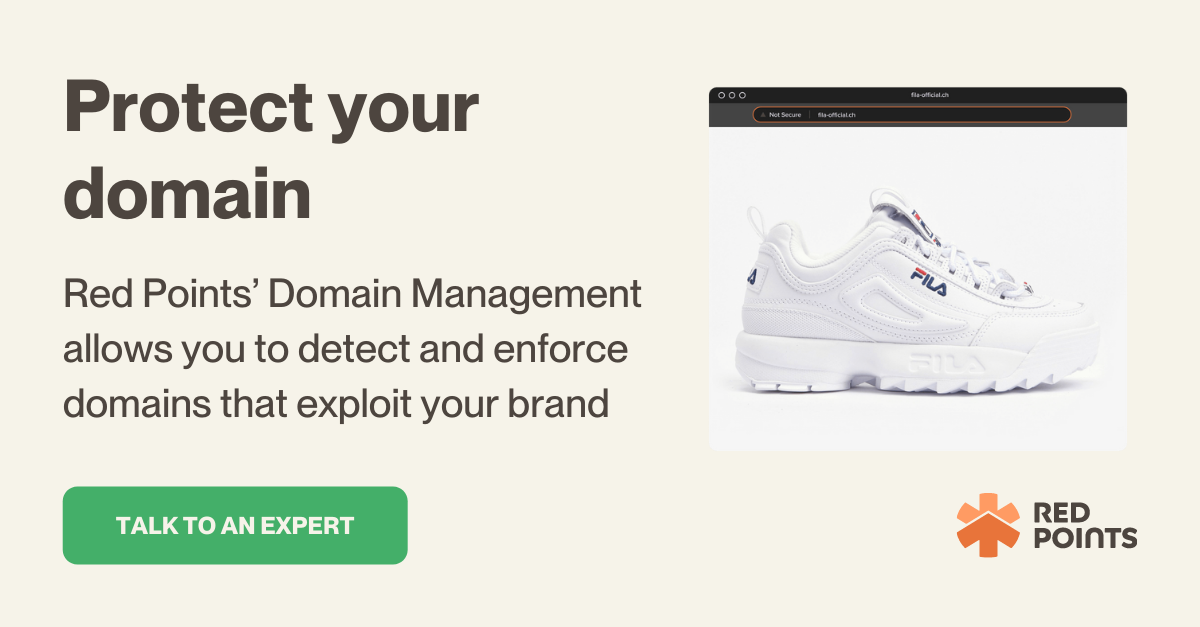
It’s no secret that the global COVID-19 pandemic has fueled a major increase in cybercrime, and cybersquatting is also among the type of cybercrimes that has shown a steady increase throughout 2020 and 2021.
Cybersquatting is a serious issue that can be severely detrimental to any business with a website or online presence in general.
We all know how reputation and credibility can be very difficult to build, and yet, can take only seconds to destroy. What if you’ve spent a lot of time and money building your online presence and your overall branding, but then a cybercriminal purchases a domain name that looks similar to yours to trick your prospective customers?
This is cybersquatting, and as you can imagine, it can do major damage to your business’s reputation and credibility.
In this ultimate guide to cybersquatting and how you can protect your brand’s valuable domain, we’ll learn about:
- What cybersquatting is.
- Different types of cybersquatting are performed by impostors and cybercriminals.
- How to prevent cybersquatting.
- How to protect your brand’s reputation from cybersquatting and other forms of brand abuse.
And more.
Let us begin this guide from the basics.
What is cybersquatting?
Cybersquatting, also often called “domain squatting,” is a type of brand abuse (and can be cybercrime) in which a perpetrator registered a domain name that resembles an established organization’s or well-known person’s likeness (i.e., an influencer or celebrity) without the legitimate owner’s authorization.
In a cybersquatting practice, the perpetrator registers and uses internet domain names that are identical or similar to company names (i.e., Go0gle.com instead of Google.com), personal names, trademarks, product names, service marks, and so on, with malicious intent to profit from the actual brand/trademark owner in one way or another.
For example, let’s assume there’s an ecommerce store called AAA, with AAA.com as its legitimate website address. A malicious party then registered the “AAAstore.com” domain name and copy-pasted the original website’s content, so prospective buyers who originally looked to make the purchase from AAA.com may be tricked. This is an example of cybersquatting, and as you can imagine, it can lead to damage to your brand’s reputation, a loss in customer loyalty, and ultimately a decrease in revenue.
In this case, the perpetrator can monetize the cybersquatting practice by either sending fake goods to customers who purchased on the fake website, stealing credit card information submitted on the website, or engaging in other nefarious scam tactics. Not only can this practice harm the buyer, but it can also ruin the legitimate website’s reputation and may even lead to legal repercussions that will drag your brand into an unwanted dialogue about poor quality or consistency.
Is cybersquatting illegal?
In the U.S. and many other countries around the world, cybersquatting is illegal. Both the ICANN (Internet Corporation for Assigned Names and Numbers) and the federal government have established legislation and policies in order to protect businesses and trademark owners from different types of cybersquatting.
The main legislation focused on combating cybersquatting or domain squatting is the ACPA (Anticybersquatting Consumer Protection Act), a federal law prohibiting people from registering domain names that are identical or similar to personal names or trademarked brand names.
There are also other federal laws like the Trademark Dilution Revision Act, as well as various state laws that can provide additional protection for trademark and service mark owners against cybersquatting practices.
It’s crucial to understand that only registered trademarks can seek legal help when they are targeted/affected by cybersquatting attacks. This can be an issue in certain cases, for example, when it’s an individual name that is targeted by a cybersquatter (not all personal names can be trademarked; more on this later.)
Anatomy of a cybersquatting practice
To be classified as a cybersquatting act, the practice must fulfill two main criteria:
1. The domain name is similar (or identical) to a registered trademark that may confuse or deceive people.
Of course, this can be very subjective since there’s no fixed definition of what’s considered “similar”. Generally, during a cybersquatting case, the court will evaluate whether the domain in question can deceive or confuse the trademark owner’s clients, customers, partners, or other people.
However, if the business or person is already well-known, but someone else buys the domain name before the legitimate brand owner with the intention to sell this domain name to the brand owner at a higher price, it can also be categorized as a cybersquatting example.
2. Malicious intent.
There are cases in which people registered a domain name that resembles established businesses or famous people without any malicious intent. Also, a name that is trademarked in one country might be totally unrelated to the same name in another country.
For example, let’s say AAA.com in Indonesia is owned by a restaurant, while AAA.org in Brazil is owned by a marine fishing company. This case can not be considered a type of cybersquatting since the two businesses are entirely unrelated without any malicious intent to capitalize on each other’s reputations.
Below are some cybersquatting examples of malicious intent that may legitimize that the domain name is obtained in bad faith:
- The domain is purchased with the intention to sell the domain to the legitimate brand/trademark owner at a higher price.
- The perpetrator starts a similar business and leverages the legitimate brand’s reputation to deceive customers or clients.
- Intention to purposely ruin the company or person’s reputation and credibility.
- Using the domain name to spread malware.
- Using the domain name to scam visitors into phishing attempts.
- Selling the domain name to the legitimate owner’s competitors.

Different types of cybersquatting
While perpetrators can use many different techniques and methods to perform cybersquatting, we can categorize all of them into just four major types:
- Typosquatting
- Name jacking
- Identity theft
- Reverse-cybersquatting
Below, we will discuss them one by one.
1. Typosquatting
As the name suggests, typosquatting relies on “typos,” typing mistakes made by internet users when typing a web address or URL into the web browser.
Typosquatting is one of the most common types of cybersquatting where the perpetrator intentionally registers misspelled domain names of established brands, for example:
- Gogle.com
- Gooogle.com
- Googlee.com
And so on.
There are also other variations of typosquatting, for example, using other top-level domains (Google.net instead of Google.com), involving different phrasing of the domain name (i.e., Goggle.com), and so on.
Homograph attack, which leverages the visual similarity of symbols to confuse users (i.e., “w” and “vv”) is also a type of cybersquatting.
Typosquatting attacks are also often accompanied by the perpetrator creating a fake website that resembles the legitimate website (i.e., similar layout, colors, content, logo placement, etc.) to further confuse the potential visitors.
The perpetrator can then launch further attacks, like spreading malware or forcing the legitimate trademark owner to buy the fake domain name to monetize their cybersquatting attempt.
2. Name-jacking
Name jacking is a type of cybersquatting attempt in which the perpetrator registers a domain name that can be associated with the name of an individual (typically famous people like celebrities, political figures, or influencers.) The main objective of a name-jacking attack is to intercept the web traffic associated with this targeted individual.
As mentioned above, not all individual names can be trademarked. According to U.S. laws, individual names can be trademarked only when they have already acquired distinctiveness through long use or advertising (meaning, you must be famous first) and have established a secondary meaning by being well-known. For instance, the rights associated with using the name, “Michael Jordan”, are owned and trademarked by the man himself, giving him full control of its use, and the right to take legal action against anyone that misuses it.
So, there can be cases in which name jacking may fall outside the scope of ACPA and other legal regulations when individual names cannot be registered as trademarks.
3. Identity theft
In an identity theft attack, the cybersquatter purchases a legitimate domain that was not renewed (typically intentionally) by the trademark owner, allowing the cybersquatter to assume the identity of the brand.
There are many techniques and technologies the perpetrators can use to launch an identity theft attack, but typically it involves using a special software solution that can perform real-time monitoring of the target domain’s expiry date.
The perpetrator can then link the purchased domain name with a fake website containing the duplicated content of the legitimate website (that now is abandoned by the owner or has a new address). This practice may effectively mislead visitors who think they are visiting the legitimate website of the previous domain owner.
4. Reverse-cybersquatting
Last but not least, reverse-cybersquatting is a specific type of cybersquatting in which a rightful trademark owner attempts to obtain a registered domain name currently owned by another company or person.
While this “should” be legal, in practice, reverse-cybersquatting may involve pressure, intimidation, and even abuse, forcing the current legitimate owner to transfer ownership of the domain name.
Depending on whether it’s performed ethically or not, reverse-cybersquatting may be considered illegal. It’s best for the legitimate trademark owner to follow the standard name dispute resolution procedures instead.
How cybersquatters monetize from you
As discussed, the act of registering/purchasing a domain similar to a legitimate trademark can only be categorized as cybersquatting when it is made in bad faith, so that the perpetrator can monetize the malicious act.
The cybersquatter can use various methods to monetize the act, but here are the most common ones you should recognize:
- Ransoming the trademark owner: The perpetrator uses the fake domain name to spread ransomware to those visiting the fake website. The perpetrator will then ask the trademark owner (or sometimes, the visitors) to pay some form of ransom.
- Domain parking: With this technique, the perpetrator redirects the domain name to another website to generate more traffic. Can be combined with other techniques.
- Scams: For example, the cybersquatter may run a phishing scheme on the website with a fake domain name, tricking the legitimate brand’s prospective customers.
- Hit stealing: Referring or redirecting the visitors of the fake (cybersquatted) website to the website of the legitimate brand’s competitors.
- Affiliate marketing: Redirecting visitors to eCommerce stores. If any visitor makes a purchase on this eCommerce store (it can be legitimate, and fake as well), the cybersquatter may receive commissions on the sales of these products/services.
How to prevent cybersquatting and protect your domain
As a business owner or an individual with registered trademarks, how can you protect your website and digital assets from cybersquatting?
Here are some actionable tips you can use:
1. Register your trademark (or trademarks) as soon as possible
As discussed, under the applicable laws in the U.S. (and also in many other countries), you can only seek legal help in the event of cybersquatting only if you are a registered trademark owner.
If you haven’t registered your brand name (or eligible personal name) as a trademark, you should do it as soon as possible. Remember that there’s a chance someone else registers your brand/individual name before you, making them the legitimate owner in front of the law, and you’d want to avoid this situation at all costs.
2. Know your legal protection
If you are located in the U.S. and if you suspect yourself of being a victim of cybersquatting, there are two laws that can help protect yourself or your brand:
- ACPA: Stands for Anti-Cybersquatting Consumer Protection Act; it’s a special law designed to combat cybersquatting in the U.S. Unfortunately, ACPA won’t be able to help domain registrants and trademark owners who currently reside in a different country. ACPA can force cancellation, transfer, or forfeiture of the disputed domain to the legitimate trademark owner.
- UDNDRP: Stands for Uniform Domain Name Dispute Resolution Policy; UDNDRP was developed by ICANN and is overseen by WIPO (World Intellectual Property Organization). WIPO can help mediate international cybersquatting disputes, where an expert panel will help review the case to find a solution for the conflict.
Here are some pointers on how you can sue the perpetrator under these laws:
Suing under the ACPA
The main purpose of the ACPA is so that legal trademark owners can sue an alleged cybersquatter in federal court to obtain a court order for transfer, cancellation, or forfeiture of the disputed domain name.
In some cases, the cybersquatter can be ordered to pay money damages.
If you are located in the U.S. and are planning to sue an alleged cybersquatter, keep in mind that you’ll need to prove:
- The malicious intent of the domain registrant is to profit from the trademark owner.
- The disputed domain name is identical or confusingly similar to the trademark, beyond a reasonable doubt.
- The trademark was registered and distinctive at the time the disputed domain was registered.
- The trademark owner was the first to use the distinctive trademark in commerce.
Suing using the ICANN procedure
Under ICANN’s UDNDRP international policy, you can file a complaint about alleged cybersquatting while providing proof of the following:
- The domain name is confusingly similar or identical to your registered trademark or service mark, again any similarities must be considered intentional beyond a reasonable doubt.
- The disputed domain name owner possesses no legitimate rights or interests in the domain name.
- The domain name has been registered and used in bad faith with malicious intent.
If the complaint is approved, the disputed domain name will be transferred to the legitimate owner (you, the plaintiff). However, unlike ACPA, you cannot seek financial remedies with UDNDRP.
3. Buy more top-level domains (TLDs)
To prevent cybersquatting, you might want to consider investing in more TLDs so they can’t be taken by cybersquatters.
There are thousands of TLDs available, and obviously, you can’t and shouldn’t buy all of them. You should, however, consider getting at least the well-known ones such as .com, .org, .net, .biz, and country-specific domains like .us, .co.uk, .ca, and so on. You should get country-specific TLDs in countries you’re planning to have a business in, even if you don’t have plans to expand the business to those markets in the near future.
These domain names in different TLDs should only cost you around $10-$20 per year, but securing them can potentially save you money and protect you from legal disputes in the future.
4. Pay attention to the domain expiry date
As we’ve briefly learned above, some cybersquatters may target expired domain names so that when the legitimate domain owner forgets to renew, they can exploit this opportunity and register the domain themselves.
If you are partnering with a reputable and reliable hosting service, typically, they’ll send several reminders before the domain’s actual expiration dates, so you wouldn’t need to worry about this too much granted you follow their instructions when they reach out. However, it’s better to be safe than sorry, so you should take note of your domain’s expiry date in order to avoid this issue.
However, a fairly common scenario is when smaller companies and startups are still not sure whether to continue their business, or the business is temporarily halted at the time of the domain’s expiration date. In such cases, it’s better to renew the domain name first (which shouldn’t cost a lot), rather than having to buy back the domains from cybersquatters at a higher price later.
5. Invest in an anti-cybersquatting solution
Thankfully, there are now software solutions and tools that are designed to help business owners combat cybersquatting, and you should leverage them to protect your business and your brand.
Red Points’ domain takedown service can help protect your brand from all types of cybersquatting in three steps:
- Real-time detection of cybersquatting websites by scouring search engines, domain databases, and social media.
- Reporting the fake domain and request for takedown by automatically contacting the domain registrant, server hosting, and CMS platform.
- Stopping repeat perpetrators by uncovering their identity and collecting data that may be required to take legal action.
6. Contact the website owner
As discussed, sometimes people simply register a domain name that is similar to yours in pure coincidence and without any malicious intent. So, instead of going to court right away, which can be expensive and time-consuming, it’s best to try to contact the domain owner on your own first and inquire about the situation.
You’d be surprised how sometimes, the domain owner will be ready to transfer the domain for free or for a small fee. Giving them the benefit of the doubt and being proactive can potentially protect your business from legal disputes and/or avoid becoming a victim of reverse-cybersquatting complaints (which can be costly).
For website visitors/clients: how to protect yourselves from being scammed
In a cybersquatting attack, the legitimate trademark owner is not the only potential victim, website visitors are also at risk of being victims, and obviously, all internet users are potential website visitors.
With that being said, here are some actionable tips you can use so you can recognize fake cybersquatted sites and prevent yourself from being scammed:
1. Always double-check the website address/URL
This is especially important when the website asks you to input login credentials, financial information, or personally identifiable information (PII). Make sure to check the address bar to make sure you are on the right site. Especially check the domain’s spelling and potential homograph (“4” with “a”, “vv” with w”, etc…).
2. Check whether the site is already using HTTPS
Nowadays, most legitimate websites owned by reputable brands or persons have used HTTPS and installed an SSL/TLS certificate. On most major browsers, you can easily check whether the website already used HTTPS by checking whether there’s a padlock sign on the very left of the address bar.
This padlock signifies an SSL/TLS certificate, symbolizing that all data transmitted between your browser and the website’s server is protected with end-to-end encryption.
While many cybersquatters are now getting smarter and more committed to their attacks by installing SSL/TLS certificates on the fake website, checking for the padlock sign can be a great start to determine whether this website is legitimate.
3. Double-check the website’s visual appearance
While a committed cybersquatter may build a fake website that looks very similar to the original website, there should still be differences, albeit subtle.
Here are some red flags you’d need to pay attention to:
- Check where CTA buttons (i.e., “download”, “buy”) point to. If they are pointed at fake pages, be very careful and check all the other signs before submitting any sensitive information.
- Too many pop-ups and advertisements can be a major red flag that it’s a fake site.
- Automatic downloads. Check the downloaded file and cancel the download if it seems suspicious.
- Redirects to unknown sites. Especially if the redirects happen frequently, it’s a clear red flag.
What’s next?
Cybersquatting can be a major threat to business owners with an online presence, especially with websites, and can cause major financial and reputational damages, as well as potential legal repercussions.
While 100% prevention of cybersquatting is very challenging to do, the actionable tips we’ve shared above can help you protect your domain and prevent cybercriminals from cybersquatting your brand. Additionally, by showing you the steps you could take in the event of cybersquatting attempts targeting your brand, you should now be aware of how to seek legal help or obtain restitution.
Nonetheless, proactive prevention and protection of your brand by implementing real-time anti-cybersquatting protection like Red Points’ Brand Protection Solution or brand abuse scan remain the best bet to protect your brand without disrupting your workflow.