In 2022, brand impersonation cost businesses in the U.S. more than $660 million. In today’s digital landscape, brand impersonation is a growing concern because it is causing significant financial losses, inflicting damage to the reputations of legitimate brands, and eroding the trust consumers place in the market.
To ensure that you can protect your brand from impersonators you need to learn as much as you can about brand impersonation and then start implementing measures to protect your business. While manual methods are useful for small-scale impersonation, many of the most effective strategies involve automation and digital technology.
In this blog, we explore the top ways to protect your brand from brand impersonation by highlighting a number of topics, including:
- What is brand impersonation?
- Examples of brand impersonation
- How to protect your brand from brand impersonation
- Brand Impersonation Protection Software: is it worth it?
What is brand impersonation?
Brand impersonation is a kind of cyber-attack in which scammers pose as legitimate brands in an attempt to take advantage of consumers. Often the goal of brand impersonators is to get consumers to give over sensitive information or money.
The impact on brands can be substantial. Businesses targeted by impersonators will often lose revenue as consumers will mistakenly buy the impersonator’s products rather than those of the legitimate brand. Equally, if brand impersonation is allowed to spread unchecked, it can damage your reputation and reduce the level of trust consumers then place in your products and messaging.
Examples of brand impersonation
Brand impersonation comes in a variety of forms. Here are a few real-life examples of the types of brand impersonation scams your business is likely to come across while operating online:
- Domain squatting
Domain squatting, or cybersquatting, is a digital scam that involves buying up generic top-level domains in order to prevent others from registering, reselling, or monetizing them. In 2022 alone, the World Intellectual Property Organization (WIPO) received 5,423 new cybersquatting cases.
Scammers will often then impersonate brands using these domains in order to trick users into giving over their personal and financial information. Domain squatting is a common scam that takes advantage of unwitting consumers and brands that are complacent about their brand protection strategies.
- Fake social media profiles
Most brands use social media to promote their products and interact with online consumers. Some bad actors target these interactions by creating fake social media profiles.
They will impersonate brands on Instagram, TikTok, Twitter, and other platforms to redirect users to fake websites that will steal their information, infect them with malware, and trick them into buying fake products.
- Email phishing campaigns
Email phishing involves impersonating a brand in order to gain sensitive information from customers. Scammers will send emails posing as legitimate brands and trick customers into giving over passwords, bank account numbers, telephone numbers, and social security information.
It is a common type of impersonation scam that is becoming increasingly sophisticated as more scammers perform AI-generated phishing attacks as they turn to AI platforms to help them write convincing fake emails.
- Counterfeit product sales
Some scammers will impersonate brands on popular marketplaces in order to sell counterfeit products. Impersonates will copy logos, product images, and product descriptions to deceive consumers into thinking they are interacting, and buying from, legitimate brands. Counterfeit product sales will both cut into your revenue and deliver poor customer experiences that may damage your brand.
- Fake mobile applications
Impersonators will also create fake mobile applications to place on a variety of app stores in order to take advantage of brands that attract a lot of mobile users.
Today, many brands use mobile apps to ensure their products and services are accessible to the widest range of possible users. However, if you are not constantly monitoring these app stores you may become vulnerable to impersonators that make cheap versions of your app that will take advantage of your brand.
How to protect your brand from brand impersonation
You have to be proactive if you want to protect your brand from brand impersonation attacks. Here are a few of the simple steps your brand can take to protect itself from brand impersonation:
- Regular monitoring with Google Alerts
Before you can begin to deal with impersonators, you need to find them. One simple way you can begin this detection process is by setting up Google Alerts associated with your brand.
This accessible Google tool allows you to monitor any keywords or keyword phrases. If you focus on keywords that relate to your brand you will be able to monitor when impersonators are posting fraudulent versions of your content anywhere on the web.
- Register your domains and Intellectual Property (IP)
You should then strengthen your content portfolio by registering your web domains and intellectual property at the relevant bodies. For example, if you want to protect your trademarks you can register them at the U.S. Patent and Trademark Office. You can register your domains at Google Domains or in many other domain registration platforms.
By registering your domains and IP, you will have a foundation to enforce your rights and pursue impersonators who may have infringed those rights. Owning your intellectual property will also help you report incidents of impersonation on social media platforms and marketplaces.
- Collaborate with platforms
You should actively collaborate with platforms to help them crack down on users who are violating their policies by impersonating your brand. Record any evidence of impersonations and submit it to them via the appropriate channels.
Many platforms, like Instagram, have dedicated services to allow you to report intellectual property violations and bring brand impersonation issues to their attention.
- Strengthen your brand and connection with customers
You can also protect your business from impersonators by strengthening your brand and establishing robust relationships with your customers. If your brand has a solid online presence it will be harder for scammers to impersonate your brand and get away with it.
Customers are the first line of defense. Talk to them and make them aware of the risk of impersonators. Encourage them to report any suspicious interactions or potential signs of impersonation.
Brand Impersonation Protection Software: Is it worth it?
The manual steps described above are useful but limited. If you want to deal with large-scale issues of brand impersonation these manual approaches will usually not be particularly cost-efficient or effective. Instead, the solution lies in automation and specialization.
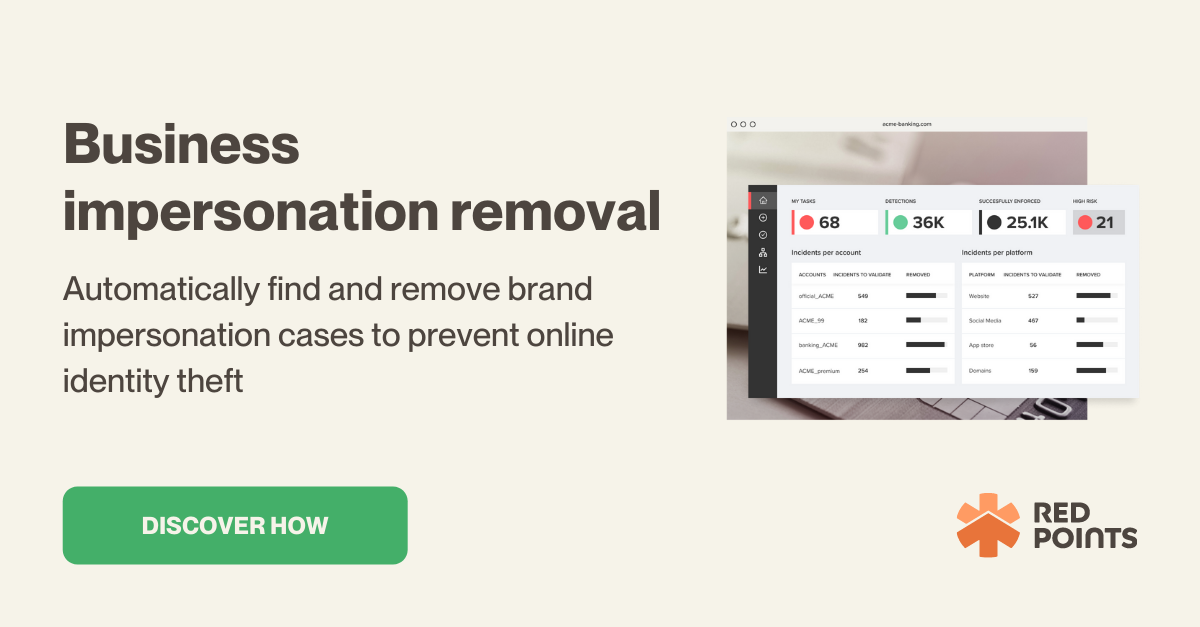
Red Points’ Impersonation Removal software is an automated solution that will empower you to take down fake accounts, apps, sites, listings, and domains. With advanced technology, tailored workflows, and world-class experts we are able to offer brands comprehensive protection from impersonation.
Here’s how it all works:
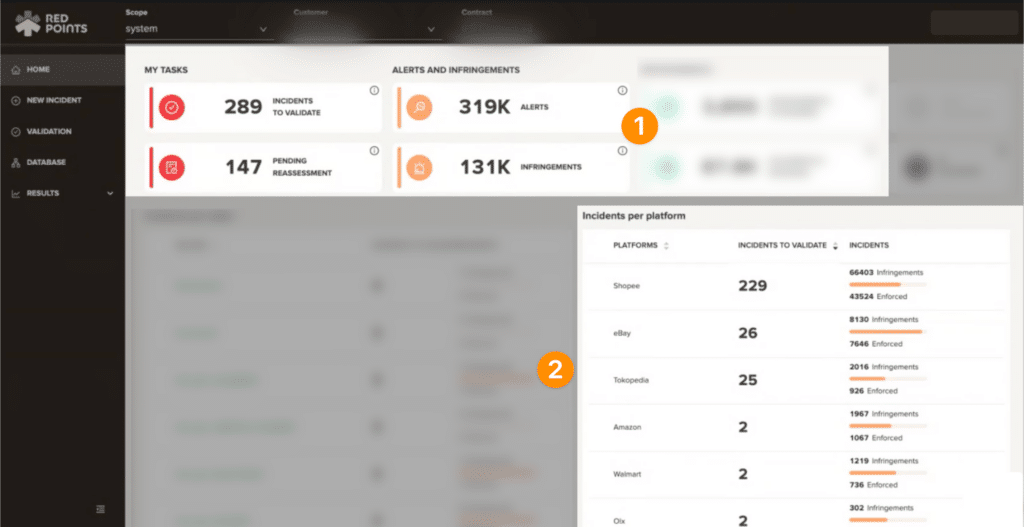
- Detect
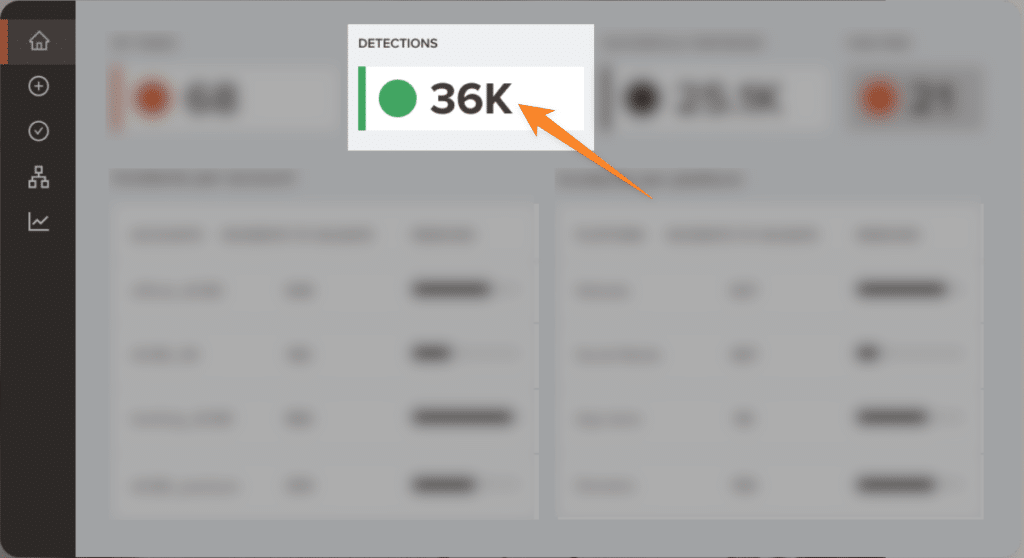
Our automated bot-powered search allows us to find thousands of impersonations within seconds. We scour social media, marketplaces, and third-party sites looking for signs of impersonation that may be linked to your brand. We collect these detections in a list for you to review.
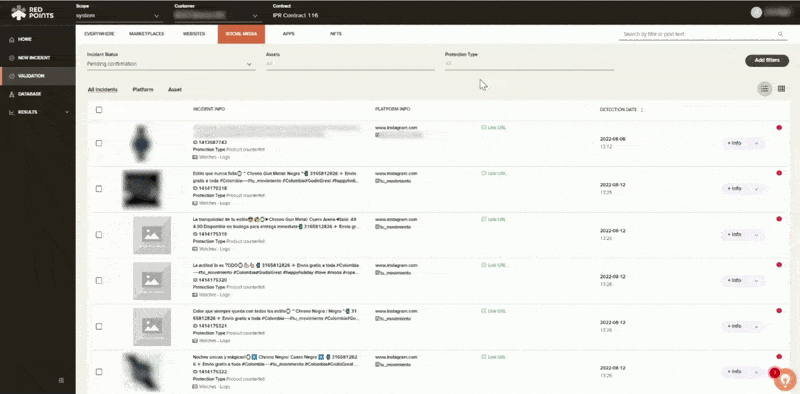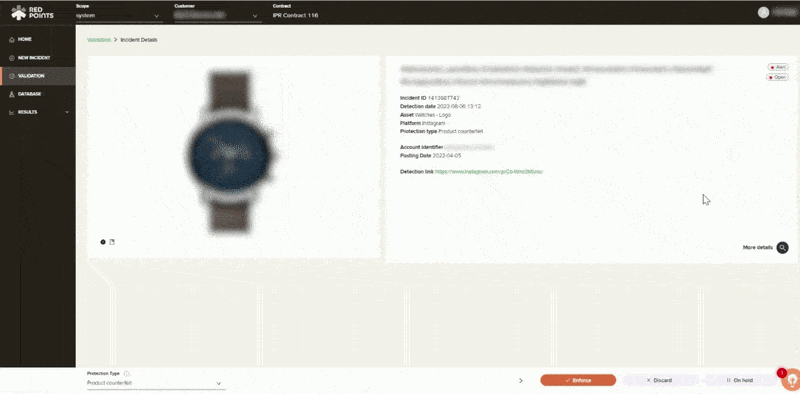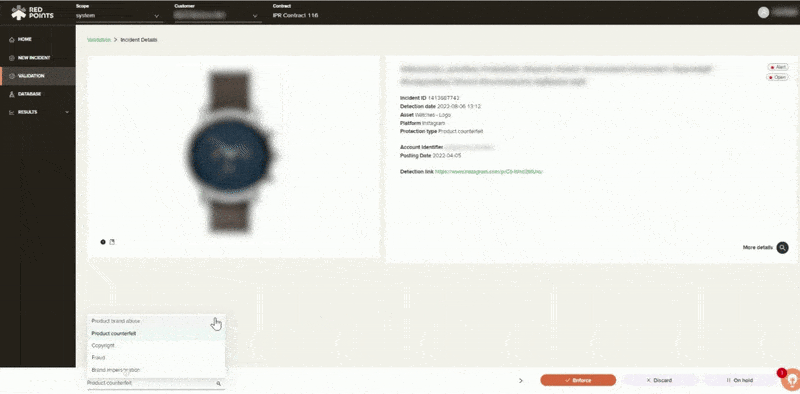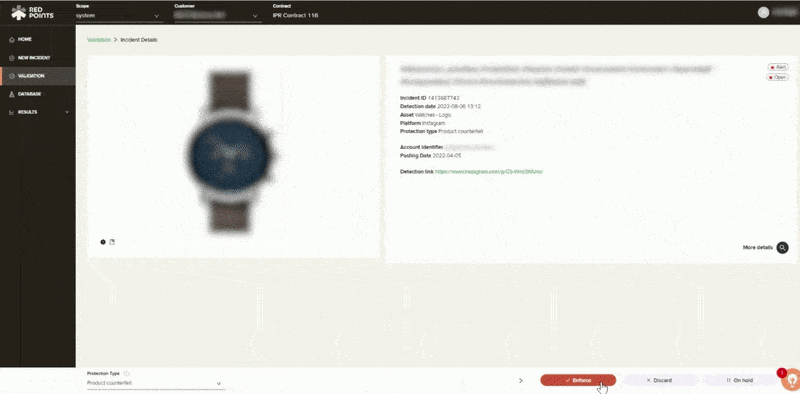
- Validate
Leveraging our image recognition technology, you will then have the opportunity to filter through thousands of potential infringements with efficiency. As you filter you can identify cases that you may pursue and find what you want to remove. This process can be done manually or you can run it automatically based on rules that you set up within our platform.
- Remove
Then you can start removing any impersonation content that may be putting your brand or your customers at risk. This will provide you with real-time protection against impersonators targeting your brand. You will also have access to detailed dashboards and reports to keep track of the results of your impersonation removal strategy, all within our platform to ensure that you continue to protect your brand from scammers.
What’s next
If you are proactive in the way you approach brand impersonation you will give yourself the best opportunity to defend your brand from bad actors. Every day impersonators are finding new ways to deceive consumers and businesses. You have to be prepared to react quickly and robustly.
An automated impersonation removal solution is the best tool you can use to tackle these issues. While manual methods will help you if you are dealing with low-level, small-scale impersonation, such methods quickly become impractical and expensive.
With automation, you can detect, monitor, and take down thousands of brand impersonators every day. Additionally, by working alongside experienced experts you will be able to design a brand protection strategy that safeguards your business in the long term too.
To learn about how we can help you protect your business from brand impersonation online, request a demo here.