Just identified someone pretending to be your company attempting to scam your customers or clients?
You’ve just experienced a cybercrime activity we call “spoofing.”
In this article, we will discuss all you need to know about spoofing and what to do when someone pretends to be your business.
By the end of this guide, you’ll have learned about:
- What spoofing is
- Different types of spoofing,
- Negative impacts and risks of spoofing attacks
- How to protect your business from being impersonated by others
Without further ado, let us begin this guide right away.
What is spoofing?
Spoofing, also called brand impersonation or brand abuse, is a type of cybercrime in which the perpetrator impersonates an established institution (government institution, famous business, celebrities, etc. ) to trick people into performing security mistakes, especially divulging personal and/or sensitive information.
As with most other criminal activities (including most cybercrimes), financial reasons are the primary motivation behind most spoofing activities, and there are several ways cybercriminals can monetize spoofing, including:
- Monetizing stolen sensitive/personal information:
- Using stolen credit card numbers to purchase goods (or other techniques to monetize the purchase)
- Sell the stolen personal information on the dark web
- Use stolen accounts to run scams
- Infecting user devices with malware:
- Turning the infected devices into botnets to launch DDoS attacks (which can be monetized in many different ways)
- Infecting devices with ransomware and extorting the owner
- Steal sensitive/confidential company data
Spoofing can happen on many different platforms: fake websites pretending to be your website, emails with spoofed domain names, fake social media accounts, fake phone calls, and even fake text messages. Spoofing can also be more technical, like performing spoofing on IP addresses, DNS (Domain Name System), and ARP (Address Resolution Protocol).
The anatomy of a spoofing attack
While there are many different variations of spoofing attacks performed by cybercriminals, typical spoofing relies on two different components:
- The “spoof”: a fake website, fake social media account, fake IP address, and so on. The role of the spoof is to win the target victim’s trust.
- Social engineering: the content within the spoof that encourages the target victim to take action. For example, the email may claim that the victim (recipient) just won a contest and then urge the victim to click a link pointing to a fake login page, providing a convincing rationale for the victim to enter their credentials (i.e., “log in to claim your prize.)
For a spoofing attack to work, the social engineering aspect of the attack must be able to manipulate the victim into taking the desired action, like divulging sensitive information, authorizing a wire transfer, making a purchase, etc. This is typically achieved by using two main techniques:
- Offering something valuable: winning a contest, free tickets, etc.
- Scaring the victim with a fictitious threat: “your account will be locked,” etc.
Either by tricking the victim into believing the offer of the threat is real, the perpetrator will then urge the victim to take immediate action, like changing their passwords on the fake login page, clicking and downloading an attachment, etc.
How can spoofing impact your business
Once the spoofing attack has been successful in convincing its victim to take action, it can result in several consequences, including but not limited to:
- Stolen credentials, allowing the perpetrator to gain access to the account. They can then use the account in further attacks.
- Stolen personal or company information (data breaches)
- Malware infection
- Bypassing access controls
- Gaining unauthorized network or system access
In turn, these consequences can impact the business in three different ways:
1. Financial damages
Successful spoofing attacks can affect the business financially in several different ways:
- Extortion: for example, the spoofing attack may result in the company’s network system being infected by ransomware, locking the company from critical files or documents before they pay a ransom to the attacker. Newer threats like data exfiltration can also cause serious financial damage.
- Lower revenue: failure to take down spoofed websites or social media accounts, for example, can result in the loss of trust from your customers, so they stop buying from you. Partners and investors may also stop their funding for the same reason, causing further financial issues.
- Higher security costs: to combat spoofing attacks or to stay compliant with newer cybersecurity regulations, the business may be required to invest in more security solutions and infrastructure, as well as in manpower (security experts and/or team) and insurance premiums.
- Legal costs: the business may need to pay for legal help in the event when they are a victim of successful spoofing attempts or to stay compliant with cybersecurity regulations.
In short, spoofing attacks and other cybersecurity threats may be financially costly for any business.
2. Long-term and permanent reputational damage
A recent study suggested that 1 in 4 surveyed Americans would stop doing business with companies that recently experienced a data breach, which is a common consequence of spoofing attacks.
Reputation is a very valuable asset in today’s digital environment: consumers will only purchase products or services from brands they can trust. On the other hand, the credibility and reputation you’ve built for years if not decades, can be completely ruined by just a single successful spoofing attack.
3. Legal issues
Failure to protect your business from spoofing attacks, data breaches, and other cybercrimes may result in legal repercussions, and your business may be held liable.
Back in 2013, hackers spoofed Target’s credit card readers, resulting in the successful theft of more than 110 million Target shoppers. This case ends up costing Target $162 million in settlements.
Common types of spoofing targeting businesses and enterprises
1. Website spoofing
Cybercriminals may use techniques like website cloning/mirroring to build a fake website that is the exact carbon copy of the legitimate website, which can trick both customers and employees of the company into making security mistakes.
Unfortunately, cybercriminals are becoming more adept at performing website spoofing, and they may combine it with different spoofing techniques (i.e., DNS spoofing) to make it very difficult to differentiate between fake and legitimate websites.
Website spoofing is often used in a multi-pronged attack vector (i.e., in combination with a phishing email linking to the website) to distribute malware, steal sensitive information, trick victims into wiring money, conduct fully-fledged identity theft, and so on.
2. Email spoofing
Perpetrators may perform email spoofing with many different techniques, the two basic ones being:
- Impersonating an email address from a well-known domain name using different characters and/or numbers that look similar to the legitimate address (misspelling.) This is mainly done via typosquatting (registering misspelled domain names.)
- Modifying the email header so that the sender address that is shown in the “form” field looks similar to the legitimate one while actually coming from a different source.
Typically the perpetrator will send an email containing a malicious downloadable attachment or a malicious link pointing to a fake website with a phishing scheme, resulting in the recipient’s device being infected by malware, the victim divulging their sensitive information on a phishing website, or other negative impacts.
3. Caller ID spoofing
By spoofing the caller ID, the perpetrator can falsify the information transmitted to the victim’s caller ID to disguise their identity, typically impersonating phone numbers of established institutions (i.e., banks).
Once the victim picks up the phone, the perpetrator will then use psychological manipulation techniques to convince them to disclose their personal or sensitive information over the phone, like passwords, Social Security numbers, banking/credit card information, and more.
4. IP address spoofing
A little bit more advanced than the other types listed above, here the cybercriminal uses spoofed IP addresses to either:
- Mask its identity, or
- Impersonate another computer
One common application of IP spoofing is for the perpetrator to gain access to networks that authenticate users based on IP address.
However, IP spoofing is also commonly used in DDoS attacks, allowing the attacker to overwhelm the victim with a high volume of traffic by sending packets to the victim while redirecting the victim’s reply to the spoofed (fake) IP, confusing the victim’s device/network and disrupting its operations.
5. ARP spoofing
ARP (Address Resolution Protocol) is a type of protocol that resolves internet layer addresses (i.e., IP addresses) into link layer addresses (i.e., MAC addresses.)
Also known as ARP cache poisoning or ARP poison routing, ARP spoofing allows the attacker to send spoofed ARP messages onto a target local area network (LAN), mainly to associate the attacker’s MAC address with the IP address of another host.
ARP spoofing is commonly used to steal or perform unauthorized modification of data but can also be used in DDoS attacks, man-in-the-middle attacks, or session hijacking attacks.
6. DNS server spoofing
DNS server spoofing is another technique that can be used by cybercriminals in pretending to be your company.
A DNS (Domain Name System) server’s main function is to resolve URLs and email addresses to a matching IP address. So, a spoofed DNS allows attackers to redirect traffic to a different IP address even if the victim is inputting the right URL (i.e., your company website’s legitimate URL) so that the victim will visit a fake and malicious website instead.
How to protect your business from spoofing attacks
Preventing your brand from being impersonated by spoofers and scammers is crucial in maintaining a positive reputation and online presence.
We call any efforts taken by businesses to protect their brand and trademarked intellectual properties (IPs) Digital Brand Protection, and below, we’ll share some actionable tips you can use to implement digital brand protection and report/take down imposters:
1. Establish a strong brand identity
Before anything else, you’ll need to set a solid foundation for your digital brand protection by having a strong brand identity that is easily recognizable.
The ideal scenario is that in the event of impersonation, your audience should be able to recognize your legitimate branding elements. At the very least, having unique brand elements would make it more difficult for the impersonator to copy your brand elements.
While every business is unique and may require different elements of branding, you should focus on developing the following universal elements:
- Logo: the most important element of your brand and should clearly represent what your business is all about.
- Color scheme: The color palette should represent your brand’s key values and personality traits while giving it a unique look.
- Tone of voice: including vocabulary. One of the most effective ways to shape how your audience perceives your brand, and often the most difficult to impersonate.
- Fonts: Choose a unique font (ideally one that isn’t freely available) that can also communicate your brand’s personality and values.
- Imagery: choice of photos, images, and style of graphics you use throughout your content. It can be the most difficult to impersonate when done right.
2. Claim and protect your intellectual property rights
Once you’ve developed and established your unique brand elements, the next step you should take is to legally claim your intellectual property (IP).
Claiming your IPs provides you with legal protection in the event of someone pretending to be your company. You’ll have more control over how your brand is presented to the general public and can get appropriate legal help when others try to exploit your brand in bad faith.
There are at least four ways you should claim your IPs to protect your brand identity:
- Domain name: a very important element of brand identity in this digital age, and you should register your domain names (and relevant variations) as early as possible in your business’s lifecycle to prevent cybersquatting or domain squatting.
- Trademark: trademark your brand name and product/service names to separate your brand from your competitors.
- Copyright: protect your brand’s digital and physical creative assets (i.e., product design, official product photos, logos, etc.) by registering their copyrights.
- Patents: if your product uses innovative technology or sufficiently unique design, you can register these unique inventions for patents.
3. Active and automated brand monitoring
Unfortunately, claiming your IPs won’t stop malicious cybercriminals from pretending to be your company and exploiting your brand identity.
Ideally, you should conduct a 24/7 monitoring of all your brand assets, but obviously, this will be too difficult and time-consuming to do.
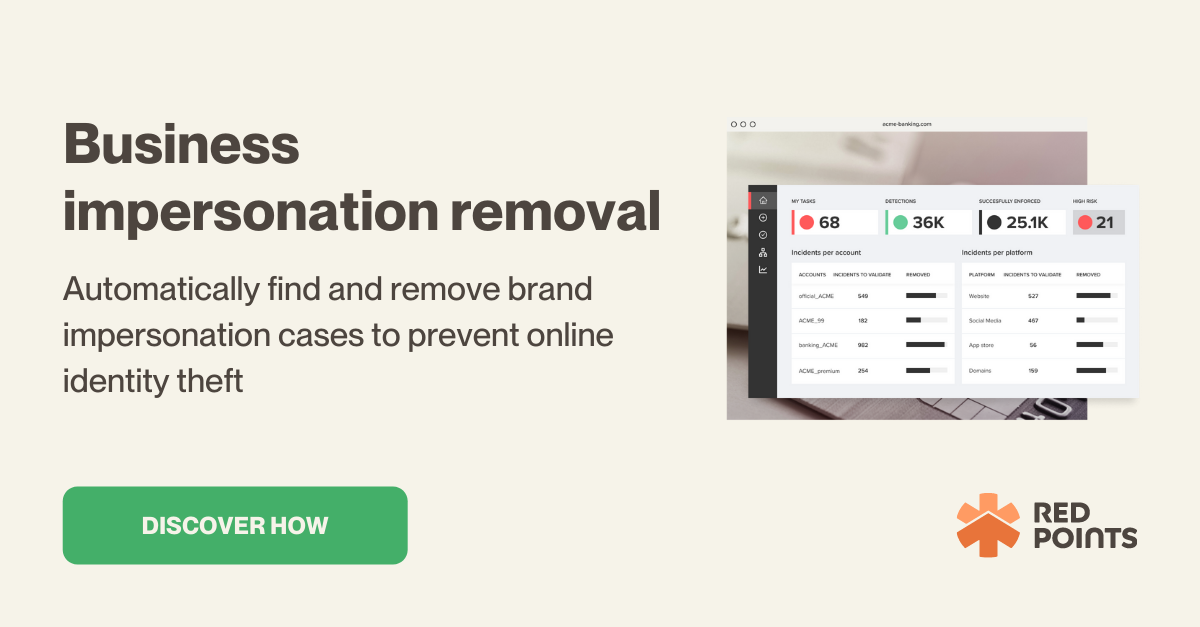
Red Points make the entire process easier. With Red Points’ Impersonation Removal Software solution, you can automate the process of finding and removing fake accounts, apps, websites, and domains, allowing you to continuously protect your brand identity and reputation in real time.
Red Points’ solution uses AI-powered search technology to scan the internet 24/7 for any kind of brand impersonation and stops these impersonations through automatic enforcement, reporting, and takedown.
How to protect your customers from cybercriminals pretending to be your company
Your customers are actively being targeted by cybercriminals pretending to be your company with various spoofing attacks, which can result in significant damages in many different forms.
It’s crucial to educate them so they can recognize spoofing and phishing attacks as soon as possible, suggesting the following best practices:
- Always start with no, and be reasonably skeptical with any offers you receive via text, phone, email, or social media that seem too good to be true.
- Always double-check the sender; make sure it’s really someone you know and/or an authorized sender from an established company.
- Be extra careful before clicking on any email or text message attachments.
- Use a VPN service and be extra careful when accessing the internet via public wi-fi.
- Scam emails tend to have typos and grammatical errors, so carefully read the email or text content. Also, be reasonably suspicious if the content seems not to be well-written. Check for proper use of punctuation marks.
- Use strong (long and complex) and unique passwords for each of your accounts, so when one account is compromised, the others are safe.
- Use two-factor authentication as an added layer of protection in the event when your password is compromised in a spoofing attack.
- In general, unless you are 100% sure, don’t share sensitive and personal information like full name, Social Security number, phone number, address, or banking details.
- Never share your password or OTP. There are very rare cases (if not never) when an established institution asks for your password over the internet.
- Be extra careful when you get sudden pop-ups urging you to take immediate action when browsing a website or opening an email. This is a very common method used in spoofing attacks.
What’s next
To protect your business’s brand identity online presence, you should consider establishing a comprehensive Digital Protection Solution in order to protect various forms of your digital IPs: brand name, website, Google Maps listing, social media handles, logo usage, and so on.
Preventing brand abuse attempts and mitigating their impacts are crucial for protecting your reputation. We should always remember that reputational damage can be severe and long-term, if not permanent. Digital brand protection can also protect your business from potential legal repercussions and financial losses.