Table of Contents:
Last updated on: January 5, 2024
Imagine one of your customers clicking on what they believe is the familiar link to your online store, but upon arrival, everything seems slightly off. Despite the odd feeling, they proceed to browse, add items to their cart, and checkout. Days pass, and not only do their items not arrive, but their credit card statement reveals a series of unauthorized transactions. They’ve fallen prey to a homograph attack while interacting with what they thought was your business.
This incident isn’t just a one-off mishap; it’s a growing concern for businesses everywhere. Homograph attacks, with their subtle character replacements and exploitation of multi-lingual domains, pose a significant threat to both the security of your business and the integrity of customer data. As businesses increasingly operate online, understanding and mitigating the risks of such sophisticated attacks is essential.
In this article, we’ll go in-depth on homograph attacks to uncover how they work and what businesses can do to navigate the digital landscape safely.
Summary:

Think of homograph attacks as the doppelgangers of the domain name world.
Officially, homograph attacks are deceptive tactics that use visually similar but technically distinct characters to register a malicious domain name. Usually, the replicated domain names belong to popular companies with an outstanding track record and thousands, if not millions, of loyal customers.
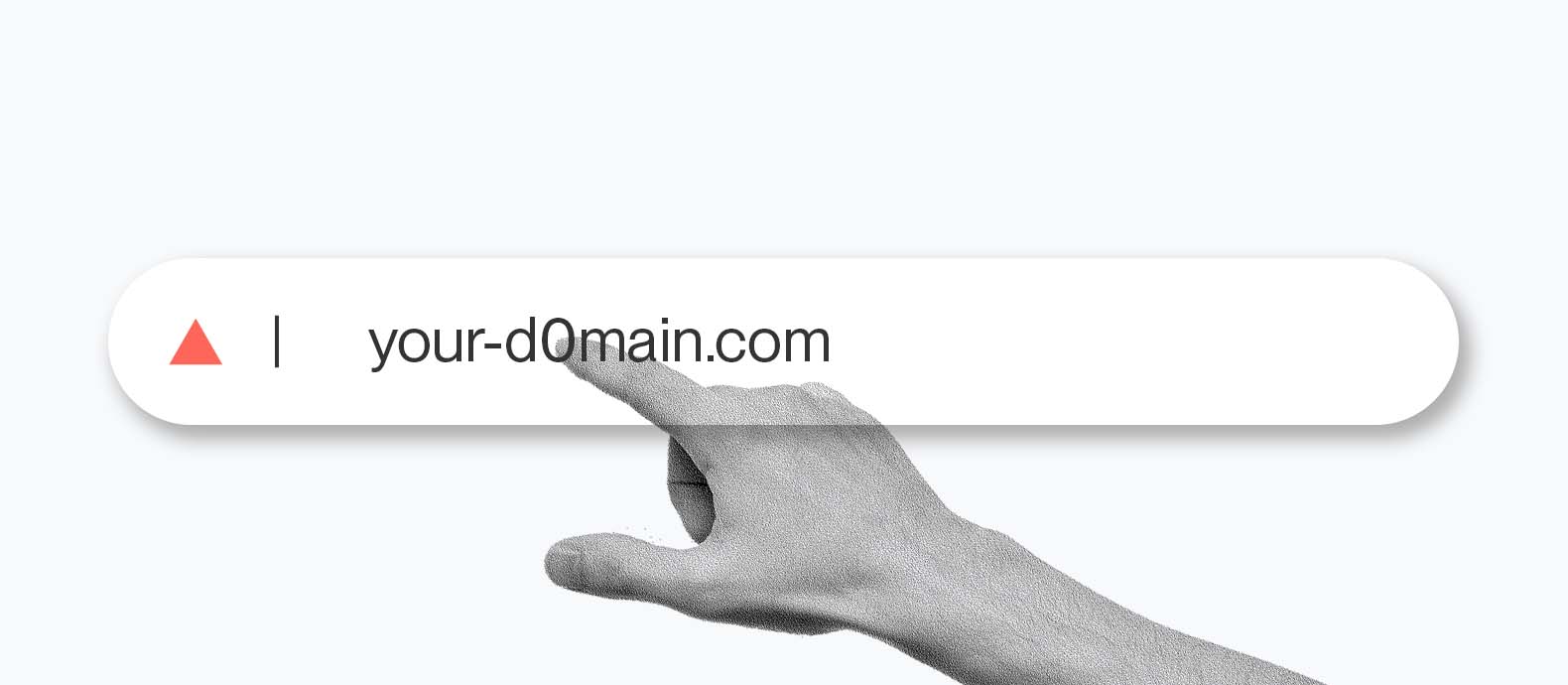
An example of a homograph attack is when a bad actor swaps out the Latin “a” in adidas.com for a Cyrillic “a,” which looks the same. In an email or a hyperlink, the unfortunate victim could not tell the difference. This small change creates a visual replica of the original website.
From here, the spoofed website entices the victim into interacting with the website and providing access to sensitive information or their computer without knowing.
A homograph attack is not to be confused with typosquatting.
The latter is a form of URL hijacking where customers register domain names conscious of misspellings or typos of popular websites. An example of a standard typographical error could be “gogle.com” for “google.com”.
There are many reasons why bad actors would typo squat domain: malware, phishing, or redirecting traffic are all common reasons.
At the base level, homograph attacks use similar characters to fool victims. Homograph attacks begin by finding characters that look very similar across scripts. Latin, Greek, and Cyrillic are all common source scripts.
Internationalized Domain Names (IDNs) and Punycode encoding are then leveraged to include non-Latin characters in the domain name, opening the door for global inclusivity but also abuse by homograph attacks.
Before these two features, domain names were limited to the 26 letters of the Latin alphabet, 10 digits, and a few symbols. This introduced a significant barrier for non-English speaking users, so IDns were introduced to allow domain names in local languages and scripts through Punycode.
Punycode translates local languages into ASCII-compatible encoding. For example, the Unicode domain “中国” (China in Chinese) is represented in Punycode as “xn--fiqz9s”.
The translation adds an extra layer of vulnerability for users looking to access international domains translated in Punycode.
By leveraging this technology to create a deceptive domain name, bad actors can create legitimate URLs.
Homograph attacks also negatively impact the replicated businesses. These deceptive tactics can lead customers to question the authenticity and security of the brand and may drive them to take their businesses elsewhere. If left unattended, this slow erosion of consumer trust can have long-term effects on customer relationships and profitability.
Phishing attacks could directly target businesses as well. Employees should take great care to scrutinize the websites they access on their work network carefully. Malicious actors could come in and download sensitive customer information or upload malware that shuts down the entire operation.
On average, a data breach of this caliber costs an organization over $4 million to fix. For example, the Sony Cyber Attack of 2014 led to data leaks and operational disruption that cost the industry leader over $100 million to resolve. Though the attack utilized malware on their systems, official records found that initial access was gained through phishing emails opened by employees.
The $100 million bill does not include the unquantifiable yet significant impact on consumer trust. These attacks severely undermine consumer confidence and emphasize the need for more robust cybersecurity measures and public awareness from all companies.
Having a set protocol for identifying homograph attacks is a necessary security measure to protect personal and business data and maintain customer trust. While the following sections are geared primarily towards businesses, the regular consumer can still learn and apply the points we mention on identifying homograph attacks.
Common red flags of homograph attacks include suspicious domain names, links from unsolicited emails, inconsistent website design, and unusual request patterns. While not guaranteeing a homograph attack, these red flags are usually signs of a fake website created to solicit sensitive information or urge victims to take immediate action.
Of these red flags, perhaps slight variations in a domain name are most telling. As we mentioned before, characters from different scripts appear visually identical but will have different ASCII codes. If you spot a link and the font style seems slightly off, staying safe is better than being sorry.
That said, you don’t have to examine every domain name before you click on them manually; software and browser features exist to add an extra security layer against homograph attacks.
Modern browsers can display the Punycode form of a domain name, and third-party anti-phishing tools are often used to detect and warn users about potentially dangerous websites.
For businesses, cybersecurity teams play a crucial role in continuously monitoring network traffic and domain name system (DNS) requests. They can create incident reports, respond to vulnerabilities, and develop policies to improve your organization’s web security.
On top of that, cyber security teams can hold regular training for employees to help them recognize and respond to suspicious emails and websites, especially when they are on a secure company network. After all, your security protocol is only as strong as your weakest link.
Preventing and mitigating homograph attacks requires a multi-faceted approach that blends proactive strategies and prompt responses. Businesses should take extra care of their customer’s data, so here’s what they can do to tackle this challenge:
Defensive domain registration
Registering variations of your domain name, including common misspellings and potential homograph representations. This prevents bad actors from registering those domains and using them to phish for sensitive information or redirect traffic to a competitor’s website.
Advanced email filtering and security
Implementing email security solutions can detect and filter out phishing emails before employees even have the option to open them. Email authentication technologies like Domain-based Message (DMARC), Sender Policy Framework (SPF), and DomainKeys Identified Mail (DKIM) prevent spoofing and verify email authenticity before they reach your inbox.
Web browser configuration
You can configure your web browser, corporate or not, to show the Punycode version of internationalized domain names, making it easier to spot homograph attacks.
Brand protection services
Third-party brand protection services exist to protect intellectual property and your brand’s identity. These services monitor for domain squatting, conduct periodic security audits, and implement resolution processes to cancel or recover domains.
Prevention can only go so far. Occasionally, mistakes can be made. No matter how careful employees or your cybersecurity team are, attackers consistently find new ways to get around the system. When this happens, it’s important to act promptly and carefully.
Do not interact: If you believe the website you’re accessing is fraudulent, stop interacting. Don’t enter more information, click links, or download files. Get out as soon as possible.
Scan for viruses: If you’ve accessed a website you believe could be dangerous, run a full virus scan on your system to check for any infiltrations. Ensure that your antivirus and anti-malware software are up to date.
Documentation: Make sure to document everything – from how the website was found to every step of the interaction. Create a detailed account of events and submit a report to the cybersecurity team.
Step-by-step policies like these highlight the need for comprehensive cybersecurity policies. Regular awareness and protocol training are necessary to help employees recognize and respond to phishing attempts. Strong authentication measures add an extra layer of security, and security updates ensure that all systems receive the latest security measures.
That said, companies often underestimate the role of legal action and domain takedown services in taking down fraudulent domains. These services have been highly effective in addressing and resolving threats to businesses. With the help of these services, companies become capable of enforcing takedown actions, monitoring domains, and building on consumer trust.
Every business that relies on a website to generate sales should have some form of domain management process. As your business grows, the risk of being targeted grows as well. Using a Domain Takedown Service like Red Points’ ensures that you can do what you do best and that we’ll protect you every step of the way.
Here’s what you can expect:
Homograph attacks pose a unique and sophisticated threat to businesses. As seen in the case of Sony, these attacks strike at the core of brand integrity and customer trust, so understanding the nuances of homograph attacks is crucial for businesses to safeguard their online presence.
In most cases, leaving it to the professionals would be the best option; services like Red Points offer peace of mind and take a proactive stance in defending your digital assets.
If you’re considering the protective umbrella of a domain takedown service, we highly recommend exploring what Red Points offers. Request a demo today and see firsthand how our services can align with your needs.