Website spoofing, or domain spoofing, is a popular form of cybercrime where fraudsters create websites imitating legitimate brands. These spoofing sites are often designed to trick unaware users into sharing sensitive personal or financial information. The sophistication of such attacks varies—some sites are amateurish and easily recognizable, while others are nearly indistinguishable from the genuine website, leading to potentially catastrophic outcomes for brands.
There can be different motivations behind website spoofing. Beyond the obvious intention of stealing users’ sensitive data, these fraudulent sites may also aim to steal business from legitimate enterprises by creating convincing competitor sites. In some cases, they trick users into downloading malware, which can further harm them by compromising their computer systems or stealing even more data. Another fraudulent outcome includes impacting legitimate businesses’ search engine rankings through the creation of duplicate content, a tactic that diminishes the visibility of the original website in search results. Moreover, spoofed websites can serve as tools for impersonation, damaging a brand’s reputation by associating it with malicious products and services.
The threat posed by website spoofing is significant and growing. In the second quarter of 2023, around 1.28 million unique phishing sites were detected worldwide—a figure that, while already alarming, likely underestimates the full scope of the problem given the blurred lines between phishing and website spoofing. These fraudulent websites can nowadays be created more easily due to technological advancements that have lowered the barrier to entry for cybercriminals, allowing individuals without advanced technical skills to launch attacks that can deceive even the most cautious internet users.
In the digital environment, fighting against new spoofing tactics of cybercriminals becomes difficult for companies, cybersecurity experts, and average internet users. Understanding the mechanisms behind website spoofing can help businesses develop effective tactics for protecting their brands against fake websites.
A website is a vital tool for any business, so businesses should be aware of how website spoofing works, as well as how to prevent it from happening to your brand. In this article, you’ll learn:
- What is website spoofing?
- How does website spoofing work?
- Technical mechanisms behind website spoofing attacks
- The difference between website spoofing and phishing
- Examples of website spoofing
- How to prevent website spoofing
- Step-by-step guide to prevent website spoofing
What is website spoofing?
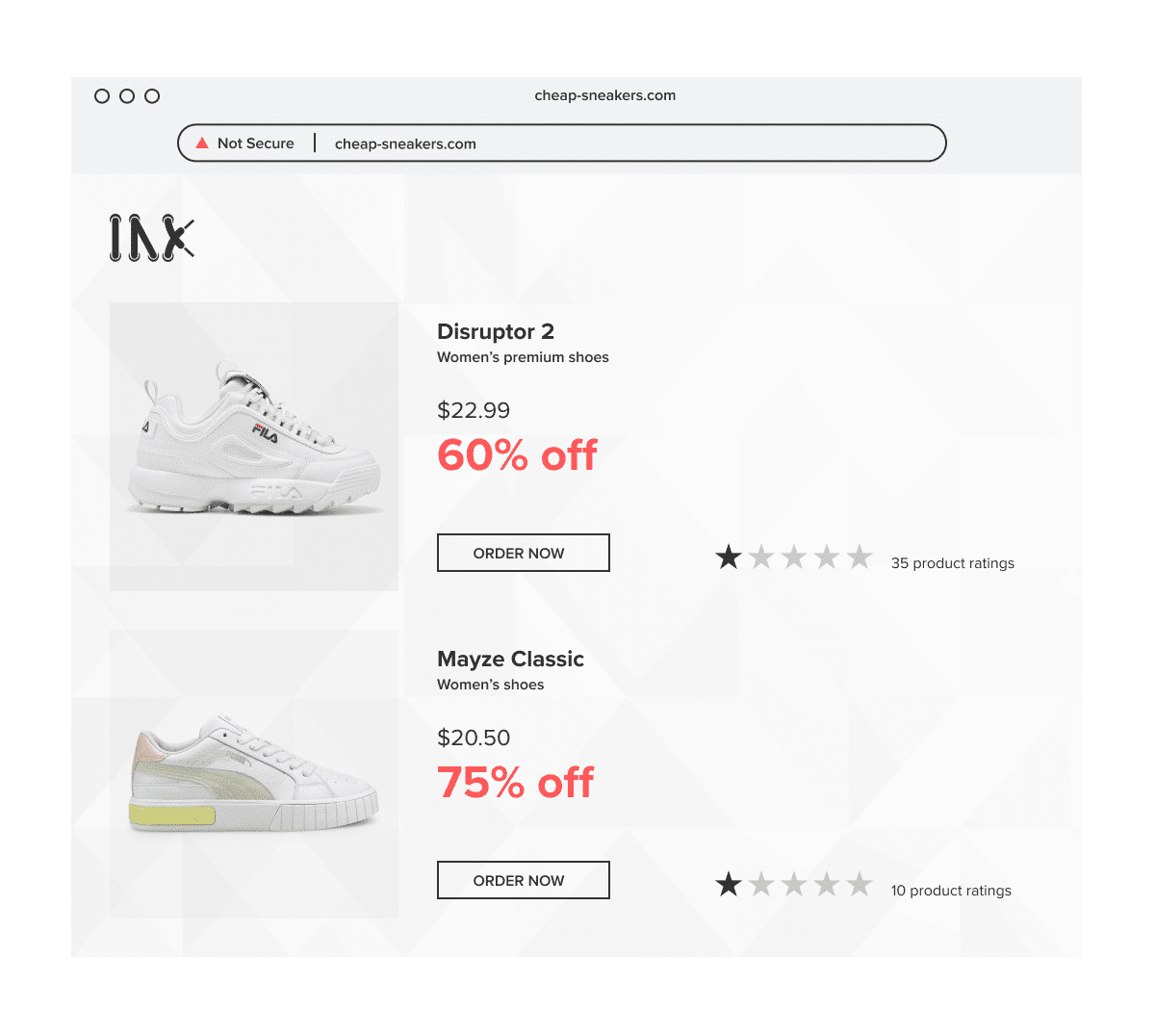
Perhaps you’ve landed on a brand’s website before and felt something was off about it. The grammar was bad, and the quality of the website didn’t match the prestige associated with the brand. The chances are you have landed on a spoofed website.
Website spoofing occurs when a scammer copies a brand’s intellectual property (IP), such as their logos, content, product lists, and domain name, for example. They weave these into a website so that it looks like the official website of a brand. The aim is to trick the user into believing they are on a legitimate website so that the user spends money or shares their details, such as usernames and passwords. Scammers may also be out to infect your computer with malware.
It is vitally important that brands don’t allow their website to be spoofed, and take down fake websites as soon as they appear. While spoofed websites are essentially stealing sales that should otherwise have gone to your brand, the biggest impact will be felt by your brand reputation. Once customers begin having bad experiences associated with your brand – even if it was a scammer purporting to be your brand – it’s difficult to undo the damage.
How does website spoofing work?
- Copy your website
There are very few barriers to entry when creating a lookalike website. All the scammer has to do is to copy identifying elements of your brand, such as your logo, tagline, product list, and content, for example. This way, a user will be tricked into thinking they have landed on a legitimate website.
Whether or not you’ve registered the identifying elements of your brand for trademark and copyright, copying your website is a significant infringement of your brand’s copyright and trademark.
- Domain name spoofing
For their scam website to pass as your original, legitimate one, scammers will spoof your domain name. Of course, scammers cannot simply register the same domain name, but they come up with ways to get around this. Typosquatting is a method used by website spoofers, where they create typoed versions of your website address. Perhaps they write amzon.com instead of amazon.com, or they will modify the ending of your domain name, such as by using .net rather than .com. Similarly, cybersquatting is when cybercriminals use slightly altered versions of the domain name, like g00gle.com.
- Use blackhat SEO techniques, social media, email, and text messaging
In order for scammers to steal your details or money, they have to first get you to their spoofed website, and they often do this through phishing techniques. To do that, they may send you a text message or an email with a link to their website, or they may create fake social media accounts leading you to their site. The more sophisticated criminals are capable of manipulating search engine results through black hat SEO techniques so that their website ranks highly.
Technical mechanisms behind website spoofing attacks
It’s essential to highlight how the technical mechanisms of website spoofing attacks work and how SSL certificates can mitigate the security threat posed by such attacks, the process of DNS spoofing, ARP spoofing, and the use of SSL certificates. Below you can find the technical aspect in detail:
DNS spoofing
DNS spoofing, commonly referred to as DNS cache poisoning, is the process of compromising the DNS address record of an internet server to reroute traffic to a harmful website posing as a legitimate one. This may result in the leakage of private data or the transmission and installation of malware.
How it happens:
Interception: By gaining access to the communication between a user and a DNS server, an attacker can intercept and alter the DNS query.
Malicious redirection: The attacker sends a falsified DNS response before the legitimate server can respond, directing the user to a malicious site instead of the intended one.
Preventive measures:
- Use DNSSEC (DNS Security Extensions) which provides a layer of authentication with digital signatures based on public key cryptography.
- Configure DNS servers securely, ensuring they resist cache poisoning and unauthorized access.
ARP spoofing
ARP spoofing, or ARP cache poisoning, is a technique used to send fake Address Resolution Protocol (ARP) messages to a local network. This manipulation results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network.
How it happens:
ARP broadcast: The attacker sends false ARP responses into a local network.
Traffic misdirection: Network traffic intended for a specific IP address can be mistakenly sent to the attacker’s system.
Preventive measures:
- Employ static ARP entries, though this is impractical on large networks.
- Use packet filtering to filter out malicious ARP packets.
- Implement Dynamic ARP Inspection on switches which can prevent invalid and malicious ARP packets.
Role of SSL certificates
SSL (Secure Sockets Layer) certificates play a crucial role in preventing spoofing by encrypting the connection between a user’s browser and the server, making intercepted traffic unreadable to anyone except the intended recipient.
How SSL helps:
- Authentication: SSL certificates ensure that the server you are connecting to is the one it claims to be.
- Encryption: Encrypts the data transferred, preventing it from being read or tampered with.
- Data Integrity: SSL provides a mechanism for detecting any alterations to data during transmission.
- Preventive Role: SSL certificates help prevent man-in-the-middle attacks, where attackers could otherwise intercept and alter communications between two parties.
Implementing SSL certificates
- Choose the right certificate: Depending on the level of security needed, choose between domain-validated, organization-validated, or extended validation certificates.
- Regular updates: Keep your SSL certificates up to date and revoke any that may have been compromised.
- Use HTTPS: Ensure that your site uses HTTPS, not HTTP, to secure all communications.
By understanding these technical mechanisms and effectively implementing SSL certificates, organizations can enhance their cybersecurity measures against various forms of website spoofing attacks. This not only protects sensitive data but also builds trust with users by ensuring secure communications.
Spoofing vs Phishing: What’s the difference?
Phishing and spoofing are terms that are often used interchangeably. Part of the confusion comes from the fact that fraudsters often use both practices in tandem.
According to The Cyberwire glossary, phishing is:
“…the delivery of a ‘lure’ to a potential victim by pretending to be some trustworthy person or organization in order to trick the victim into revealing sensitive information”
Phishing is, in other words, a social engineering tactic used to lure you into sharing sensitive information, such as social security numbers, financial information, login details, and bank account numbers. Bad actors may use emails (as with executive impersonation emails), telephone, or other methods to trick you into clicking on a malicious file or revealing private information.
Website spoofing is similar to phishing, but it is centered around communications that masquerade as though they are from a legitimate source. The Cyberwire glossary defines spoofing as:
“…an attack technique that relies on falsifying data on a network in a way that enables a malicious site or communication to masquerade as a trusted one”
The aim is to get users to believe they are interacting with the original, trusted source and to share their personal information. Website spoofing often happens in conjunction with phishing. For example, a phishing email may link to a spoofed website. Spoofing is usually weaved into the phishing process in some way, as a means of gaining the user’s trust.
Is website spoofing illegal?
Creating a spoofed website is not illegal if the aim is to parody another brand as long as the comical intention is clear. The kind of website spoofing we have been discussing in this article, however, is in violation of any laws.
As with a lot of digital fraud, there are usually more laws than one that is being transgressed. For example, spoofing a website will always be infringing copyright and/or trademark law, since to spoof a website the fraudster has to copy identifying elements of the brand. If the scammer is to use the information given by the unsuspecting user, then this would be in violation of 18 U.S. Code 1029 – “Fraud and related activity in connection with access devices” if the scam was taking place in the US.
There are plenty more laws that can be broken by scammers who spoof websites; these are just a small selection so that you know your rights as a business owner.
Examples of website spoofing
One particularly nefarious website spoofing example is when a scammer creates a website that impersonates a bank. They will usually draw you to the fake website via phone calls, emails, or screen-sharing software. Once you’re there, they may collect the information you put into the false security checks, install malware onto your computer, or request a bank transfer.
Fake ecommerce websites are popular among spoofers. There are two types of fake online stores: those that aim to harvest details or money from unsuspecting shoppers, and those that pretend to be a legitimate brand but sell counterfeit items. Both are highly damaging to customers and legitimate businesses.
How to prevent website spoofing
- Automated software
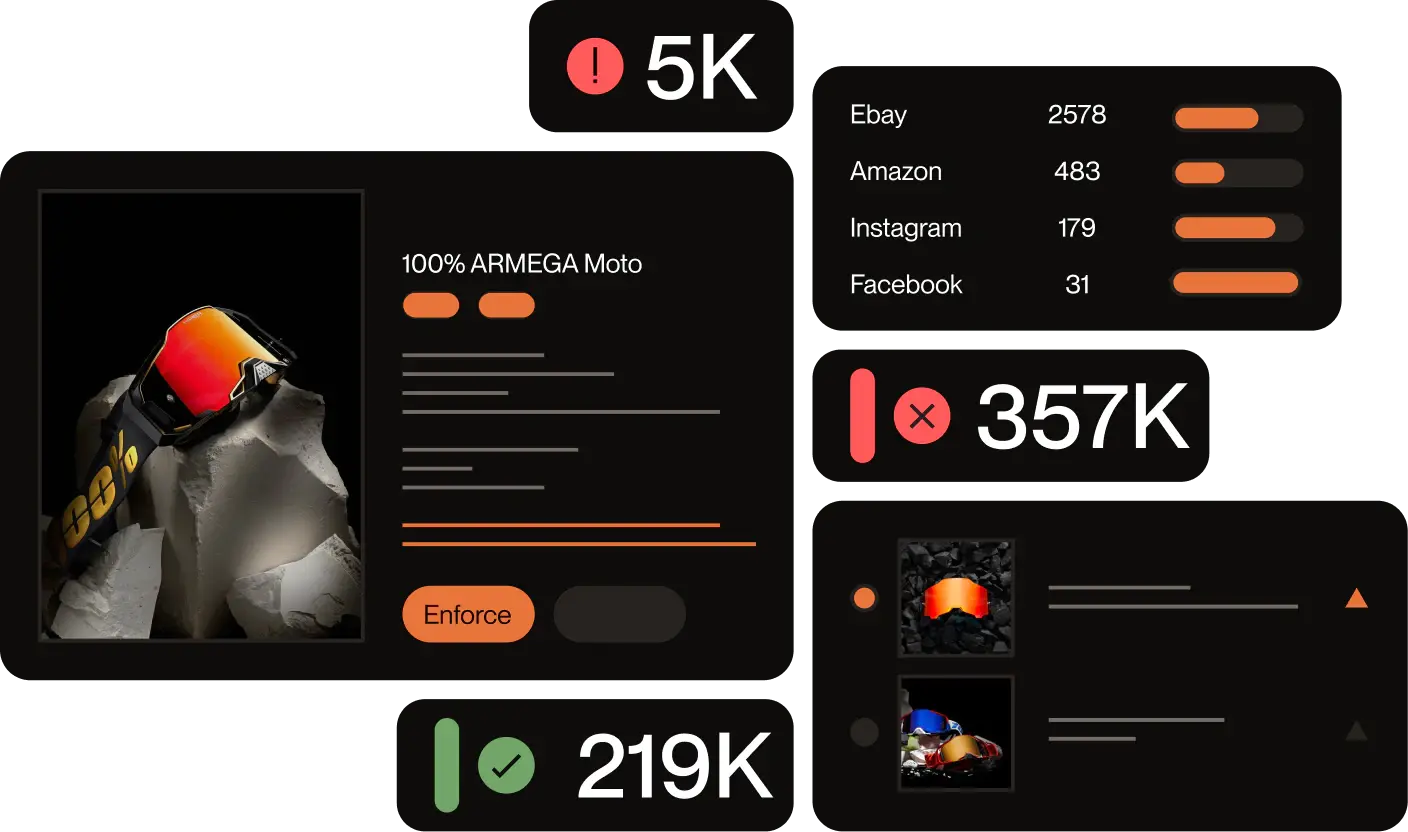
How do you even know your website is being spoofed until it’s too late and a customer leaves you a terrible review? The best way to detect and prevent website spoofing before it starts ruining your brand reputation is through automated, 24/7 brand protection software. Red Points’ Domain Monitoring Service is constantly scanning the web for any suspiciously similar websites and sending out automatic takedown requests to hosting providers or registrars.
- Register your trademark and copyright
While everything you create is covered under copyright or trademark law, you may not be protected in a court of law unless you officially register your business trademarks and copyright your content. Even if you are not registered, you can still legally put the trademark and copyright signs on your website, which might just help to scare off unscrupulous copycats.
- Educate your customers and employees
It’s important to let your customers know how and when you would ever ask them for sensitive information. For example, many banks have notices on their websites reminding their customers that they will never ask for their card details over the phone or via email. Likewise, with your employees, you should ensure that certain checks are met before money or information is transferred and that there is a well-established process in place.
What’s next
Fake websites are being created by the thousands every day. Many of them are spoofing websites whereby lookalike scam sites replicate those of a trusted brand. Being taken in by a fake website is a distressing experience for any customer, and ultimately, this will affect the brand reputation of the original business. This may seem unfair, but as any business owner knows, your brand reputation is one of your most vital assets. Once scammers begin creating lookalike versions of your brand, your reputation is no longer in your control.
Luckily there are website spoofing prevention measures you can take. The most effective one is to install automated software. You can get a domain takedown service and remove spoofing sites that take advantage of your brand with Red Points’ Domain Takedown service. That way, you can concentrate on improving your brand while Red Points focuses on keeping your brand safe from copycats.