Social engineering attacks have increasingly become a tactic used by scammers to take advantage of brands, steal sensitive information, and mislead consumers. Today, nearly 98% of all cyber-attacks involve some form of social engineering to deliver malicious content.
It is therefore vital for businesses to be aware of the threat of social engineering. You have to implement solutions that will ensure you can safeguard your assets and customers from deceptive tactics that have proven to be very damaging for businesses that have failed to take the issue seriously.
In this blog, we’ll be exploring how to minimize the risk of being targeted by social engineering attacks and how to protect your brand by highlighting a number of topics, including:
- Understanding social engineering attacks: recognizing the threat
- Importance of social engineering prevention for businesses
- Protecting your organization from impersonation and fraudulent schemes
- Top strategies to defend against social engineering attacks
Understanding social engineering attacks: recognizing the threat
Social engineering is a kind of psychological deception used by scammers to manipulate individuals into giving over confidential or sensitive information. This information will usually be used to perpetrate some fraudulent scheme or tactic.
Commonly, when social engineering is used online against businesses, these fraudsters will target their customers and employees in order to create weak points that will allow them to steal information and money.
Some of the most common social engineering attacks include:
- Phishing
- Pharming
- Spoofing
- Identity theft
- Baiting
Phishing is one of the most popular tactics for online scammers. Typically, phishing uses dodgy links and spoofed email addresses to trick people into divulging passwords, financial data, or other personal information.
As a result, in order to understand social engineering attacks it is also important to be able to spot impersonation scams and common social engineering tactics like phishing. Contained within these scams will be various social engineering tactics that aim to manipulate the unwitting consumer and steal information. The quicker you can recognize these elements the easier it will be to identify them and start to protect your business from social engineering fraud.
Importance of social engineering prevention for businesses
Social engineering presents various dilemmas for business. Successful social engineering scams can lead to identity theft, data theft, malware attacks, service disruption, and reputational damage. These can all have a knock-on effect on your business’s finances and your overall operation.
- Financial damage
Social engineering attacks will sometimes have direct financial implications for your business. Scammers will use social engineering tactics to siphon money away from your customers which will impact the amount of revenue you are able to bring in. The risk of financial damage is high if the social engineering attacks are consistently successful. You may also have to incur costs to try to recover funds lost to these scammers.
- Reputational damage
Your brand’s reputation will suffer if you are seen to be an easy target and bad actors are continually taking advantage of you with social engineering scams. In fact, about 40% of consumers believe brands should be responsible for taking down these scams, so if they fall victim to a scammer, they hold the brand responsible. Consumers will be less inclined to trust your brand and may become hesitant to interact with your business online if they know you can’t protect your business from social engineering attacks.
- Operational disruption
One of the risks associated with social engineering attacks is disruption to your operations. In order to deal with attacks you may have to change your workflows, alter your processes and reassign your resources. This will primarily affect your IT and Security teams but will also have a major impact on your customer service team. If your customer service is spending time explaining to would-be customers that they were scammed, they are spending less time supporting actual paying customers. However, it can potentially infect your whole operation and supply chain creating logistical delays and business-wide disruption.
Businesses must prioritize social engineering prevention because it goes to the heart of brand security and customer connections. With strong social engineering prevention, you will be able to protect your intellectual property (IP), preserve your customer relationships, and safeguard your revenue. With weak social engineering prevention, you risk your brand’s reputation and ability to grow your customer base.
Protecting your organization from impersonation and fraudulent schemes
To protect your organization you need to be adept at identifying the red flags and warning signs of social engineering attacks. Within the online world of business, there are an extensive variety of digital tactics used by scammers to manipulate, impersonate and mislead. Some key red flags to take note of include:
- Romance Scams
Some scammers will take advantage of your business through romance scams. They will learn about individuals via publicly available information usually through social media. Then they will create fake identities and contact individuals within your business or your customers via social media or dating apps.
The purpose of this contact will be to build trust. They will work to develop a “loving” relationship online before asking for money or more sensitive personal information. To prevent these kinds of scams pay attention to suspicious messages and online profiles that seem inauthentic and overeager.
- Social media impersonation
Increasingly, social media platforms have become a place for fraudsters to execute their scams and take advantage of businesses and customers online. One key red flag to look out for is when a social media account uses a name, image, or other identifying element of a person or business for a fraudulent purpose.
Social media impersonation may be used to kickstart phishing scams, sell counterfeit products, or conduct fraudulent activity, Today’s scammers are more sophisticated than ever in how they use social media to impersonate legitimate brands. You must look out for suspicious activity and interactions across a variety of platforms if you want to keep your business safe.
- Fake Lottery/Sweepstakes Winnings
Is it time to claim your prize? Have you won the lottery? Did you enter a sweepstakes competition? Today, many businesses and customers are sent fake lottery or sweepstakes messages via email or social media.
These messages may appear to come from well-known companies and will claim that you are the recipient of some winnings. They will say that you can collect these winnings by giving over sensitive information or a small amount of money.
This common genre of scam targets business employees as well as customers. As soon as you see any message that states you are a winner or that you can claim a prize, this should set off alarm bells and you should steer well clear.
- Fake Tech Support Pop-ups
Some fraudsters use fake tech support pop-ups to conduct their online scams. These pop-up windows may trick users into believing they have a tech problem on their computer or web browser that needs to be fixed. They will get them to interact with their pop-up.
Through these interactions, they will try to gain access to sensitive financial or personal information. They may also encourage users to wire money or send money using cryptocurrency or a money transfer app.
Top strategies to defend against social engineering attacks
Registering all intellectual property
One of the most effective steps you can take to defend against social engineering attacks is to register your intellectual property. Your business will likely have various content attached to your brand that is capable of being protected under intellectual property rights.
For example, you can help to stop scammers using your logo in their social engineering attacks by registering your logo as intellectual property at the United States Patent and Trademark Office. Similarly, you can protect any creative work associated with your brand from being misused by scammers by registering it with the U.S. Copyright Office. By registering all intellectual property you will have a robust legal resource to use if your brand’s content is being violated in social engineering attacks.
Manual monitoring of social media and other platforms
Once you are aware of the red flags of social engineering attacks you can then manually monitor the digital world for any signs. This means keeping an eye out for suspicious interactions on social media and other platforms.
You can also enhance your manual monitoring by communicating with your customers and finding out whether they have experienced any strange interactions. Manual monitoring is a time-consuming activity but it can be crucial to helping your brand defend against social engineering scams.
Digital impersonation detection and removal software
The most effective step you take to mitigate the impact of social engineering attacks is to use a digital impersonation detection and removal software.
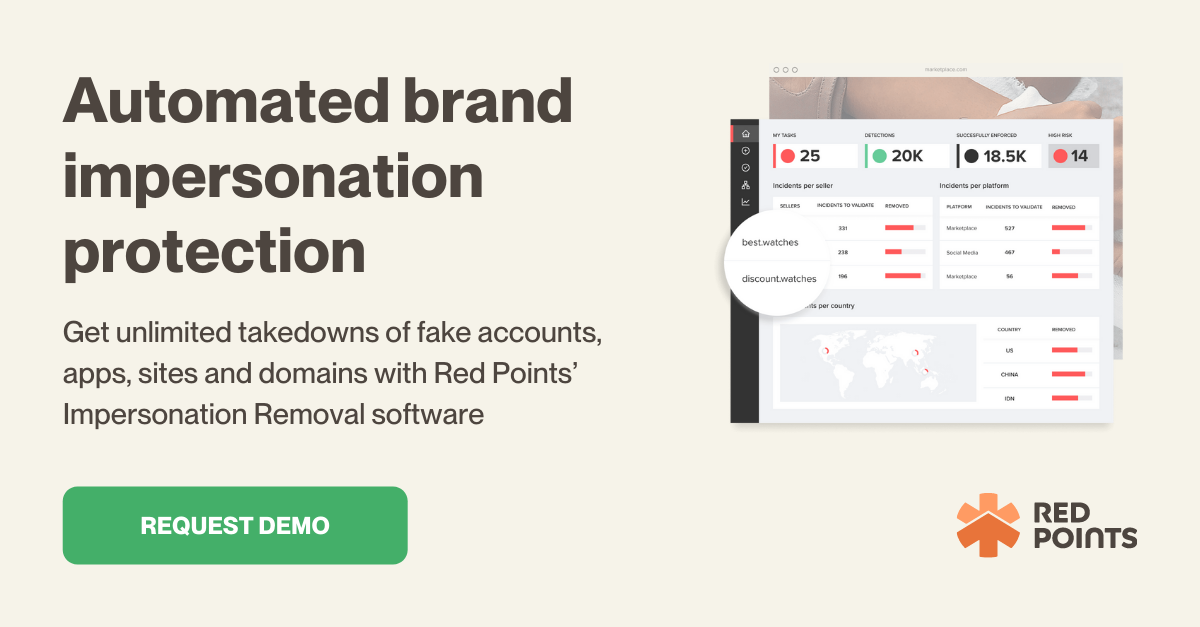
Red Points’ Brand Impersonation Protection Solution is a key tool that your business can use to get unlimited takedowns of fake accounts, apps, sites and domains. Our software will help you clean social media, pursue bad actors and create a robust defensive shield to safeguard your revenue and customers from social engineering attacks.
Our service operates via a simple, three-step system of detection, confirmation, and removal.
1. Detection
We leverage our machine learning AI-powered platform which uses a bot-powered search to monitor the web for websites that are impersonating your business’s site. These fake sites that pretend to be your brand are typically the final step in complex phishing schemes that are targeting your customers that will either steal their personal or financial information.
2. Confirmation
Whenever our machine learning platform detects and flags a website that may be impersonating your business, it is immediately added to a backlog of other sites that we have detected. As the intellectual property (IP) owner it will be your responsibility to review this log of alleged impersonation sites and confirm that they are infringing on your IP rights.
Fortunately, to make this process less manual and to maximize efficiency our platform has several smart rules and customizations that users can implement in order to automate as much of this process as they like.
3. Remove
The second a detected impersonation is confirmed it automatically triggers our takedown process, which we handle entirely on your behalf as the IP owner.
Once takedowns are complete our platform automatically tracks all data associated with your brand protection and impersonation removal efforts in order to give you a transparent look at how effective Red Points’ software is for your business.
What’s next
Social engineering attacks have the potential to seriously impact your brand’s ability to operate online. Many social engineering tactics will use impersonation fraud, phishing, and other types of deception to steal sensitive information and misuse your IP. To ensure you can successfully deal with social engineering scams you need to be protective and use a solution that is appropriate for your business.
Red Points’ Automated Brand Impersonation Protection Solution is the ideal tool to help you mitigate the impact of social engineering attacks and protect your brand from scammers. Through a robust system of monitoring, validation, and removal we empower brands to protect themselves from impersonation and fraudulent schemes.
With our help you can tackle social engineering scams head-on and safeguard your customers. To learn more about how Red Points can help you deal with social engineering attacks, request a demo here.,