With more people relying on apps for work, studies, and even leisure, app development and mobile app businesses have also become increasingly prevalent. Today, there are thousands of apps for many different purposes, with most of them aimed at making tasks much easier to accomplish.
The downside is that there are also more people falling victim to app impersonation. A serious problem for both users and developers alike, app impersonation is something that needs to be detected and addressed seriously. For business owners in particular, app impersonation can cause loss of profits, customer confidence, among other business risks.
In today’s article, we will focus on:
- What is app impersonation?
- How does app impersonation impact your business?
- How can I detect app impersonation?
- How can I report app impersonation?
What is app impersonation?
In simple terms, app impersonation is the process of cloning legitimate applications for illegitimate purposes. These illegitimate purposes include being able to collect sensitive personal information, such as the user’s biometric information or their bank details. Another one is being able to steal confidential business data from the app developer.
One common type of app impersonation is API manipulation. Basically, API, or Application Programming Interface, is a mechanism which acts as a software intermediary between two applications. It allows two apps to “communicate” with each other, such as when your smartphone’s weather app “talks” to the weather bureau’s software system to give you weather updates, for instance. Here, app impersonation happens when the perpetrators take advantage of the vulnerabilities in the APIs themselves, in order to steal business or personal data. For app developers or business owners, losing your exclusive right over your brand’s highly valued intangible asset, or over your business entirely, against a cyber-thief.
An even more specific example of app impersonation is the issue on TikTok Pro, a fraudulent app that became widespread in India a few years ago. Here, the cybercriminals took advantage of the permanent ban of TikTok and other Chinese-developed apps in India and developed a clone app which then lured a lot of people in India downloading thinking it was the same as the original TikTok app. It turned out to be a case of app impersonation, where the users fell victim to data leakage, among other injurious consequences.
How does app impersonation impact your business?
As discussed above, app impersonation does not only victimize the end-user, it also negatively impacts businesses. In particular, app impersonation detrimentally affects the following major business aspects:
Data Privacy
The most common damage of app impersonation is security breach. When a business falls victim to app impersonation, its valued confidential data and records are accessed by unauthorized persons. These data and records may include customer information, insider information, trade secrets, programming codes, among others. As trade secrets and such other confidential data generally have significant commercial value, app impersonation thus results in a significant decrease in business worth.
Profitability
App impersonation has the potential to cause financial harm to a business. For instance, when a user mistakenly downloads a counterfeit version of a paid app, the original app may miss out on revenue opportunities. Additionally, if app impersonators gain access to a company’s confidential information, it can lead to a loss of competitive advantage and profitability.
Brand Reputation
A loss of customer confidence is, of course, a necessary consequence of the fraud, especially among those whose sensitive personal information was compromised. If your business has been around for quite some time, then you would know how much time and effort are spent in building and maintaining a brand’s reputation and identity. Accordingly, you would also understand how difficult it would be to gain that back.

How to detect app impersonation?
As mentioned, detection is key in defending your business against the negative consequences of app impersonation. If you are a business owner, it is important that you are able to quickly detect when apps, including websites, are impersonating yours for illicit purposes.
The most effective ways to detect app impersonation are:
Manually search for similar apps
Search the app stores and internet for apps that use similar names, logos, and content to your app. Check if any of these apps are impersonating your app or infringing on your intellectual property rights. You can use search engines or online trademark databases to help you with this process.
Check app details
Once you have identified any suspicious apps, examine their details, such as the developer name, app description, and app icon, for any discrepancies with your official app. For example, check if the developer name matches your company name or if the app description accurately represents your app’s features.
Monitor bad reviews
Look for reviews of the suspected impersonated app, especially if the app has negative reviews that mention the app being fake or not working properly. If you find multiple reviews with such claims, it could be a sign that the app is impersonating your app.
Monitor your app’s performance
Keep an eye on your app’s usage statistics and revenue to see if there is any decrease in traffic or revenue. If you notice a significant drop in downloads or revenue, it could be a sign that your app has been impersonated, and you should investigate further.
How to report app impersonation?
If you have found an app impersonating yours, follow these steps to report it:
Identify where the app is hosted
The first step in reporting an app impersonating your app is to identify the platform where the impersonated app is being hosted. This could be the Apple App Store, Google Play Store, or third party app stores where apps can be downloaded. Once you have identified the platform, go to the app’s listing page to start the reporting process.
Find the report form in the respective platform
Most app stores and platforms have a reporting feature that allows you to report an app that is infringing on your intellectual property rights. This feature is typically located on the app’s listing page, and can be in the form of a flag or report button. Look for this feature, and click on it to start the reporting process.
Provide relevant information
When reporting an app impersonating your app, it’s important to provide as much information as possible to support your claim. This could include the name and package name of your app, a link to your app’s official listing, and any evidence that the reported app is impersonating your app, such as screenshots or a detailed description of the similarities. Some app stores or platforms may have specific forms to fill out, so make sure to provide all the required information.
Submit the report
Once you have provided all the necessary information, the app store or platform will then review your report and take appropriate action, which could include removing the impersonated app from the platform or contacting the app developer to request that they remove the app.
If you need more information about app reporting, check out our guide to report copyright infringement and trademark infringement in app stores.
How to protect your business against app impersonation with Red Points?
Monitoring
To start, your business will not be able to stop app impersonation if you are not able to detect it in the first place. Thus, it is important that you are able to monitor the market and discover apps, including websites, that are impersonating yours.
As manual monitoring is admittedly a time-consuming process, apart from the fact that you will have to allot money and resources for it, you can opt to do it automatically. For example, Red Points can help automatically find fraudulent apps to protect your customers, revenue, reputation, and, essentially, your business as a whole.
Removal
Detection should, of course, be followed by effective ways to remove from the market your impersonators. Again, this can be done manually, such as personally reaching out to the perpetrator or filing a legal case or claim. This is only possible if, in the first place, you are able to find out who the perpetrator is and gain access to his contact details. Usually, this is not the case. As such, automated removal is also available. Red Points’ automated brand impersonation protection offers unlimited takedowns of fraudulent apps, sites, and domains, among its other brand protection features.
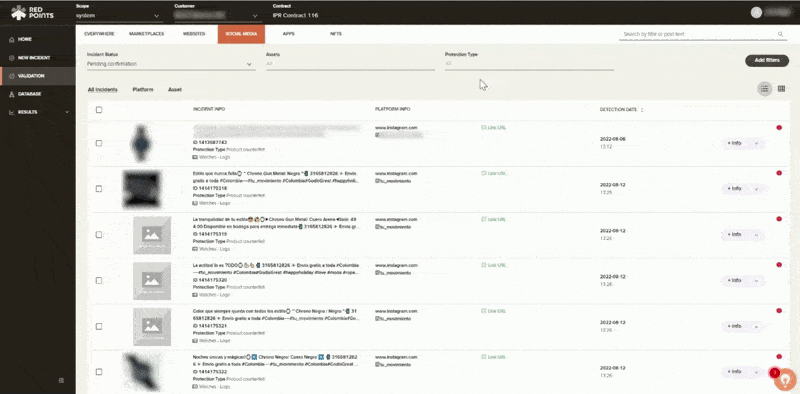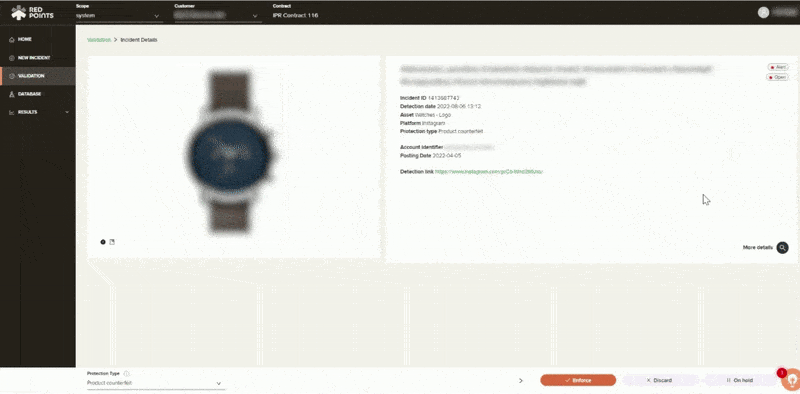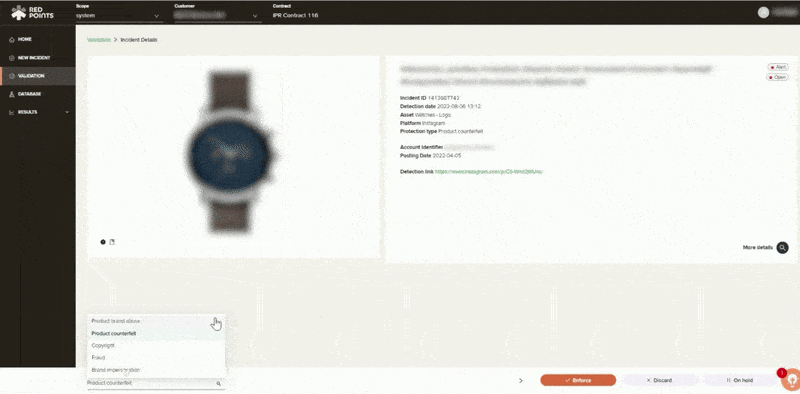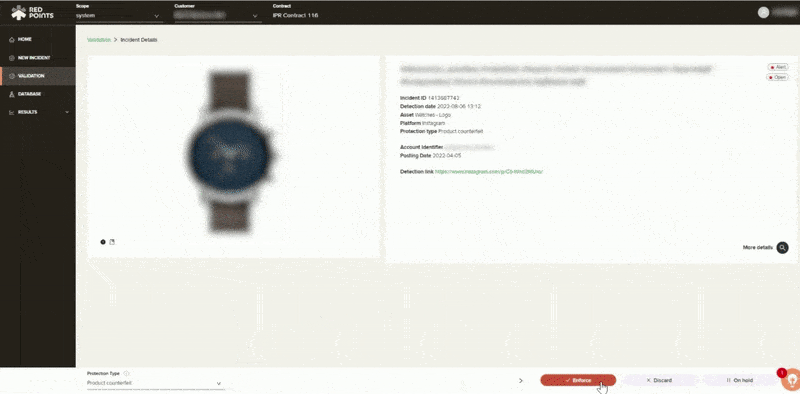
Protection
If your business has been affected by app impersonation, you have to make sure that this will not ever happen again. Apart from the automated assistance, Red Points also gives you access to performance dashboards and reports, including calculations on the economic impact of your actions. This helps you get a better understanding on safeguarding your business against app infringements and the most effective measures on how to go about protecting your brand.
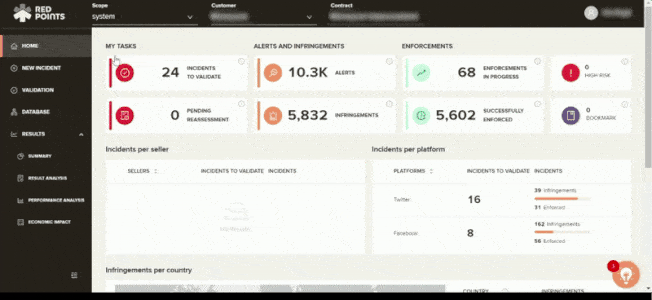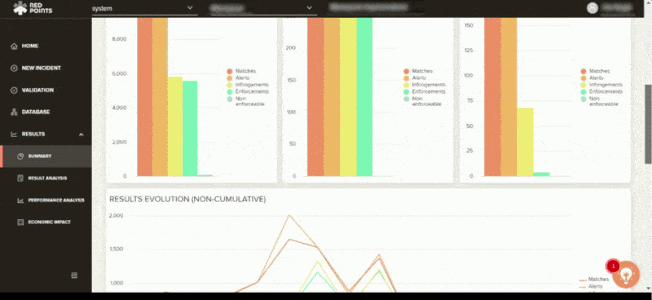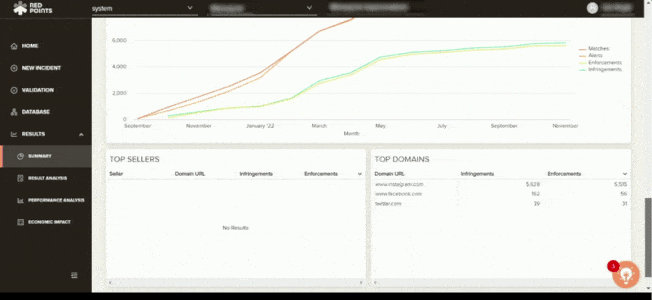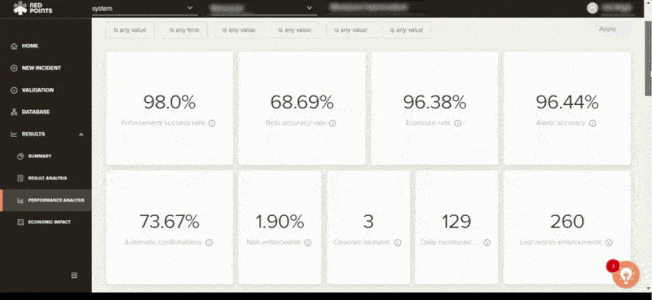
What’s next?
Fraudulent apps, and other acts of infringements for that matter, pose a serious risk to your business. They do not only result in unwarrantable security breaches and significant income losses, but, more importantly, they lead to damaged brand reputation. If not addressed properly and immediately, this may eventually lead to cessation of business operations.
Precisely, Red Points’ services are aimed at app infringement detection, removal, and overall Brand Protection.
See which of Red Points’ automated programs your business needs. Learn more about Red Points’ products or request a demo today.