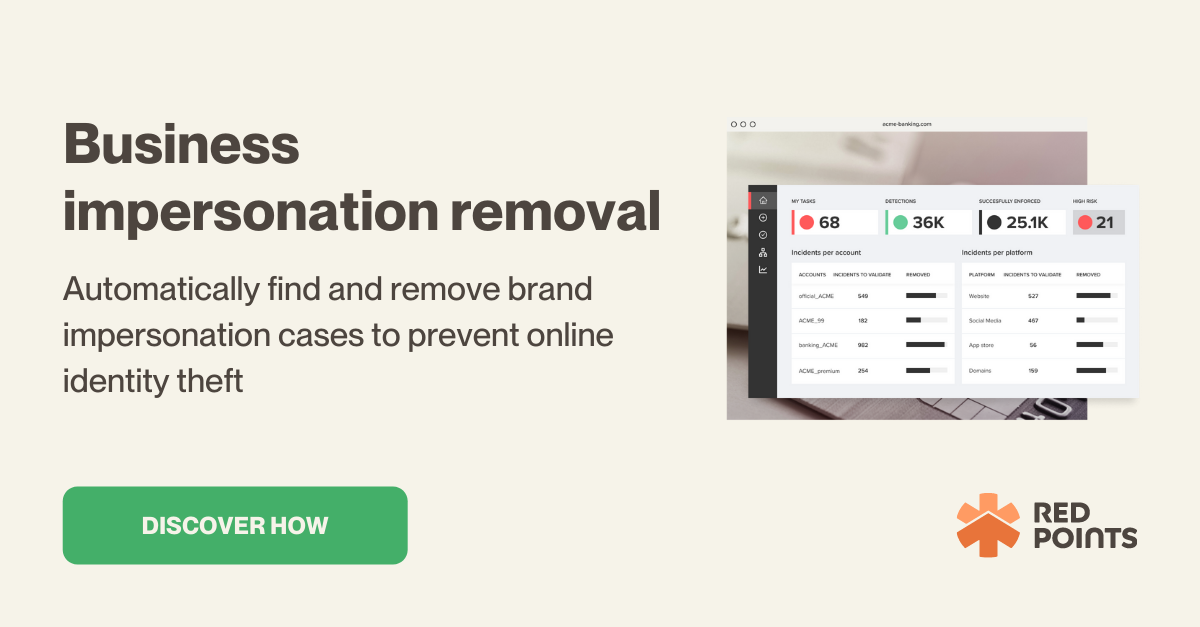
Online fraud has become a serious threat to any business in today’s digital age.
With online transactions and business activities becoming the norm and growing, the risk of online fraud has also skyrocketed.
Malicious parties are using sophisticated technologies and techniques to perform various fraud activities: stealing login credentials, frauding people for financial data, phishing attempts targeting companies, and more.
This increase in online fraud doesn’t only result in significant revenue losses for companies, but also long-term or even permanent damages to their reputations.
With that being said, it’s crucial for businesses to be proactive in protecting themselves and their customers from the growing threats of online fraud and other cybercriminal activities.
3 ways how online fraud impacts businesses: why you should care
More and more businesses are realizing the severity of online frauds as cybersecurity threats, but there are also those who made the mistake of overestimating the threat, causing them to feel completely defenseless.
The threats of online fraud are serious, but at the same time, they can be manageable if you know how to protect your business from various types of frauds and cybercrimes.
Here we will learn how online frauds can affect business in three major ways and how to overcome them:
1. Financial damage: increased costs and loss in revenue
Most online fraudsters perform their attack to make money, and extortion is one of the primary ways to do so.
There are many ways cybercriminals can extort your business in various cybercrime schemes, for example:
- Phishing is the most common and potentially damaging form of online fraud, tricking the victim into divulging their personal/sensitive information or credentials.
- Infecting your device or system with ransomware by tricking you into clicking a link or downloading an attachment, locking access to important files or documents before you pay the ransom.
- Cybercriminals may steal access to your account via Account Takeover (ATO) attacks and ask you to pay a ransom to gain back the account.
For businesses, failure to protect your business from online fraud on your platforms may cause a loss of trust from consumers, so they’ll stop buying from you. Ultimately, this will lead to a loss in revenue.
After falling victim to online fraud, companies may also lose money due to the loss of confidence from investors and sponsors, who can withdraw their funding.
Last but not least, the increasing danger of online fraud and other cyber crimes may also force businesses to put out extra investments to protect themselves or to stay compliant with newly-applied cybersecurity regulations. These extra investments can include:
- Cybersecurity infrastructure and solutions
- Manpower (cybersecurity experts)
- Insurance premiums
- Legal help both for staying compliant with regulations and when they are a victim of cyber attacks.
2. Reputational damage: lost trust and credibility
Reputation is very important in today’s digital business environment: with so many different options available in the market, consumers will only purchase products and services from brands they trust and those they deemed as credible
Being a victim of cyber attacks and failing to protect your customers from online fraud can cause long-term and even permanent damage to your reputation, even if it’s not really your fault. Your customers, clients, partners, and investors may perceive that your business failed to protect your brand and establish adequate cybersecurity practices, so they may stop business with you.
In fact, a recent study shows that 25% of the surveyed American consumers won’t do business with companies that recently experienced a data breach.
3. Legal repercussions: settlements and legal issues
Not only being a victim of cyber attacks may cause financial and reputational damages, but your business may also be held legally liable.
Back in 2011, the Japanese tech giant Sony experienced a data breach, resulting in more than 100 million customer records from the PlayStation Online service being compromised. In the end, this data breach cost Sony more than $171 million in settlements on top of the damage to public opinion and losses in revenue.
Again, failing to prevent online fraud on your platforms may hold your business legally liable.
How to protect your business from online fraud
The harsh reality is that cybercrimes, including online fraud, are here to stay. In fact, various future projections have suggested that it’s only going to get worse.
While total elimination of online fraud from affecting your business is downright impossible, you can still take measures to protect your organization against them:
1. Expect attacks and be prepared
Always assume that your business is a target of cybercriminals, and expect online fraud attacks to come sooner or later.
Audit your business’s state of cybersecurity implementation and try to identify potential attack vectors that may affect your business. This way, you can plan your defensive measures accordingly.
Identify:
- What are your most valuable IT assets and elements?
- Which assets are the most vulnerable (i.e., hardest to defend)
- Who is using each of these assets?
- What are the access points of each asset?
Based on these pieces of information, you can plan how to secure these different IT elements and their access points. Remember the old adage: if you fail to plan, you plan to fail. Always assume the worst attacks are coming, and plan for the best security measures you can afford.
2. Protect your business from impersonation
Business impersonation fraud is a type of online scam in which a cybercriminal poses as a legitimate business (that could be your business) to trick its customers and employees into divulging sensitive information, sending money, or other.
Cybercriminals may impersonate your brand in various different ways and via various channels, including but not limited to:
- Sending emails with addresses similar to your brand’s legitimate email addresses (i.e. with similar domain names)
- Setting up a fake website with your brand colors, logos, and other brand elements
- Setting up fake social media profiles
- Fraudsters impersonating your customer service or tech support and contacting customers via phone call, email, or other means
- Setting up fake ecommerce/online stores that appear to be selling products from your brand, but are actually designed to steal credit card information, sell counterfeits or spread malware to the victim’s device
It’s crucial for any modern business to be aware of these business impersonation attacks and monitor online mentions of your brands so you can remove any impersonation frauds affecting your customers as timely as possible.
Regularly monitor your company’s email domains to keep track of unauthorized use, and make sure your domain registration information is secure and up to date.
3. Educate your employees
An important consideration when trying to protect your business from fraud is to prepare your employees. Remember that even after you’ve purchased and installed the most expensive, state-of-the-art security infrastructure, your company’s state of cybersecurity depends on your employees’ knowledge.
When, for example, one of your employees has their credentials to their company email compromised as a result of a phishing attack, it can be an entry point for the cybercriminal to enter your whole network or system.
With that being said, an important aspect of your cybersecurity strategy should be about establishing proper training and educating your staff on cybersecurity.
We’d recommend making basic cybersecurity training a mandatory part of your employee onboarding program. This basic training should include at least:
- Importance of using strong and unique passwords
- Recognizing spam, phishing attempts, and other online scams
- Basic guidelines on how to securely use Wi-Fi
- Basic steps to take in the event of incoming cybersecurity attacks
Also, consider the fact that new cyber attack vectors and methodologies are being introduced rapidly, so also schedule regular refreshers of your training program to update them with the new trends and methodologies.
Design your cybersecurity training program to be as simple as possible without sacrificing the details. If it’s too complex or difficult to follow, it may lower your employees’ level of commitment to maintaining cybersecurity best practices.
4. Invest in the right hardware and software solutions
Make sure only to use solutions (both hardware and software) from reputable vendors that are security compliant. Even if only a single software solution is vulnerable, the cybercriminal can potentially exploit it to access your whole system.
On top of secure hardware and software solutions, you should also invest in adequate cybersecurity solutions to provide extra layers of protection to your overall infrastructure.
You should consider investing in at least these basic security solutions:
- Antivirus or anti-malware software. Preferably one with an AI-based behavioral detection technology.
- Brand Monitoring and Infringement Detection Solution to protect your business from being impersonated by cybercriminals.
- Bot monitoring and mitigation solution. Many types of cyber attacks are performed or assisted by malicious bots.
- A proper firewall to help you monitor and filter your network traffic. If your company is heavily targeted by cyber attacks, consider investing in more advanced network scanning firewalls to protect your network from SQL injection, cross-site scripting (XSS), and other sophisticated threats.
- SSL certificates (HTTPS) and other Public Key Infrastructure (PKI) services
5. Update everything as soon as possible
Many online fraudsters leverage known vulnerabilities to launch their attacks, and the last thing you’d want is for your network to be compromised just because of a vulnerability in your OS or one of the applications you use that actually has been fixed in a security patch.
Keep all operating systems (OSs), software solutions, applications, and firmware (in devices) up to date, ideally as soon as updates are made available. While this can be time-consuming and costly, the risks of not updating your solutions are simply too great to neglect.
If it isn’t possible to update your solutions immediately after each released update, at least maintain a regular weekly schedule to update everything.
Again, don’t underestimate the importance of keeping everything up-to-date. Even a single vulnerability in old hardware can be exploited to wreak havoc on your whole network, so invest enough time to make sure everything is updated accordingly.
6. Encrypt and backup your data regularly
One of the most valuable assets online fraudsters can target from your business is your data, so it’s very important to have a comprehensive data protection strategy.
First, make sure to encrypt all sensitive and/or regulated data. Whenever data needs to be transported, make sure both devices and/or solutions have end-to-end encryption.
Again, make sure to use a high-quality encryption solution from a reputable vendor, and update it regularly. Make sure this encryption solution is activated on all company devices, networks, and systems.
Once you’ve made sure about encryption, the next thing you should focus on is establishing a backup strategy.
We’d recommend sticking to the 3-2-1 backup strategy: at least three backups of your data in two different mediums, with one backup being stored offsite.
For offsite backup, it’s best to invest in a cloud backup solution. There are many Backup as a Service (BaaS) and Disaster Recovery as a Service (DRaaS) solutions available in the market for this purpose. Investing in the right one can effectively add an additional layer of security for your data.
7. Create comprehensive security policies and response plans
In many types of cyber attacks and fraud, once you’ve realized there’s an incoming attack, the damage has already been done, and swift action is needed.
In a DDoS attack, for example, you won’t have time to assess the situation and take action, so everything must be pre-planned.
This is where having a clear security policy and response plans are very important.
Simulate every worst-case scenario and carefully outline how these scenarios should be handled. Don’t forget to establish a chain of communications that should be followed in the event of an attack: who should be informed, who should contact who, and so on.
Establish clear security policies and develop comprehensive guidelines. Make sure to properly communicate the consequences when an employee fails to adhere to the policies (or intentionally violates the policies.)
These guidelines should also regulate access to sensitive data and devices:
- How to prevent access to company servers, computers, and devices from unauthorized users
- Steps to perform when handling lost/stolen devices
- Steps to be taken when upgrading a device (how to dispose of the old one)
- Who can access each data
- How to sign off user authorization when they no longer need specific data to perform their work.
8. Consumer education
As discussed, compromised customer data during a data breach may lead to legal repercussions for your business, so the general principle is only to collect the information you absolutely need.
However, in cases when you need to collect customers’ personal and/or sensitive information, create a comprehensive and clear disclaimer stating why you must collect their information and how you are going to use this information.
It’s important to communicate to your customers that you will not request any personal and sensitive information like their credit card details or Social Security numbers through unprotected means like emails or phone calls. Encourage them to report suspicious communications. This aspect is important to educate customers against phishing attacks while also protecting your business from being liable for these attacks.
If your brand is being targeted by counterfeiters, adding a section or disclaimer on your website including all your legitimate distributors, how to spot a fake item, and sending email communications ahead of critical periods (like holiday season), can prevent your customers from being scammed by online fraudsters.
What’s next
Protecting your business against online fraud is not a one-off thing and can be a never-ending battle depending on the persistence of the bad actor.
Above, we have discussed the actionable steps you can take in protecting your business from various cybercrime attempts and online fraud, but in the end, it’s about establishing four things:
- Investing in proper security infrastructure and only using hardware and software solutions from reputable companies.
- Encrypting all sensitive data and regularly backing-up the encrypted data in secure places.
- Adequately train your employees while maintaining a security-first company culture.
- Educating your customers by providing them information and tools to identify possible phishing attacks and scammers trying to sell them fake products.
Remember that protecting against fraud and other cyber attacks doesn’t only mean avoiding the negative impacts of these cyber attacks but will also improve the company’s overall resilience and efficiency.