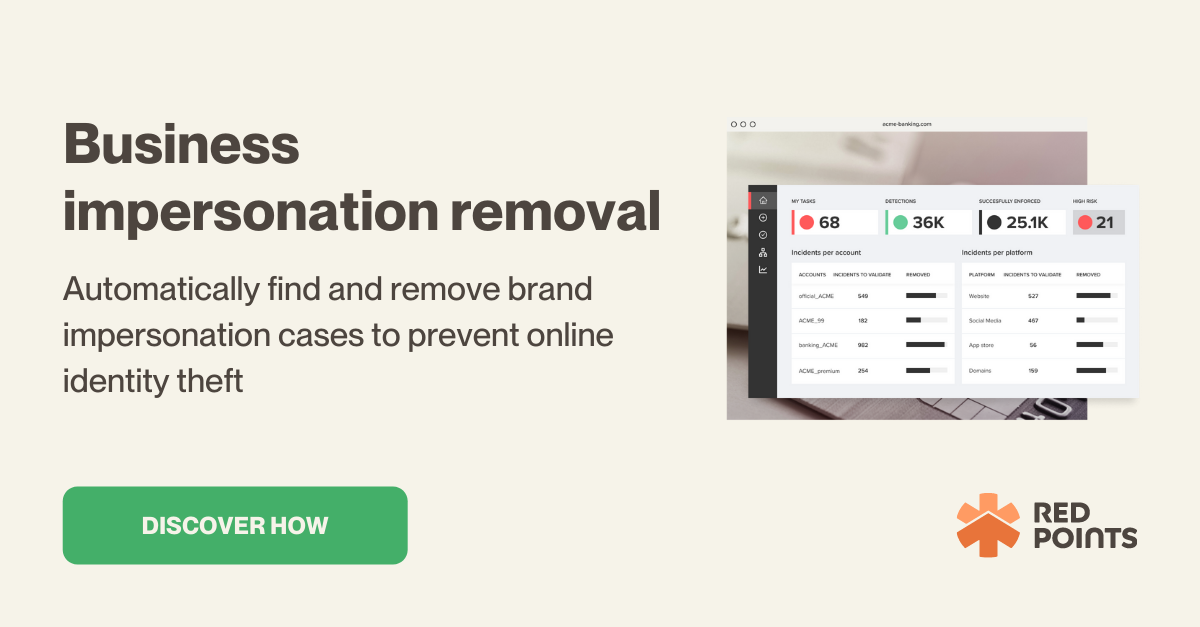
Protecting your business goes far beyond ensuring your merchandise and services are secure. Our current digital age has created an easy opportunity for online scammers to take advantage of your brand. Keep reading to learn more about business impersonation and how you can protect yourself from someone impersonating your company.
What is company impersonation?
Business impersonation is the practice of using an existing brand’s name, content, products, and other intellectual property to scam consumers. There are many different ways a brand’s identity can be impersonated, and these scams can greatly impact your business.
The impact of impersonation on brands
It may seem like consumers are the main victims of brand impersonation, but that’s not the case. The Federal Trade Commission states on their site that “your company has a lot to lose” from brand impersonation (Cyber Security for Small Business).
A brand’s image is more important than ever, and your business reputation can be destroyed by impersonators. Scammers can pretend to be your company and send out faulty products, take advantage of your would-be customers, and create distrust with your brand. Any of these occurrences can cost you brand deals and partnerships, loyal customers, and sales.
Business impersonation attack examples
Brand protection can be difficult when there are so many forms of business impersonation a scammer can take advantage of. Here are the top impersonation attack examples your business should be protected against:
Domain spoofing
Domain spoofing is the impersonation of a business by using its domain to scam consumers and/or employees of the business. There are two main ways scammers can impersonate a company through domain spoofing: cybersquatting and typosquatting.
- Cybersquatting: Scammers use cybersquatting to claim domain names of already-existing businesses. They can set up websites with that business’s branded content and sell counterfeit products, stealing would-be customers and sales. Cybersquatting can also be used to sell the domain back to a legitimate business for a large markup.
- Typosquatting: Scammers use typosquatting by registering a domain name extremely close to an existing business website. When a consumer accidentally misspells a domain name, they can end up on these sites. Scammers can copy the original site and consumers may never know they ended up on a counterfeit site.
Fake social media accounts
Creating a fake website is fairly simple, but making a fake social media account to impersonate your company is even easier for a scammer. Social media impersonation on platforms like Instagram and Facebook is a growing problem for businesses. Fake social media accounts can be used to scam consumers out of sensitive information, sell counterfeit products, and more.
Fake mobile applications
Fake apps resemble existing brands and websites, all with the goal of getting consumers to download the app. They may profit off consumers by charging a fee for the fake app or selling counterfeit products its interface.
What to do for business impersonation protection
Impersonating a company is illegal, which is good news for legitimate businesses. If a scammer is impersonating your business, there are steps you can take to get them to shut down.
Detection
By the time a consumer alerts you to someone impersonating your business, the damage has already been done. Early detection is one of the most important steps of brand protection against these scammers.
Ensure you have a process set up to detect suspicious activities on social media, search engines, app stores, and domain names. Investing in a brand protection service is a surefire way to ensure you will immediately be alerted to company impersonators.
Enforcement
Time is of the essence to take action when you find accounts or websites impersonating your business. Malicious accounts or websites can damage your brand image in a single day if they aren’t dealt with. For detailed guides on how to take down different types of company impersonation, head over to these articles:
- How to report a fake Facebook business page
- How to report an impersonation account on Instagram
- How to report a Twitter account for impersonation
- How to take down a fake website: full guide to protect your brand
What’s next
With all the chances scammers have to impersonate your business, brand protection can be a full-time job. You likely don’t have the time, technology, or capacity to ensure your business is protected from impersonation the way it should be. This is where a brand protection service like Red Points is vital. There’s no way you or any number of employees can search for scammers 24/7, but this software can!
Bots scan and keep a constant lookout for business impersonation across search engines, social media accounts, and app stores. The speed and rate of successful takedowns for these impersonators help prevent scammers from further attacks. Best of all, Red Points offers a flat monthly fee for full identity protection. This means no jumping through hoops or paying extra when an impersonator needs to be taken down.
Visit Red Points to learn more about our business impersonation removal solution, and how we can address your unique business needs.