Cybercriminals are working around the clock to steal from profitable brands. If cybercriminals successfully impersonate your brand to make money, what happens to you? You lose money–and reputation, as well as customer trust and loyalty. Not only that, you encourage more theft, infringement, and risk to your brand.
This is not acceptable.
Spoofing examples include using fake websites, impersonated social media accounts, and look-alike apps–all to use a customer’s confidence in you and make far more than a buck off it.
This article answers these important questions about spoofing attacks.
- What is spoofing? How common is it?
- How do spoofing attacks affect your business?
- What are common examples of spoofing?
- How can you identify spoofing attacks? How can you protect your business from them?
Read on.
What is a spoofing attack?
What are spoofing attacks? For a brand, it’s when a cybercriminal tricks a customer into believing that you or someone representing your brand is on the other side of an exchange.
Generally, the bad actors impersonate a trusted persona to reap a reward off of their victims’ misplaced trust.
Spoofing attacks, also known as spoofing scams, have two victims. The first victim, the direct target of the scam, is the customer. The second victim, however, is the brand, whose trustworthiness is made a host for the parasitic cybercriminal.
How common and prevalent are spoofing attacks?
Spoofing attacks happen every day on the internet to companies of all sizes. Everyone is a potential target, which means brand owners constantly have to keep their guard up. Ask experienced business-people who you know, they’ll likely have dealt with this problem before considering how common these scams are. In fact, in a report by World Intellectual Property Organization (WIPO) via AtlasVPN, data suggests that this year specifically, there was an increase of 10% in cybersquatting cases filled compared to last year. Cybersquatting is when someone buys a brand name domain to resell it for profit.
Cybercriminals find it lucrative to pretend to be high-performing brands. Successful companies frequently come across, for example, look-alike applications and misleading social media accounts that dupe customers. The short of it is, you won’t avoid spoofing attacks. They’re happening to you and your competitors. Make sure you do something about them. Learn how as you keep reading.
How do spoofing attacks affect businesses?
Businesses lose tremendous sums of money to cybercriminals. A significant portion comes through spoofing attacks: directly and indirectly. Your first obvious loss is the sale the fraudster took off your plate and onto his. Cybercriminals often violate intellectual property (IP) law to pull off impersonations–your trademark, for example, may have been infringed upon.
But that is not all. The same customer may have lost trust and respect in you, now all future sales from them are gone. The spoof scam may have spread malware or stolen sensitive information. That customer spreads the word to some degree, and as your business fails to remove more and more impersonators, your reputation weakens. Customer trust and loyalty diminishes.
Negative impact on revenue
The most immediate harm from spoofing attacks is sales you did not make because cybercriminals got them from you. The sooner you shut down these operations, more on that later, the sooner you regain this flow of lost revenue. The more you tolerate these crimes against your company, the more sales you lose. This happens in two ways. One, when a customer who suffered a spoof scam goes away permanently. Two, via network effects: Other customers hear about what happened and don’t come around.
Negative impact on brand reputation
What is a brand? It is knowledge inside the minds of customers and potential ones about your company. Knowledge of what? The value that you offer with your products and services. People expect a worthy brand to set itself apart from competitors. People expect a worthy brand to assert itself and protect its customers.
Negative impact on customers’ trust & loyalty
Reputation is everything. If people think cybercriminals can steal from you and cheat customers, they won’t respect you. Knowledge of your brand will include your failure to protect yourself and your customers. Customers will not trust you and they will not be loyal to you.
Don’t let that happen. Learn how in this blog post.
Common examples of spoofing attacks
Spoofing attacks take many forms, which is why it is important to understand how to handle all of them in a strategic way. What are the most costly spoofing attacks for businesses?
- Fake websites and URL spoofing, where a cybercriminal sets up a domain that misleads customers into believing that they are conducting transactions with your business.
- Social media accounts that impersonate those of your brand.
- Look-alike apps: Smartphone applications that look like yours.
Cybercriminals also combine methods of spoofing. Consider the use of fake websites mixed with email spoofing.
Indeed, the most common spoofing attack on the front end to customers is via email. Cybercriminals will create an email address that looks so similar to one from your firm that it amounts to a visual illusion, or they’ll change the “From” field. If customers reply it’ll go to you, but the spoof scam depends on customers clicking links that go to a fake website. That’s the back end of this form of spoofing. The website will look familiar and often will have a stolen logo and other brand indicators.
Other spoofing examples include:
- Caller identification (ID) spoofing, where the caller ID is modified to resemble that of your company. Another person-to-person communication scam involves text message spoofing, where the sender of the text is disguised.
- Network spoofing, where cybercriminals abuse internet protocols and layers. This includes IP spoofing, Address resolution protocol (ARP) spoofing, domain name system (DNS) spoofing
How to identify a spoofing attack
You can identify spoofing attacks on your customers based on customer complaints on social media comments and to your customer support team. Actively solicit these complaints so you can flag perpetrators sooner.
The fundamental tool for a spoofing attack is trust, the trust that your customers have (had) in you. That is why the main preventative measure for your customers themselves is vigilance. They need to know what to look out for, and you can help them do it.
2 ways brands can prevent spoofing attacks
You can have some spoofing protection to prevent revenue loss immediately without relying on anyone.
Use trademark-laden customer communications
Put trademarked brand symbols in every communication to customers. That includes email, text messages, and every webpage. This has 4 benefits for your firm:
- It’s harder to impersonate your brand, so (1) fewer cybercriminals will make the attempt, and (2) fewer customers will get fooled by attempted spoof scams.
- It’s easier to enforce your brand against spoofing attacks because you have trademark law on your side.
The final benefit is that you keep your trademarked brand symbols live this way. Trademark status stays as long as you use the symbol actively.
Protect your customers with knowledge
You can protect your customers with knowledge in 2 ways.
First, simplify what customers need to know with a tight communication policy: All company communications, sales pages, and more will have certain trademarked symbols. If the symbols aren’t present, it’s a spoof–your customers should close the tab, unfollow the account, and report the situation to you and the government.
Second, spread knowledge among your customers of how they can protect themselves from spoof scams. Write a how-to blog post and circulate it on social media. Affirm the key markers of your brand. Assert, for example, that legitimate companies like yours do not ask for sensitive information through email or text messages.
Tell them how to report spoofing attacks to government agencies like the Federal Trade Commission. Meanwhile, you can take steps unilaterally and in concert with private sector revenue recovery firms. Let’s start with what you can do on your own.
H3 – How Red Points can protect businesses from being targeted in a spoofing attack
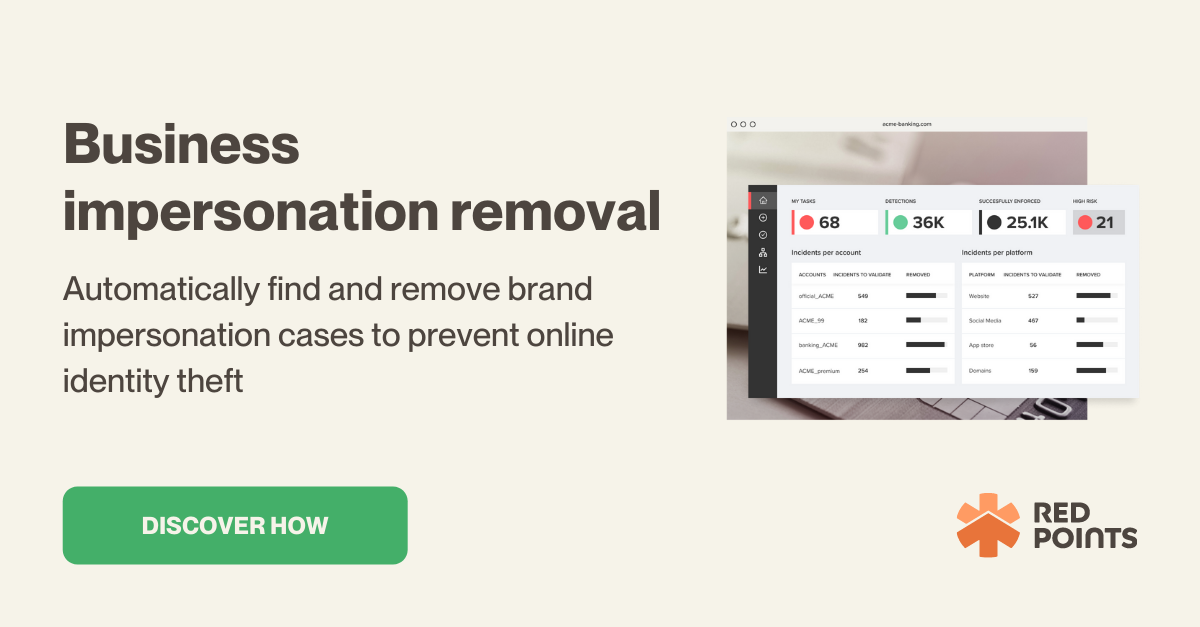
Do you want to enforce your brand identity and protect your customers? Red Points offers spoofing protection for businesses. Over 1,000 companies use our platform to recover stolen revenue.
Our impersonation removal techniques target the biggest sources of revenue loss for businesses flowing from spoof scams of customers. In addition to look-alike applications, use our domain takedown service to run down and eliminate fake websites stealing your sales. Try our social media protection tool to trim and dispose of social media accounts masquerading as yours.
What’s next
Spoofing attacks are common. If you’re a profitable business of any size, they will happen to you if they aren’t already underway. Spoof scams take money from you and your customers. Spoof scams give customers no value when you could have and you will get part of the blame. Your brand will lose trust and loyalty. Your brand will suffer reputational damage. That’s revenue loss in the short term and the long term too.
You shouldn’t tolerate this.
But spoofing protection is viable in partnership with a revenue recovery service. Consider ours. We will help you reinforce your brand identity, enforce your IP rights, and make sure you get your money back from the cybercriminals who stole it.