try to get company information, employee social security numbers, and more, and employees should know not to give this information over the phone.
Smishing
Smishing also involves phones but uses text messages instead of phone calls. The scammer typically poses as someone the victim knows, like their boss or work colleague, by saying they got a new number. They then ask for sensitive information, or for the victim to do something like buy a gift card and send them the number.
You can help protect your employees from smishing attacks by setting up clear communication boundaries. It will be far easier for them to identify scammers if they know you won’t text them for important info.
6 ways to protect your company from phishing online
Some phishing attacks like vishing and smishing require companies to act offline, while others require monitoring of online channels. For the best all-around phishing protection, follow these steps:
Build a robust IP portfolio
Any phishing that happens online has something to do with stealing a company’s identity. That said, the key to protecting your company is to ensure you have broad, holistic coverage of your intellectual property. Don’t leave out anything, as typical phishing happens when cybercriminals fake your company website, web design, social media accounts, and more.
The top things you’ll need to monitor and protect are your domain name, copyright, and social media presence.
Educate your customers and audience
Knowledge is power, especially when it comes to phishing attacks. If you have clear communication with your customers, audience, and employees, it will be far more difficult for scammers to succeed. Educate all your channels about the phishing threats they could fall victim to, as well as how they can best protect themselves.
Report malicious behavior to the platform
As soon as you see something happen, make sure to report it to the platform where it takes place. Social media impersonation and other phishing attacks can be detrimental to your brand if left alone for too long and must be dealt with as quickly as possible. Whether you experience scam ads, fake direct messages, and more, use the existing reporting systems on the platform to ensure it stops.
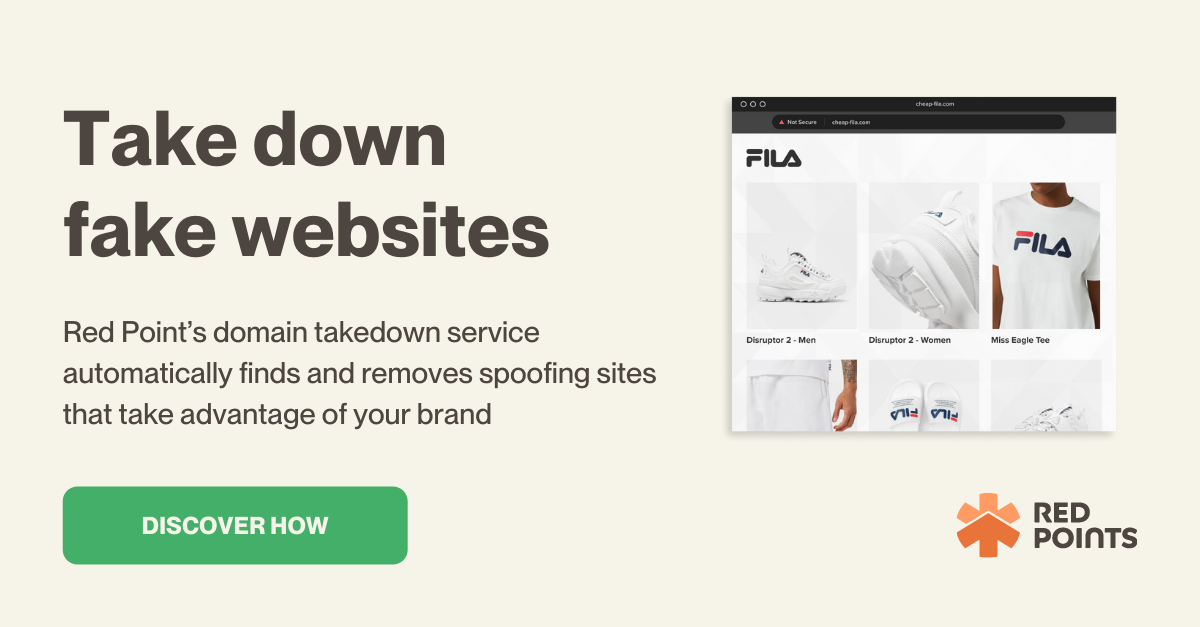
Take down fake websites
Fake websites impersonating your brand not only pose a threat to your customers but can tank your brand reputation. It’s essential to monitor for and take down fake websites to protect your revenue, customers, and brand.
Keep an eye out for anything clickable for consumers
It only takes one click on the wrong link to download malware onto a computer, sometimes causing irreparable damage. This is why hidden links and links sent via messenger and other apps are growing more and more dangerous. Be on the lookout for these links, and always do your research before clicking.
Anti-phishing/anti-impersonation tools
With so many types of phishing scams out there, it can be nearly impossible to monitor all of them and keep yourself fully protected. Investing in phishing protection software can make this process easier than ever, and offer you the ultimate protection against scammers.
Next steps
Phishing scams are no joke when your business is targeted. To ensure you are protected against phishing attacks, it’s essential to monitor them consistently and act quickly to stop them when they occur. To ensure the best phishing protection for your business, schedule a call with our team and learn how Red Points can protect your business identity.